SINT MAARTEN—Curious just how susceptible some of the more vulnerable IoT devices are, a researcher set up a series of honeypots at his friends’ houses to record traffic, exploit attempts and other statistics.
Dan Demeter, a junior security researcher with Kaspersky Lab’s Global Research and Analysis Team (GReAT), reviewed two years of honeypot history in a talk at the company’s Security Analyst Summit last Tuesday.
“Our idea was to run honeypots in people’s houses, some of my friends accepted, some of my friends didn’t,” Demeter said of the project, which he carried under the guidance of GReAT Director Costin Raiu. Demeter said the devices, mostly faulty routers, didn’t affect the users’ internet activity, they just silently recorded pings.
After planting vulnerable devices, mostly in the UK and his native Romania, Demeter was able to register 200 malicious or abusive IP addresses and almost 13 million hits from his honeypots.
For his project Demeter gleaned traffic from ISPs and networks mostly in Romania, such as RDS and RCS, Telekom Romania, and UPC Romania. In the U.K., he looked at traffic from BskyB-broadband-as, GB – AS5607.
Demeter saw attackers attempt to carry out a variety of exploits – new and old – but broke down three of the more common ones in his talk.
Many attacks tried to leverage an older vulnerability in the embedded webserver RomPager in order to change DNS server settings. Attackers also used the vector to carry out clickjacking attacks, Demeter said, hoping to redirect users a variety of phony sites, some mimicking Netflix, some urging users to invest in a new cryptocurrency called Fargocoin.
Researchers with Check Point publicized the RomPager vulnerability, a cookie vulnerability that affected 12 million devices they dubbed Misfortune Cookie, mostly routers, in 2014.
“The fact that I still see RomPager exploits in a honeypot in 2017 means that there are still vulnerable routers out there,” Demeter told the crowd, “I think this trend will not go away, these attacks are almost four years old and I think they’re going to be around for a long time.”
Demeter also saw attacks trying to execute commands via another vulnerability from 2014, ShellShock, and perhaps more interesting–especially given the freshness of the vulnerability–leverage last month’s Apache Struts 2 exploit.
Attackers were quick to incorporate the Struts 2 vulnerability, Demeter said. The flaw was patched after it was disclosed by Cisco’s Talos on March 8 but it only took one day for Demeter’s honeypot to observe a hit trying to exploit the vulnerability. Before all was said and done, he saw 10,000 hits trying to exploit the Struts 2 flaw.
Demeter showed a sample of one request that emanated from a server in China and described how it was trying to search for a content type header to exploit. Embedded IoT devices don’t run Apache Struts by nature so none of Demeter’s devices were at risk but that didn’t stop the researcher from being fascinated with how quickly the vulnerability was recruited.
 One of Demeter’s more interesting observations from the project came when attackers changed their behavior to adapt to his honeypots.
One of Demeter’s more interesting observations from the project came when attackers changed their behavior to adapt to his honeypots.
The researcher’s honeypots collected logs that are processed in a machine; another machine, meanwhile, fetched links and samples in a sandbox environment. One day Demeter observed that attackers were beginning to use FTP to echo commands in a file.
“I was like ‘Oh my god, my honeypot doesn’t know how to handle FTP connections,'” Demeter said, “I found that pretty interesting because they changed their behavior, they adopted a new tactic because they realized that our honeypots were capable of automatically extracting the files.”
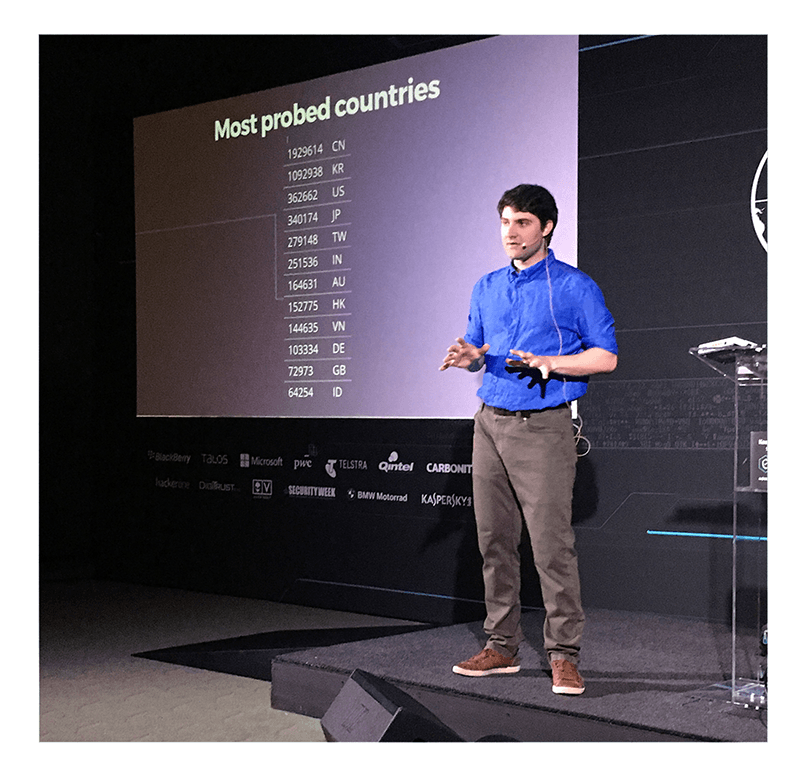
The researcher took a moment near the end of his talk to drill down on the botnet’s details further and tabulated which countries were the most probed. Southeast Asian countries like China and South Korea, perhaps not surprising, were the most active, with over one million pings each. The United States and Japan came in third and fourth with 360,000 and 340,000 respectively.
“As more and more devices are added to the network the vulnerability, the web space for attacks gets larger and larger,” Demeter said, “I think new devices that are being developed should have a thorough code review.”
Demeter began his talk by reviewing vulnerable IoT devices such as IP cameras made by Dahua and routers made by TP-Link. He also described the spate of recent, large-scale DDoS attacks, including those that affected OVH, the DNS provider Dyn, and Brian Krebs’ website. He suggested that in the grand scheme of things there may not be a huge difference between now and nearly 30 years ago, in 1988 when the Great Worm, a/k/a the Morris Worm made its way through computer systems.
“Is this really a new trend?” Demeter asked, “Back then, more and more computers were connecting to ARPANET and slowing down, there were no patches. Now experts say that by 2020, there will be 50 billion IoT devices, is there really a difference?”












