As the U.S. midterm election season gets underway in earnest, concerns about the ability to hack the vote is more in the spotlight than ever. A fresh survey from Venafi has found that a full 93 percent of security pros are concerned about cyber-attacks targeting election infrastructure.
The poll, which gathered responses from 411 IT security professionals in the U.S., U.K. and Australia, found that 81 percent believe that it’s not just ballot machines themselves at risk; they fear that cybercriminals also will target election data as it is transmitted by machines, software and hardware applications, from local polling stations to central aggregation points.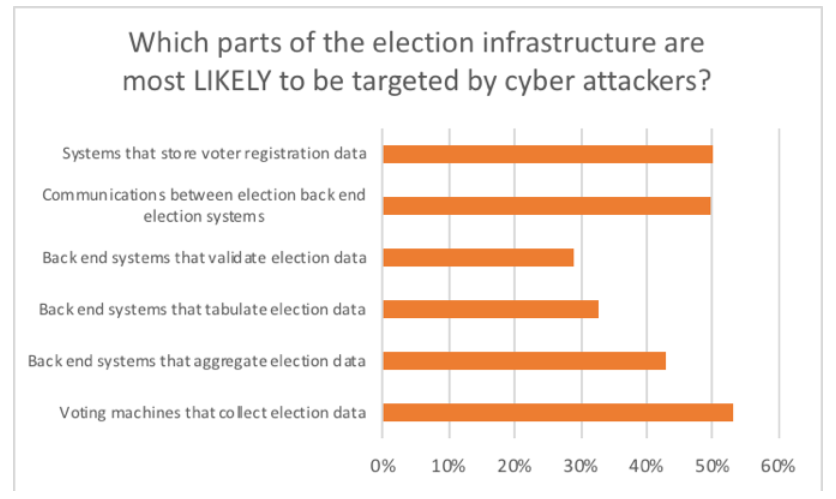
When asked what areas of election infrastructure were most vulnerable to cyber attackers, 54 percent said voting machines that collect election data; and 52 percent said encrypted communications between polling stations and back-end election systems. Half said systems that store voter registration data.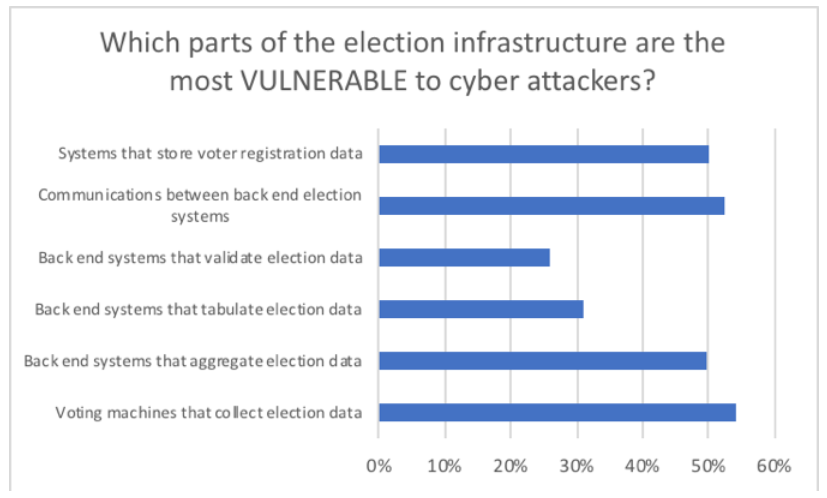
Other interesting data points include the fact that 95 percent of respondents believe election systems—including voting machines, software and back-end systems—should be considered critical infrastructure. Also, 64 percent believe vulnerabilities and exploits connected with election systems are available to cyber-attackers on the Dark Web.
Only 2 percent are “very confident” in their local, state and federal governments’ abilities to detect cyber-attacks targeting election infrastructure. In addition, only 3 percent are very confident in their local, state and federal governments’ abilities to block them.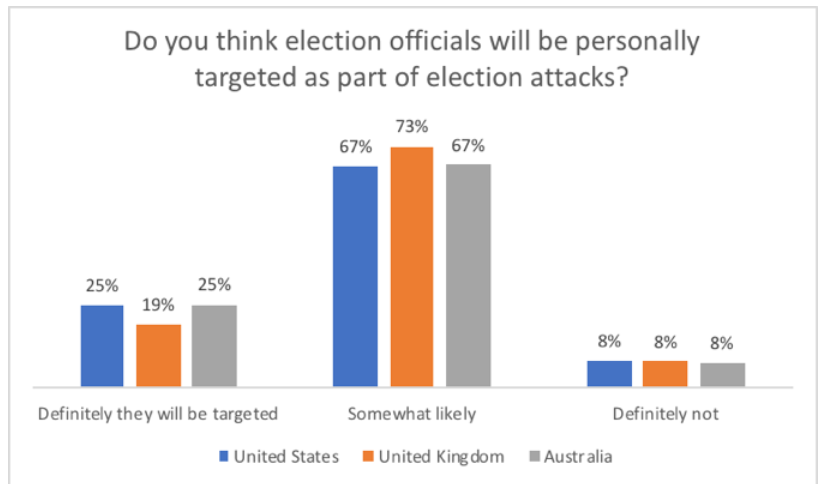
“Right now, the theater of war is information and information is in machines; all kinds of machines,” said Venafi CEO Jeff Hudson. “And many machines that used to be controlled manually are now fully automatic, so if you can control information and you can control machines, it’s this whole new theatre. And because a lot of our physical world is controlled by machines, cyberattacks can jump the gap from the digital world to the physical world and cause kinetic damage. For example, why would a nation state want to infiltrate our energy grid? I think it’s because they can use digital control of our critical infrastructure to undermine our political system and institutions.”
The survey comes as hackers were able to compromise several aspects of a simulated end-to-end election process at DEF CON 26, which just wrapped over the weekend in Las Vegas. It was the second year in a row that white-hats were able to successfully compromise voting gear.
“Last year, attendees at DEF CON managed to find and take advantage of vulnerabilities in five different voting machine types within 24 hours,” added Hudson. “While these findings were disturbing, conference attendees only examined a small portion of election infrastructure. It’s clear to nearly all security professionals that the back-end systems that transmit, aggregate, tabulate, validate and store election data are at least as vulnerable to cyberattacks as voting machines.”










