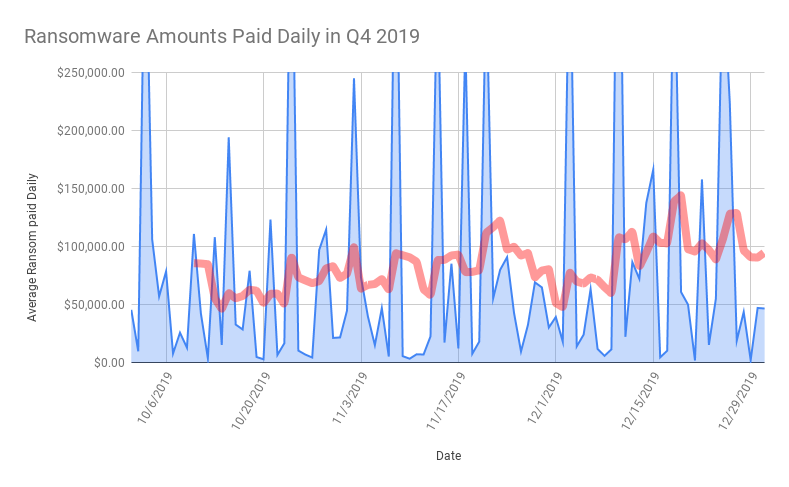
Ransomware costs more than doubled in the fourth quarter of 2019, with the average ransom payment skyrocketing to $84,116, a 104 percent surge up from $41,198 in the third quarter.
Researchers said that the leap up in ransomware costs are due in large part to some attackers pushing variants such as Ryuk and Sodinokibi harder into the lucrative enterprise space. Here criminals can attempt to extort companies with deep pockets for seven-figure ransom payouts.
“In Q4, ransomware actors also began exfiltrating data from victims and threatening its release if the ransom was not paid. In addition to remediation and containment costs, this new complication brings forth the potential costs of 3rd party claims as a result of the data breach,” said researchers with Coveware in an analysis published this week, which aggregated anonymized ransomware cases handled by Coveware’s incident response team.
Costs from ransomware attacks can vary, including the cost of a ransom payment if one is made, the cost of remediation efforts to a network and its associated hardware devices. Costs beyond the attack itself also include lost revenue from downtime and even brand damage if business interruption is severe enough.
Downtime Increases
In addition to ransom payments skyrocketing, the average downtime that a ransomware attack causes for a company also increased from 12.1 days in the third quarter of 2019 to 16.2 days in the fourth quarter.
This uptick was also linked to a higher prevalence of ransomware attacks against larger enterprises, which are often left scrambling to restore their systems for weeks. “Established enterprises have more complex networks, and restoring data via backups or decryption takes longer than restoring the network of a small business,” said researchers.
Another reason why downtime has gone up is that certain ransomware actors, like Ryuk, have evolved their attacks to make them even more pervasive, researchers said. For instance, in the fourth quarter Ryuk criminals began to use a feature called “Wake-on-LAN” that turned on devices within a compromised network that were initially powered off – so that the number of encrypted endpoints are maximized and the impact thus greatly magnified.
Working Decryptors?
Researchers found that in the fourth quarter of 2019, up to 98 percent of companies that paid the ransom actually received a working decryption tool (the same percentage as the third quarter of 2019). And, in the fourth quarter of 2019, victims who paid for a decryptor successfully decrypted 97 percent of their encrypted data (a slight increase from the previous quarter).
However, researchers warn that payment success rates do vary across different types of ransomware and different threat actor groups.
For instance, certain threat actor groups associated with Phobos and Rapid ransomware are known to consistently default after being paid. And, the most prevalent types of ransomware such as Sodinokibi and Ryuk are being distributed by more sophisticated actors, who tend to be more careful in how they handle the encryption process (thus having a lower likelihood of deploying payloads in an irresponsible manner that corrupts data beyond recovery).
“Any victim of ransomware should seek out information about the variant and threat actor before ever contemplating a payment,” researchers said.
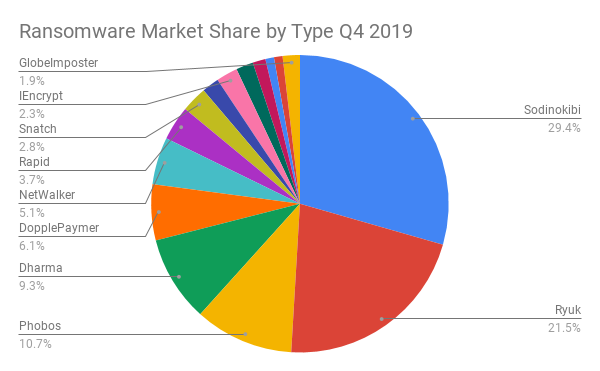
Sodinokibi Dominates
Ransomware-as-a-Service Sodinokibi was the most prevalent strain of ransomware (by incident count) in the last quarter of 2019.
Despite only being discovered in April 2019 by Cisco Talos researchers, Sodinokibi racked up several high-profile targets, including a severe New Year’s Eve attack on foreign currency-exchange giant Travelex and an early December attack on U.S. data center provider CyrusOne.
Sodinokibi is particularly dangerous because there is at least one affiliate using the ransomware that has a deep specialization in compromising monitoring and management tools used by IT managed service providers (MSPs). Once compromised, these tools can be used to push the ransomware to every endpoint managed by the MSP.
“It is not uncommon for an MSP to have hundreds of individually impacted end clients if Sodinokibi is successful in gaining persistence within the MSPs network,” said researchers. “During the quarter, Sodinokibi also changed their extortion tactics to include threatening the release of exfiltrated victim data.”
Other popular ransomware strains in the fourth quarter include Ryuk, Phobos, Dharma and DopplePaymer.
Other Takeaways
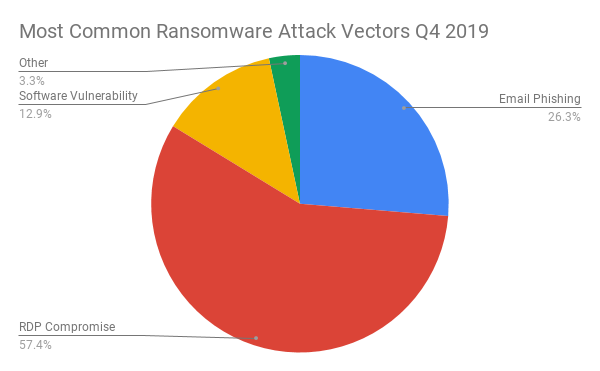
Researchers also looked at the top most common ransomware attack vectors in the fourth quarter, which were dominated by Remote Desktop Protocol (RDP) compromise (used as an initial infection vector for more than half of the attacks). Other popular attack vectors included email phishing and software vulnerabilities.
In terms of victims, professional services, healthcare, and software services were the most common industries to be targeted by ransomware in the fourth quarter, while the average size of companies targeted by ransomware were 610 employees.
These findings underscore that ransomware continues to be a growing headache for businesses. Most recently, in January, a ransomware attack reportedly caused an Arkansas-based telemarketing company to shutter its operations, leaving hundreds of employees unsure that they still had jobs days before Christmas. And earlier in 2019, 22 Texas entities – the majority of which were local governments – were hit by a ransomware attack that Texas officials called a targeted attack launched by a single threat actor.