The banking malware called Dorkbot is back. Samples of the 6-year-old malware are now ranked the second biggest banking malware headache in 2018 so far, according to new data from Check Point.
“Dorkbot, known malware that dates back to 2012, has entered back the top ranks, starring in the APAC [as the] top banking malware and also ranked second in the Americans, in the EMEA and globally,” wrote Check Point in its 2018 malware trends report, released Thursday.
In its heyday, Dorkbot was used by attackers to target Skype, Facebook and Twitter users. The original variant tried to con victims into downloading a malicious .Zip file with a message: “Lol is this your new profile pic?” Those who opened the .Zip attachment were locked out of their PC, roped into a botnet and their contacts were all sent the malicious .Zip and profile picture message.
The malware has evolved quite a bit over the years. Today Dorkbot is a trojan that steals a user’s credentials using web-injects that are activated as a user tries to login to their banking website, Check Point said.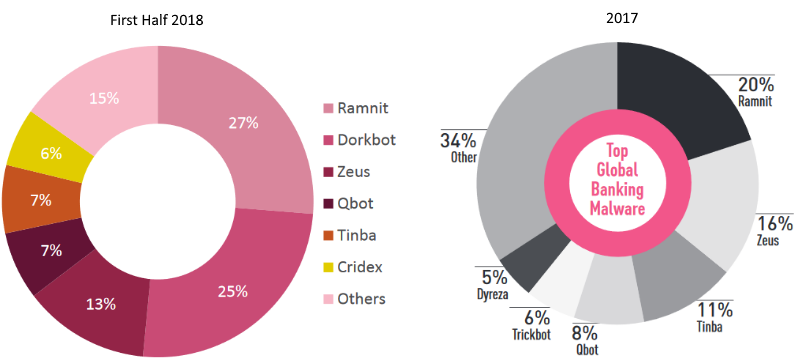
“Dorkbot, designed to allow its operators remote code execution capabilities alongside with a primary motivation to steal sensitive banking information, has been observed on last April using newly code injection technique dubbed ‘Early bird’, allowing it to avoid detection by anti-malware security products,” wrote Check Point.
Last year, Check Point reported the top banking malware threats were Ramnit (representing 20 percent of samples), Zeus (16 percent) and Tinba (11 percent). Dorkbot wasn’t even mentioned in Check Point’s 2017 analysis.
This year has seen a consolidation of the banking malware market. The top three banking malware samples comprise 65 percent of the market. For the first half of 2018 globally, Ramnit is the most prevalent (27 percent) followed by Dorkbot (25 percent) and Zeus (13 percent).
Last year the top three samples represented 47 percent of the most prevalent samples.










