A temporary patch has been released to address a zero-day vulnerability in Adobe Reader that could enable bad actors to steal victims’ hashed password values, known as “NTLM hashes.”
0patch on Monday released a micropatch for the flaw, found in Adobe Reader DC. The vulnerability, which has no official fix yet, allows a PDF document to automatically send a server message block (SMB) request to an attacker’s server as soon as the document is opened. SMB protocols enable an application or user of an application to access files on a remote server. Embedded in these SMB requests are NTLM hashes (NTLM is short for NT LAN Manager).
“This vulnerability… allows a remote attacker to steal user’s NTLM hash included in the SMB request,” said Mitja Kolsek with 0patch in a Monday post. “It also allows a document to ‘phone home’, i.e., to let the sender know that the user has viewed the document. Obviously, neither of these is desirable.”
Kolsek said that the latest version of Adobe Reader DC (2019.010.20069) is definitely impacted, but “older versions are likely in the same boat too.”
Security researcher Alex Inführ first disclosed the vulnerability and a proof of concept exploit in a Jan. 26 blog post.
A short write up about a PDF callback request, which can also be used steal NTMLv2 hashes https://t.co/UcA30XRNi1
— alex (@insertScript) January 26, 2019
The vulnerability is similar to a previously-discovered high-severity flaw, CVE-2018-4993, which existed in an element in malicious PDF documents that enabled automatic loading of another PDF from a remote share. This issue was patched by Adobe so that the user must click on a “security warning” box that tells them first that the document is trying to request a remote share.
This more current Adobe issue uses a similar vulnerability with similar functions.
While CVE-2018-4993 used an /F entry to load a remote file, this most current flaw (which does not yet have a CVE) exploits loading a remote XML style sheet via the SMB request.
While the user may receive a security warning if the document tries to load the XML style sheet via HTTP, no such warning occurs when using a UNC path (the type of path that denotes a resource in a shared folder), researchers said.
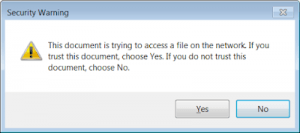
0patch’s micropatch add a security warning for loading style sheets via UNC, which like the fix for CVE-2018-4993 alerts users that the document is trying to access a file on the network.
The video below shows how the micropatch adds a security dialog to Adobe Reader.
“If the user selects ‘Yes’, the remote style sheet is loaded (whereby the SMB request delivers your NTLM hash to the remote server), and if they select ‘No,’ reader complains about not being able to load the style sheet from and empty path. Done,” according to 0patch.
An Adobe spokesperson told Threatpost that the company plans to issue a security update this week that addresses the vulnerability.
The company is approaching its monthly security updates, which take place tomorrow (Feb. 11). Adobe’s regularly scheduled update in January fixed two bugs rated important in its Adobe Digital Edition and Adobe Connect products. The two important vulnerabilities include an information-disclosure bug in Adobe’s eBook reader software program, Digital Edition; as well as a session-token exposure bug in its presentation and web conferencing software, Adobe Connect.
“Note that Adobe might issue an official fix for this issue tomorrow as they release their monthly Reader update, but if not, we’ll quickly port the micropatch to the new Reader version to keep the vulnerability patched on your computers,” Kolsek stressed.