The telecom sector is being plagued with dangerous types of malware that can lead to significant loss of confidential or regulated data, a report has found.
Lastline’s findings, published today, found that telecom sector threats are “ahead of the curve,” based on an analysis of threats to the segment over the past 30 days. In comparing the results to overall global malscape threats in all sectors, the report found that telecom over-indexes in advanced, stealthy malware that may not have been seen before; vague antivirus flags; and the volume of malicious files being used — all of which is being used to pick off email credentials from the ISP side of the house.
“There were significant differences in the trends seen in telecom services compared to the global trend,” said researchers, in the study. “Threats arriving in telecom services organizations are ahead of the curve, essentially a zero-day attack, with very few prior submissions of samples being evidenced on VirusTotal. These malspam attacks represent the tip of emerging campaigns and reflect the inherent criminal value in stolen email credentials.”
Malware with Advanced Behaviors
In the telecom sector, one in 10 malware threats displayed “advanced behaviors” — a higher level of advanced threats than the global average, which is one in 12, the report said.
These include malware with the ability to navigate its way around static analysis with the use of “packer” technology , i.e. a tool that compresses, encrypts and modifies a malicious file’s format; the ability to avoid detection by dynamic analysis systems with evasion behaviors; and compromise of a host while remaining undetected, by exhibiting stealth behaviors on the victim’s system.
“The explanation could be that the telecom services sector’s more effective security requires a more sophisticated threat to successfully breach a company’s defenses,” researchers said. “Additionally stolen telecom sector credentials play a pivotal role in many forms of cybercrime activities, and so threats with stealth behaviors play a increased role.”
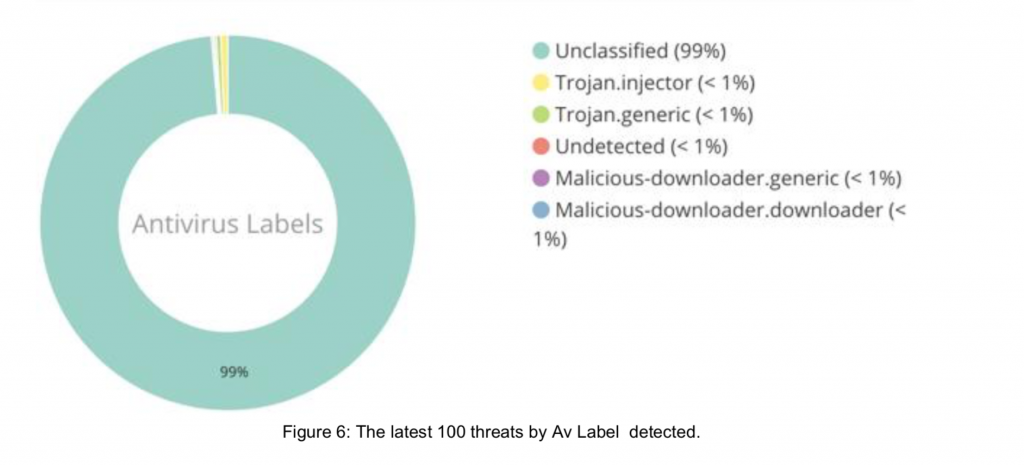
Unclassified Antivirus Labels
Of the payloads submitted to VirusTotal, the majority had only generic detections (such as “filerepmalware” and “trojan generic”), which is concerning because it is difficult to completely remediate threats and protect against subsequent attacks using stolen credentials when they have vague labeling.
This generic labeling offers no ability to adapt incident response procedures to correctly remediate the threat, researchers said.
“The typical incident-response guidance from tools that identify files with these generic descriptions is to restore the device from a known good backup or simply perform a clean re-image,” the report said. “The issue with providing generic guidance is that it does not address the very significant threat posed by malware that is designed to steal credentials, for example.”
A High Number of Malicious Files
Lastline found that the average number of malicious files that other security controls allow to infiltrate network traffic within the telecom services sector was one in every 370 submissions – a higher malicious saturation level than the average of 1 in 500 seen across the global malscape.
“The reason for this could simply be that telco service providers experience a higher malicious encounter rate than other verticals, or it could also be that higher levels of security in the telecom services sector tmore effectively pre-filter files,” researchers said.
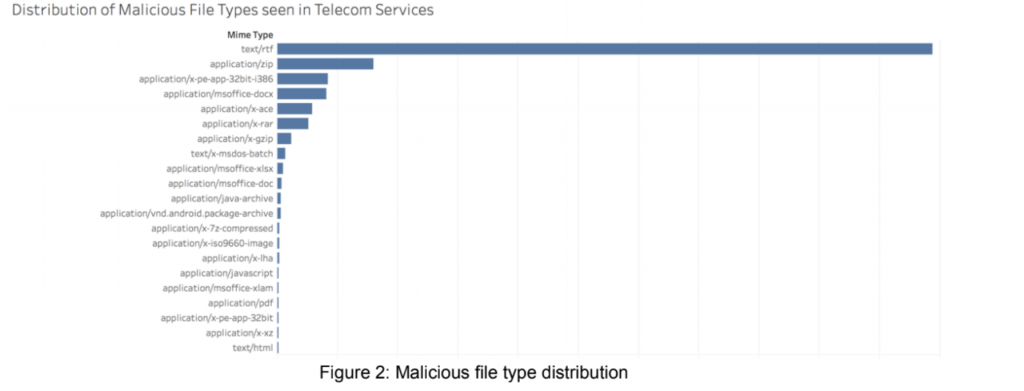
Meanwhile, only 15 file types were used to deliver malware, which is significantly lower than the global average of 40 file types.
Also, providing email services is one of the key business functions for this sector, and email-related file types such rich text format (RTF) documents dominate this sector’s encounter rate, researchers said.