As we enter into a new year full of uncertainty, one thing for cybersecurity practitioners remains true: You have a strategic advantage over adversaries. It may sound obvious to say, but they’re launching attacks against you, within your environment, which you control – giving you a fundamental defender’s advantage.
In theory.
Unfortunately though, organizations often struggle to capitalize on this fundamental advantage. So below, inspired by Mandiant’s first-ever published book, The Defender’s Advantage, are four ideas for where to start on cyber-defense activation to get the biggest bang for your security buck – in 2022, and beyond.
Establish Your Cyber-Threat Profile
“The cyber-threat profile is arguably the most important document for a cyber-intelligence program. And most programs either don’t have one or aren’t using it to drive their operations.”
– Andrew Close, Principal Consultant, Intelligence Capability Development, Mandiant
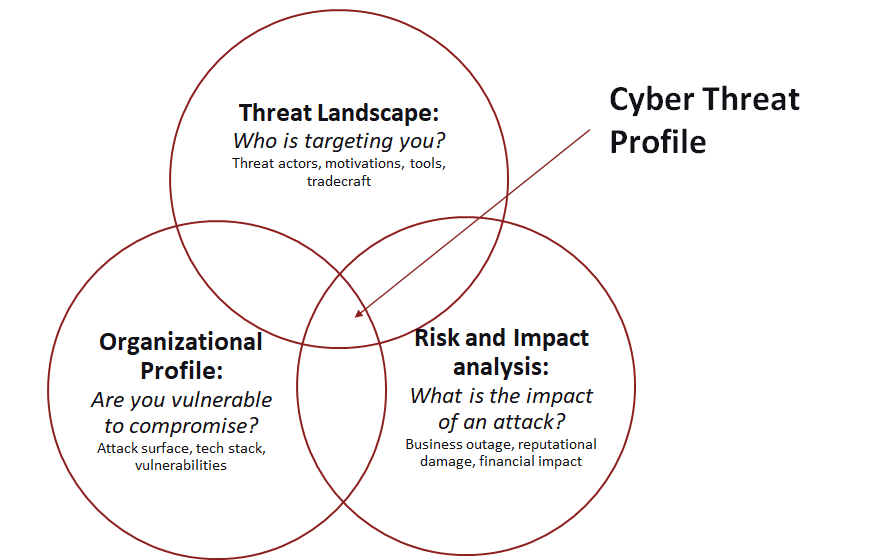
One of the most valuable steps an organization can take is to establish a cyber-threat profile, which is a deep-dive look at your organization’s adversaries, vulnerabilities and risk. The creation of a cyber-threat profile should be based on intelligence and due diligence (not headlines) and should be used to drive action for the other cyber-defense functions.
A cyber-threat profile ideally examines a combination of three key factors: the threat landscape, your organizational profile, and a risk and impact analysis.
The threat landscape information layered with a granular organizational profile can provide information on the active threat actors currently launching attack campaigns on organizations like your own. The profile should include information about your attack surface, what the attackers may be after (most-valuable data or accounts), and any known vulnerabilities along with patching status. To do this, you may need to increase the visibility you have into your environment.
The final piece of the triad is to understand the risk and impact of an attack on the business. Not all breaches are created equal, and an honest risk analysis can help focus resources on the most consequential activities.
Organize Your Environment & Operations for Battle
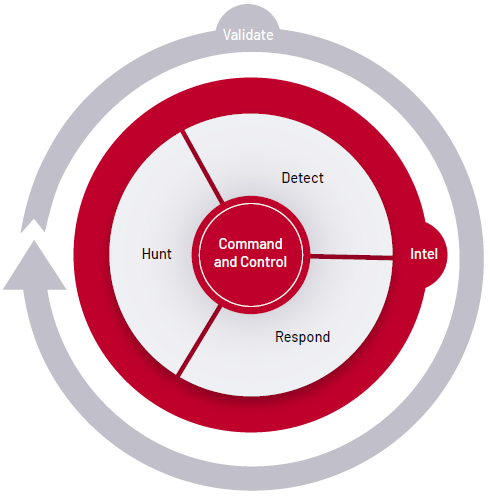
There are six critical functions of cyber-defense: intel, command and control, hunt, detect, respond and validate. With your cyber-threat profile in hand, you can use it to determine your priorities and not only prepare these cyber-defenses, but advance them to active duty. Each of the six should be established and activated based on your specific cyber-threat profile.
Considerations:
- Optimize security controls and ensure they are configured in the correct locations for visibility and action. The cyber-threat profile (the intel) will determine your organization’s crown jewels. The security architecture should then be designed to see all interactions with these crown-jewel assets and allow the security organization to respond to threats.
- Hunt for active or prior compromise based on current intelligence and knowledge of your environment. This requires close communication between the intelligence and hunt functions within a cyber-defense organization. If a compromise is detected, then a pre-established handoff with the respond function will speed investigations and allow for quicker remediation.
- Communicate effectively before, during and after a breach through a command and control function that will orchestrate cyber-defense actions and communications both internal and external to the security organization.
- Make sure to validate your capabilities (see below).
Drill, Drill, Drill to Validate Capabilities
“If your controls and processes don’t work, you want to know before the adversary does.”
– Lynn Harrington, Mandiant
A key component of activating your cyber-defenses is to confirm that the work (and investments) you have put into technologies, processes and staff are paying off. To do this, you need to continuously validate the effectiveness of controls and operations.
Using your cyber-threat profile as a guide, you can test your capabilities against active threats to your organization. This includes both external and internal threats and can be validated through automated tooling, penetration testing or cyber-range-simulated breach exercises.
Another invaluable activity to regularly perform is a tabletop exercise. These exercises should cover various attack scenarios including, but not limited to, ransomware, data exfiltration and insider threats.
Tabletop exercises should be held regularly throughout the year with both executive and technical groups. The value of these exercises is to practice incident-response procedures so that if (or rather, when) the “worst day” arrives, your organization can provide a quick and measured response. An important aspect of these exercises is to identify and practice communications with groups external to the IT security function. This can include legal counsel, insurance providers, IT functions and board communications.
A great example of the need to collaborate with groups outside of the IT security function is when mapping out a mass password reset event. This is often required after a breach and must be tightly coordinated with the IT organization. Some questions to work through: Is a mass password reset event viable? What is involved in planning and how long would it take to execute? What activities need to happen on the IT and security side of things to ensure it is successful, and that it only needs to be performed once to fully mitigate the threat?
Tabletop exercises coupled with controls validation will allow you to close vulnerabilities in your systems and operations to prevent or minimize the impact of a breach event.
Know Your Capabilities
The good news is that establishing and activating your cyber-defenses doesn’t have to happen overnight (although, the sooner the better.) Start with establishing a cyber-threat profile; that, validation of existing controls and operations, and business goals will then guide how you build out your capabilities from there.
It can be costly to acquire the necessary expertise to shore up every function, so activating your cyber-defense can include identifying opportunities to augment the expertise in your cyber-defense organization through partnerships, outsourcing and managed services, where necessary.
Remember, it may not happen overnight, but the defender’s advantage is achievable – with an intelligence-driven approach, understanding the critical functions of cyber-defense and a commitment to continuous improvement.
Kerry Matre is a senior director at Mandiant.
Enjoy additional insights from Threatpost’s Infosec Insiders community by visiting our microsite.