A new variant of the the NetWire remote access trojan (RAT) is hitching a ride on IRS-themed phishing ploys targeting taxpayers in hopes of snatching victims’ credentials and tax information.
The recently uncovered campaign reveals the RAT’s operators swapping up infection tactics to use a legacy Microsoft Excel 4.0 Macro, helping them sidestep detection and analysis efforts. The NetWire variant’s payload has also been given a facelift, with improved keylogger and credential-collecting features.
“In this new variant, I noticed that it has improved its feature that collects credentials from the victim’s system,” said Xiaopeng Zhang, with Fortinet in a Tuesday analsysis. “It also fixed some bugs in the keylogger, which were wrongly recorded Esc as Ctrl in previous versions.”
NetWire has been spreading widely over the past few years, focused on stealing credential information, logging keystrokes and stealing hardware information. This latest campaign extends these capabilities by targeting taxpayers (many of whom are in the midst of the extended tax deadline) specifically, aiming to capture their screens as they fill out tax forms, check their online bank accounts, or write private emails, Zhang warned.
The malspam emails purport to contain an important Internal Revenue service (IRS) letter about 1040 and W2 U.S. tax forms. The emails come with an OLE (Object Linking and Embedding) format Excel file attachment, named “1040 W2 IRS letter.xls.” When the victim clicks on the attachment, a Microsoft Excel sheet opens, which shows some obfuscated IRS forms in the background, with an aim to make the file appear legitimate. Victims are asked to click the “Enable Content” button to show the clear forms – which instead enables the malicious Excel 4.0 Macro to be executed.
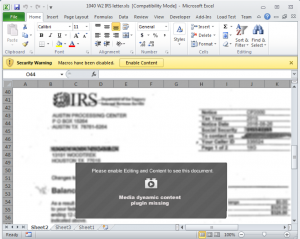 Excel 4.0 Macros has been used previously in other malware campaigns – but this is a first for NetWire, said Zhang. Excel 4.0, released in 1992, is an attractive option for cybercriminals because Microsoft also never provided a debugging feature for Excel 4.0 Macro, creating a roadblock for security analysts trying to examine complex Excel 4.0 Macro code. It can also bypass most antivirus detection: “Probably due to the technology [being] very old (28 years by now) and rarely being used in nowadays, most antivirus engines don’t detect it and treat Excel files with a malicious Excel 4.0 Macro as clean,” said Zhang.
Excel 4.0 Macros has been used previously in other malware campaigns – but this is a first for NetWire, said Zhang. Excel 4.0, released in 1992, is an attractive option for cybercriminals because Microsoft also never provided a debugging feature for Excel 4.0 Macro, creating a roadblock for security analysts trying to examine complex Excel 4.0 Macro code. It can also bypass most antivirus detection: “Probably due to the technology [being] very old (28 years by now) and rarely being used in nowadays, most antivirus engines don’t detect it and treat Excel files with a malicious Excel 4.0 Macro as clean,” said Zhang.
Once executed, the Excel 4.0 Macro starts an extensive chain of download: First, the program “powershell.exe” is executed, which then triggers the download of an MSI file, which is an installation package file used by Windows to install software, frequently chosen by attackers to spread malware as it easily bypasses many antivirus services. The MSI file (“unmodifiedness.msi”) downloads an EXE file, then which acts as a malware loader that begins to download malicious code string onto the system – one of which eventually executes an encrypted bin file from its download server. That bin file is decrypted to then execute the payload of a new NetWire variant.
Going through the code of the payload, Zhang said the structure is “very simple and clear:” It includes functions to implement a keylogger feature, connect to the Command and Control (C2) server, and handle control commands. After download, the NetWire payload implements the keylogger, and sends the command and control (C2) server various data on the victim’s login user, the computer name, as well as screenshots of the victim’s screen.
Zhang noted that the payload feature that collects credentials from the victim’s system in the sub-function of handling certain commands (0D3/0D4) has been improved, as researchers believe this most recent campaign aims to swipe taxpayer credentials and bank numbers: “We now know that NetWire is able to capture the victim’s screen and record keyboard inputs when they are, for example, filling out tax forms, checking their online bank account, writing private emails, and so on,” said Zhang.
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.











