The average cost estimate for cleaning up a cyberattack comes in at around $1.1 million, according to a recent survey. But this is actually a rosy view: For those organizations that actually calculate (versus estimate) the real cost of an attack, that number increases significantly to $1.67 million.
According to Radware’s 2018-2019 Global Application and Network Security Report, which analyzed vendor-neutral survey data from 790 IT executives, there has been a 50 percent growth in organizations that estimate the cost of an attack to be greater than $1 million, and an overall shift away from lower estimations.
“Quantifiable monetary losses can be directly tied to the aftermath of cyberattacks in lost revenue, unexpected budget expenditures and drops in stock values,” according to the report. “Protracted repercussions are most likely to emerge as a result of negative customer experiences, damage to brand reputation and loss of customers.”
About half of the respondents said that the main impact of an attack lies in revenue-killing operational and productivity loss (54 percent), followed by negative customer experience (43 percent).
And no wonder: The majority (78 percent) of respondents hit by a cyberattack said they experienced service degradation or a complete outage (almost half, 45 percent, reported that the goal of the attacks they suffered was to cause just that). The situation is worsening, too: 68 percent last year said an attack led to service interruption.
Data leakage and information loss remain the biggest concern to more than one-third (35 percent) of businesses, followed by service outages. This dovetails with the fact that for a third of responding victims (35 percent), the goal of the attack was data theft.
While the cost of attack mitigation continues to rise, so does the number of organizations under attack. Most organizations have experienced some type of attack within the course of a year, with only 7 percent of respondents claiming not to have experienced an attack at all. A fifth (21 percent) reported daily attacks, representing a significant rise from 13 percent last year. And yet, a third (34 percent) said they don’t have a cybersecurity emergency response plan in place.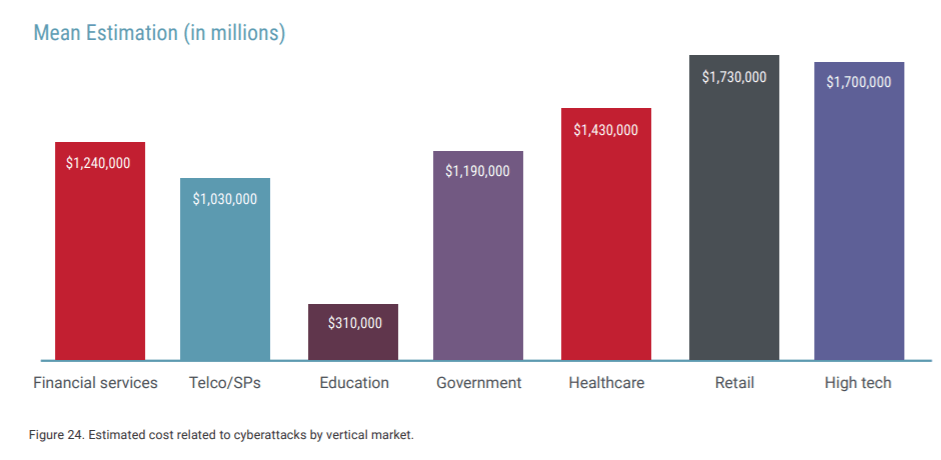
“While threat actors only have to be successful once, organizations must be successful in their attack mitigation 100 percent of the time,” said Anna Convery-Pelletier, CMO for Radware, in the report. “A cyberattack resulting in service disruption or a breach can have devastating business impacts. In either case, you are left with an erosion of trust between a brand and its constituency.”
In terms of threat scenarios, malefactors increased their usage of emerging attack vectors to bring down networks and data centers: Respondents reporting HTTPS floods grew from 28 percent to 34 percent; reports of DNS attacks grew from 33 percent to 38 percent; reports of burst attacks grew from 42 percent to 49 percent; and reports of bot attacks grew from 69 percent to 76 percent.
Application-layer attacks meanwhile still cause considerable damage. Two-thirds of respondents experienced DoS attacks against specific services, and 34 percent foresee application vulnerabilities being a major concern in the coming year. More than half (56 percent) reported making changes and updates to their public-facing applications monthly, while the rest made updates more frequently – opening the door to misconfiguration or the introduction of weaknesses.













