Researchers have discovered a campaign delivering a previously unknown backdoor they’re calling Tomiris. Analysis of the new malware suggests that we may not have heard the last from the Nobelium advanced persistent threat (APT) behind the sprawling SolarWinds supply-chain attacks of 2020.
Namely, Tomiris has a number of similarities to the Sunshuttle second-stage malware (aka GoldMax) that was distributed by Nobelium (aka DarkHalo). That’s according to a report presented at the virtual Security Analyst Summit (SAS) 2021 on Wednesday, from Kaspersky researchers Pierre Delcher and Ivan Kwiatkowski.
Nobelium also isn’t the only APT that could have links to the malware; the researchers said that the targeting of the Tomiris campaign shows a number of overlaps with Kazuar, a backdoor linked to the Turla APT, first reported by Palo Alto in 2017 (though its development goes back to 2015).
History Repeats Itself: SolarWinds Keeps Blowing
As the researchers noted, news of the SolarWinds attacks rocked the world last December.
The espionage attacks started with SolarWinds, a major U.S. IT firm, spread to its clients, and went undetected for months. The attackers, believed by some U.S. officials to be backed by Russia, spied on private companies that included cybersecurity firm FireEye, Microsoft and up to 10 federal government departments, including the Department of Homeland Security and the Treasury Department.
The Sunburst malware, aka Solorigate, was the tip of the spear in the campaign, in which adversaries were able to use SolarWinds’ Orion network management platform to infect targets. The campaign pushed Sunburst out via trojanized product updates to almost 18,000 organizations around the globe. Once Sunburst was embedded, the attackers proceeded to pick and choose which organizations to further penetrate, ultimately resulting in about 100 compromised organizations.
By the time that FireEye first discovered the campaign in December, Nobelium was believed to have already been working on it for over a year. Evidence indicates that the APT spent six months inside the Orion networks as the threat actor polished the attack.
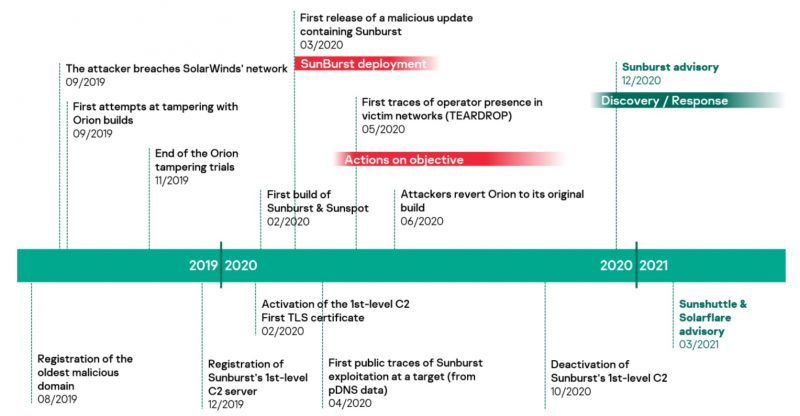
The first malicious update, which contained the Sunburst malware, was pushed to SolarWinds users in March 2020. “We can only assume that DarkHalo [Nobelium] leveraged this access to collect intelligence until the day they were discovered,” the Kaspersky researchers explained in their report, which provided the following timeline of the SolarWinds campaign:
Leaks and Family Likenesses
When it all came to light in December, Kaspersky researchers discovered two things: First, that the malware’s DNS-based protocol leaked the identity of about 100 victims who downloaded the trojanized package containing the Sunburst backdoor – victims that Nobelium planned to further exploit, including a U.S. government organization and a large U.S. telecom.
A month after that, Kaspersky uncovered similarities between Sunburst and the Kazuar backdoor, which Palo Alto linked to Turla. Turla, aka Snake, Venomous Bear, Waterbug or Uroboros, is a Russian-speaking APT known since 2014, but with roots that go back to 2004 and earlier, according to previous research from Kaspersky.
Last March, FireEye and Microsoft released more details about Sunshuttle/GoldMax. A few months later, in May, Microsoft attributed a spear-phishing attack to Nobelium, but by that time, the trail had gone cold. It looked like Nobelium had slipped under the radar: There were no major discoveries of incidents attributable to Nobelium following Sunburst.
Detecting More Glimmers From Nobelium
But in June, more than six months after Nobelium went dark, Kaspersky picked up on a DNS hijacking of multiple government zones of a CIS member state that allowed the threat actor to redirect traffic from government mail servers to machines they controlled: a feat it pulled off likely after obtaining credentials to the control panel of the victims’ registrar.
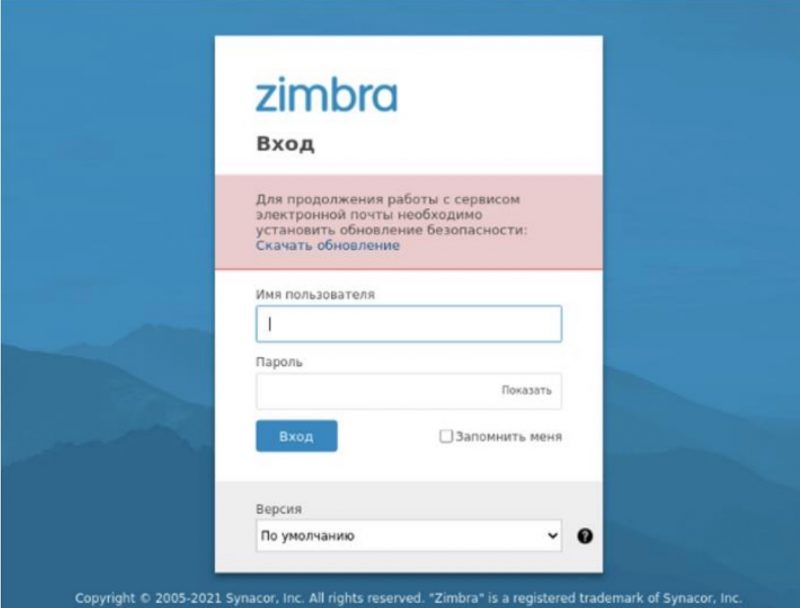
The takeover was hard to detect, Delcher and Kwiatkowski said: “While the malicious redirections were active, visitors were directed to webmail login pages that mimicked the original ones,” according to their analysis. “Due to the fact that the attackers controlled the various domain names they were hijacking, they were able to obtain legitimate SSL certificates from Let’s Encrypt for all these fake pages, making it very difficult for non-educated visitors to notice the attack – after all, they were connecting to the usual URL and landed on a secure page.”
It was all quite convincing: When targets tried to access their corporate email, they were redirected to a fake copy of its web interface, shown below. After that, they were tricked into downloading a malicious software update.
When Kaspersky researchers traced the attackers’ path, they found that the purported update was actually a previously unknown backdoor: Tomiris, a backdoor designed to establish a foothold in compromised systems that could be used to download additional, as yet unidentified malware.
Tomiris proved suspiciously similar to the Sunshuttle/GoldMax second-stage malware that was deployed by the Sunburst backdoor in the SolarWinds attacks.
This is an incomplete list of similarities Kaspersky noted between Tomiris and Sunshuttle:
- Just like Sunshuttle, Tomiris was developed in the Go programming language
- Each backdoor uses a single encryption/obfuscation scheme to encode both configurations and network traffic
- Both rely on scheduled tasks for persistence, use randomness and sleep delays to hide their activities
- The general workflow of the two programs, in particular the way features are distributed into functions, look similar enough that Kaspersky analysts suggest they could be indicative of shared development practices
- English mistakes were found in both Tomiris (‘isRunned’) and Sunshuttle (‘EXECED’ instead of ‘executed’) strings, which points to both malicious programs being created by people that do not speak English natively (It’s widely acknowledged that the Nobelium actor is Russian-speaking)
- The Tomiris backdoor was discovered in networks where other machines were infected with Kazuar – the backdoor which is known for its code overlaps with the Sunburst backdoor
‘Tell Us We’re Right/Wrong’
Kaspersky is eager for other researchers to confirm or challenge its suspicions. “None of these items, taken individually, is enough to link Tomiris and Sunshuttle with sufficient confidence,” Delcher said in a press release. “We freely admit that a number of these data points could be accidental, but still feel that taken together they at least suggest the possibility of common authorship or shared development practices.”
At the SAS conference, Delcher said that if the researchers haven’t exactly picked up on the work of the developers behind SolarWinds, they have at least spotted work from developers that share common development practices.
“All in all, it feels like we are just missing one piece of evidence to be able to wrap up all the standards together with a high degree of certainty,” he said. “It’s really starting to look like a duck and quacks like a duck, [but] in my opinion … we are not exactly there yet.”
The researchers have found clues that may indicate that the Tomiris backdoor authors might be Russian speaking. That’s not enough to make a solid link to the SolarWinds attackers, but looking at the timeline, the Tomiris campaign did in fact drop soon after the discovery of Sunburst/Solorigate, which feels significant to the researchers.
“I estimate that Tomiris development started around December 2020, right after the SolarWinds incident blew up,” Delcher said. “Right after the discovery of Solarigate, the attackers dropped this campaign and then they moved on to something new. They registered domains and then nothing happened until late January. And while they’re doing this … they might [have been] rebuilding [their] capabilities.”
Also in the press release, Kwiatkowski added that if Kasperskiy’s guess about Tomiris and Sunshuttle being connected is on target, “It would shed new light on the way threat actors rebuild capacities after being caught.
He invited others in the cybersecurity industry to weigh in: “We would like to encourage the threat intelligence community to reproduce this research and provide second opinions about the similarities we discovered between Sunshuttle and Tomiris.”
092921 14:38 UPDATE: Added comments from Pierre Delcher’s presentation at SAS 2021.
Rule #1 of Linux Security: No cybersecurity solution is viable if you don’t have the basics down. JOIN Threatpost and Linux security pros at Uptycs for a LIVE roundtable on the 4 Golden Rules of Linux Security. Your top takeaway will be a Linux roadmap to getting the basics right! REGISTER NOW and join the LIVE event on Sept. 29 at Noon EST. Joining Threatpost is Uptycs’ Ben Montour and Rishi Kant who will spell out Linux security best practices and take your most pressing questions in real time.