UPDATE: This story has been updated with commentary from the company that manufactures and sells the vulnerable automated tank guages.
The gauges that detect and prevent fuel leaks at more than 5,000 gas stations in the United States are utterly vulnerable to remote attacks, according to new research conducted by HD Moore of Rapid7. The gauges are manufactured by Veeder-Root, who says it is working with its customers better enable available security features.
Automated tank gauges (ATGs), as they are called, monitor fuel levels in gas station storage tanks and trigger alarms in compliance with environmental regulations when fuel tanks are overfilled. The risk posed to these gas stations — roughly three percent of the 150,000 station in the U.S. — are serious and could enable hackers to completely shut down the stations containing the vulnerable ATGs.
“Many ATGs can be programmed and monitored through a built-in serial port, a plug-in serial port, a fax/modem, or a TCP/IP circuit board,” Moore explained on Rapid7’s Security Street blog. “In order to monitor these systems remotely, many operators use a TCP/IP card or a third-party serial port server to map the ATG serial interface to an internet-facing TCP port. The most common configuration is to map these to TCP port 10001.”
https://twitter.com/hdmoore/status/558398276932624384
Worldwide, there are 5,800 ATGs exposed on the Internet without password protection. 5,300 of those are located within the U.S. As Moore notes, a remote attacker could theoretically shut the 5,300 vulnerable stations down with little effort. Moore explains that while these systems have the capacity to turn on password protection, most operators are simply not doing so.
Attackers with access to the serial port interface, Moore claims, could spoof reported fuel levels, making tanks seem fuller than they actually are, triggering false alarms and shutting stations down in the process. They could, in theory, also do the opposite: under-report fuel levels, causing spills as tanks are then refilled beyond capacity.
More than 5,000 U.S. gas stations are vulnerable to remote hacks that could cause fuel spills and shut stations down
Tweet
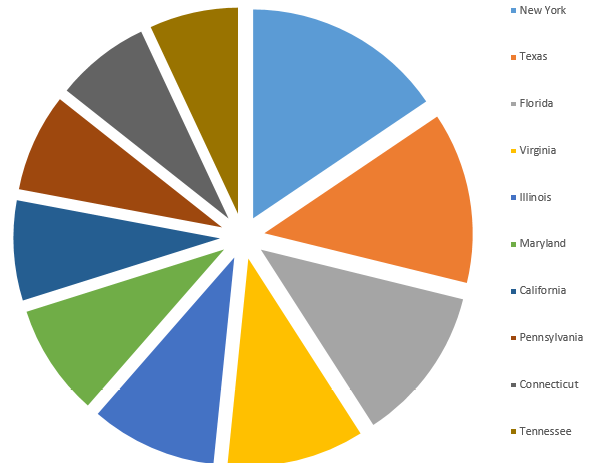
Most of the vulnerable ATGs are at gas stations in New York, Texas, Virginia, Florida, Illinois, Maryland, California, Pennsylvania, Connecticut and Tennessee.
Moore writes that “tank gauge malfunctions are considered a serious issue due to the regulatory and safety issues that may apply.”
Rapid7 uncovered these vulnerabilities by performing an Internet-wide scan of port 10001 in early January. They claim that the majority of exposed ATGs are built into retail gas stations, truck stops and convenience stores, many of which are operated by major brands.
“An unknown number of ATGs are exposed through modem access,” Moore wrote. “The majority of the ATGs appear to be manufactured by Vedeer-Root, one of the largest vendors in this space, and were identified on IP ranges associated with consumer broadband services.”
Rapid7 is not aware of any instances of these vulnerabilities being attacked in the wild, but it also acknowledges that it would be nearly impossible to differentiate between an intentional attack and an accidental malfunction.
“Operators should consider using a VPN gateway or other dedicated hardware interface to connect their ATGs with their monitoring service,” Moore said. “Less-secure alternatives including applying source IP address filters or setting a password on each serial port.”
For its part, Veeder-Root has acknowledged the vulnerability and is working with its customers to bolster the security of its products.
“Security, accuracy and reliability are top priorities at Veeder-Root,”Andrew Hider, president of Veeder-Root told Threatpost in an email. “We have taken immediate and decisive steps to inform each of our customers about activating the security features already available in their tank gauges. It is important to note that no unauthorized access of any kind have been reported by any of our customers in regard to our gauges, but we feel that any question regarding security is met with the appropriate resources to safeguard Veeder-Root customers.”
While these vulnerable systems are particularly exigent because they affect an incredibly visible part of nearly everyone’s daily lives, vulnerabilities in industrial systems are every bit as common as bugs in standard software systems.
Image via the Flickr photo stream of Philip Bunkens