While fake Flash updates that push malware have traditionally been easy to spot and avoid, a new campaign has employed new tricks that stealthily download cryptocurrency miners on Windows systems.
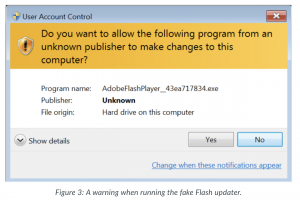
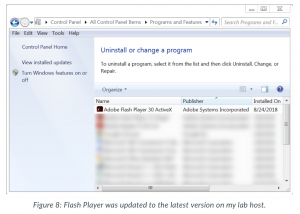
To the average user, the newly discovered samples, which have been active as early as August, seem legitimate. The samples act as Flash updates, borrowing pop-up notifications from the official Adobe installer, and even actually updating a victim’s Flash Player to the latest version.
Unbeknownst to the victims, while the legitimate Flash update has occurred, a tricky XMRig cryptocurrency miner is quietly downloaded and runs in the background of the infected Windows computers.
“A recent type of fake Flash update has implemented additional deception,” said Brad Duncan Threat Intelligence Analyst with Palo Alto Networks’ Unit 42 group, in a post about the new campaign Thursday. “As early as August 2018, some samples impersonating Flash updates have borrowed pop-up notifications from the official Adobe installer. These fake Flash updates install unwanted programs like an XMRig cryptocurrency miner, but this malware can also update a victim’s Flash Player to the latest version.”
While searching for fake Flash updates, researchers noticed Windows executable file names starting with AdobeFlashPlayer, from non-Adobe, cloud-based web servers. The downloads always contain the string “flashplayer_down.php?clickid=” in the URL.
Duncan said he could not determine how potential victims were arriving at the URLs delivering the fake Flash updates, however.
Network traffic during the infection process consists mainly of the Flash update. Interestingly, the infected Windows host generate an HTTP POST request to [osdsoft[.]com], a domain associated with updaters or installers pushing cryptocurrency miners.
But, the research team noticed that their infected systems soon generated traffic associated with the XMRig cryptocurrency mining over TCP port 14444 – as the malicious cryptominer began to take sway and utilize the systems’ power for mining.
While the Adobe pop-up and update features make the fake installer seem more legitimate, potential victims will still receive warning signs about running downloaded files on their Windows computer, said Duncan.
“This campaign uses legitimate activity to hide distribution of cryptocurrency miners and other unwanted programs,” the research team said. “Organizations with decent web filtering and educated users have a much lower risk of infection by these fake updates.