In Syria, the crackdown on political activists continues, with reports of pro-Syrians using malware that targets and spies on users attempting to use popular VOIP software Skype.
A blog post by the Electronic Frontier Foundation’s (EFF) Eva Galperin and Morgan Marquis-Boire on Wednesday describes a website claiming to offer Skype encryption. After users download and install the Skype encryption program – which is really a Trojan horse program – they open themselves up to being spied on.
The Trojan in question, DarkComet 3.3, has been used in the past to monitor Syrian rebels. It allows attackers to capture webcam activity, disable settings for anti-virus programs, record keystrokes and steal passwords – all while communicating with a remote Syrian IP address, according to the EFF.
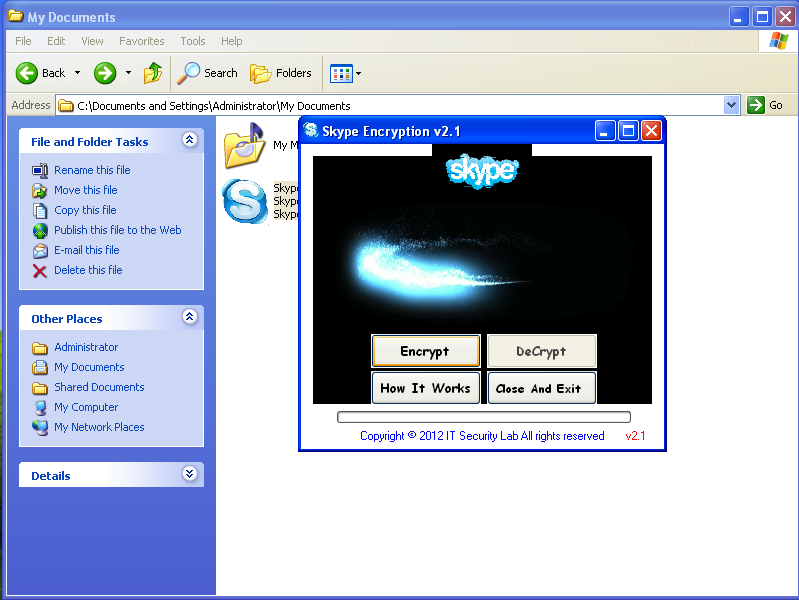
As popular and international pressure has mounted on the government of Bashar al-Assad, his government has increasingly turned to cyber surveillance to keep tabs on the actions and communications of political dissidents inside and outside of the country. Just this week, anti malware firm F-Secure reported on the government’s use of another Trojan, Xtreme RAT, to spy on dissidents. That malware was pushed out to its intended victims using Skype’s chat feature.
Earlier this year the EFF warned Iranian and Syrian users about targeted attacks that tricked users by emulating Adobe Flash Player updates via fake Youtube pages.









