Sometimes fighting good security is harder than embracing it. That appears to be the case with at least one company that went to great lengths to avoid insecure HTTPS browser security warnings from appearing on the thousands of sites it managed.
The company in question is ShopCity.com, a community-based business that gives brick-and-mortar retailers and municipalities a place to hang their shingles online. Recently Troy Hunt, who runs the Have I Been Pwned service, was tipped off to a unique act of security defiance.
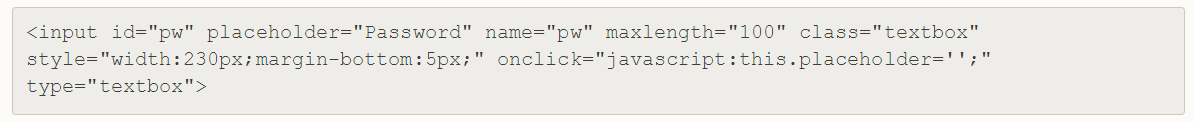
ShopCity.com was using “pseudo password fields” to avoid Google Chrome and the Firefox browser from showing “Not Secure” warnings in the URL bars of the sites it managed.
After being tipped off to ShopCity.com’s activities, Hunt did some sleuthing and found sites managed by the company were avoiding HTTPS warning error messages by displaying what amounted to fake login screens.
“Firstly, the browser warnings about an insecure login only fire when there is an input type of ‘password,'” Hunt wrote in a blog post. He points out it might look like a password field, but it is not.
“Ah, it only says ‘Password’, it’s actually just a type of ‘textbox’. There’s a single CSS class on it for some visual styling but once clicking on the field, something magical happens.” That something is a script that runs.
“And now we have a totally new class on the field. Plus, of course, the onclick event on the input box itself sets the placeholder text to an empty string. So what does the class do? It merely changes the font.
“And as you’ve probably guessed by now, that ‘font’ is nothing other than a single disc per character designed to be a visual representation of the real disc you’d normally see when entering text into a proper password field,” Hunt wrote.
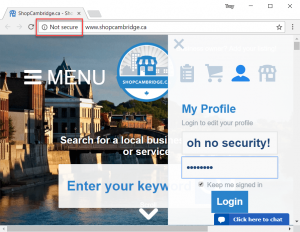 In the end, he said, “it’s a pseudo password field designed to fool the user and deny them of the browser’s visual warning designed to protect their password.”
In the end, he said, “it’s a pseudo password field designed to fool the user and deny them of the browser’s visual warning designed to protect their password.”
In Hunt’s post on the incident he said he was tipped off by a user considering becoming a ShopCity.com user. The woman told Hunt when she asked ShopCity.com about the lack of security on its sites she was told “SSL is more about Google’s monopolizing visibility of content, and less to do with security.”
HTTPS is key to securing communications between a client and server and thwarting attacks such as the so-called Great Cannon attack. HTTPS is a combination of the HyperText Transfer Protocol (HTTPS) and the Secure Socket Layer (SSL) protocol. Together, HTTPS, encrypts communication sessions between a computer’s a web browser and a web server. The absence of HTTPS leaves that connection between browser and web server vulnerable to sniffing attacks.
For Hunt, the willful ignorance against security isn’t new. He cited an incident when Oil and Gas International was so miffed at an insecure password and login warning displayed on a Firefox browser it filed a bug report demanding the warning be removed.
So, is all this effort worth keeping your HTTPS head in the sand? According ShopCity.com the answer is “no.”
Threatpost spoke to Rob Calvert, network administrator for ShopCity.com, who said he was a bit embarrassed and surprised at the attention Hunt’s critique had brought his company.
“We found out about this when Troy Hunt brought it to our attention,” Calvert said. “The problem traces back to a junior developer who created this workaround to avoid the security warning. We had no idea what he had done.”
Calvert said after Hunt’s exposure, now all sites on ShopCity.com’s platform are displaying the insecure browser warning at the password login screen. He emphasized that only user login’s were insecure and that any transactions conducted with merchants online were facilitated through a PayPal shopping cart that uses HTTPS.
“I agree. It’s absurd to work so hard at making it seem these sites are secure when just using HTTPS is so much easier and safer for users,” Calvert said. “We are currently transitioning our users to HTTPS and we’ll be 100 percent there by the new year.”