The systems that power the manufacturing, power and water plants, the oil and gas industry, and many other sectors are increasingly in the crosshairs of cyber-attackers: A full 41.2 percent of industrial control system (ICS) were attacked by malicious software at least once in the first half of 2018.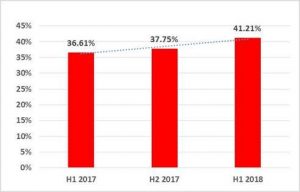
That’s according to Kaspersky Lab, which analyzed telemetry information from customers using industrial automation computers through the end of June. The data indicates a consistent rise in the percentage of attacks on this segment; the year-ago data showed the percentage of ICS computers attacked to be 36.61 percent; that then ticked upward to 37.75 percent in the second half of 2017.
The main source of infection was the internet – with 27 percent of attacks received from web sources. Another 8.4 percent arrived through removable storage media, and a surprisingly small 3.8 percent came from email clients.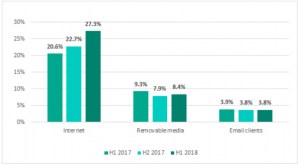
“We have observed increases in the percentage of ICS computers on which phishing emails and malicious attachments opened in online email services using the browser, as well as attempts to download malware from the internet and to access known malicious and phishing web resources, were detected,” the report noted.
The threats include cryptomining, ransomware, remote-access trojans (RAT), the VPNFilter botnet and spyware; malware was delivered via phishing mails and exploits, including for the Spectre/Meltdown class of vulnerabilities. In all, Kaspersky Lab security solutions installed on industrial automation systems detected over 19.4 thousand malware modifications from 2.8 thousand different malware families.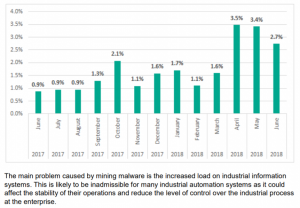
The report also found that attempts to infect ICS computers were, in most cases, random attacks rather than targeted attacks.
The countries most impacted by attacks by percentage were Vietnam (75.1 percent), Algeria (71.6 percent) and Morocco (65 percent). The safest regions for industrial machines were Denmark (14 percent), Ireland (14.4 percent) and Switzerland (15.9 percent). This follows a pattern of developing economies being disproportionately targeted by bad actors: the report noted that countries in Africa, Asia and Latin America are significantly worse off in terms of the percentage of ICS computers attacked than countries in Europe, North America and Australia.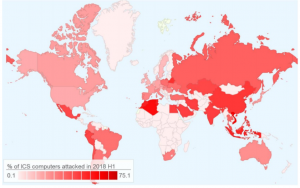
“The high percentages of ICS computers attacked in developing countries could have to do with these countries having had industrial sectors for a relatively short time only,” according to the report. “It is well-known that, when designing and commissioning industrial facilities, the main focus is often on the economic aspects of their operation and the physical safety of the industrial process, while information security is much lower on the list of priorities.”
“The percentage of cyberattacks on ICS computers is a concern,” said Kirill Kruglov, security researcher at Kaspersky Lab. “Our advice is to pay attention to systems’ security from the very beginning of their integration when the systems’ elements are first connected to the internet. Neglecting security solutions at this stage could lead to dire consequences.”
The report noted that ICS users can protect themselves by implementing well-known best practices: regularly updating operating systems, application software and security solutions on systems that are part of the enterprise’s industrial network; restricting network traffic on ports and protocols used on the edge routers and inside the organization’s operational technology (OT) networks; auditing access control for ICS components in the enterprise’s industrial network and at its boundaries; and offer dedicated cybersecurity training and support for employees as well as partners and suppliers that have access to the network.










