The role of cybersecurity defenders is usually unfair. They have disadvantages — as they have to continuously build up perimeters that protect their networks and prevent intrusions.
An attacker only needs to discover a single flaw, a small hole in the wall, and breach entire complex defenses.
How could that asymmetric interaction be changed?
Game theory helps build models to observe the interactions between attackers and defenders in complex cybersecurity incidents. When introducing strategies such as deception, defenders can level up their game. They can play the same “unfair” game that attackers play.
1. Game Theory and Cybersecurity
Game theory is a theoretical framework used to observe interactions between opposing forces. It has found its way into many fields — from economics, computer sciences, evolutionary biology, politics, law, finances, and now into cybersecurity.
Game theory has been used in cybersecurity to observe the nature of a cyber incident— where network defenders, attackers, and users, interact with each other and produce an outcome. Game theory is useful because it models each player’s behavior, their strategies, and captures the interaction between opposing players.
In this “game” interaction of opposing forces (whether teams or individuals), each force is interested in a prize, or on the contrary, to avoid loss.
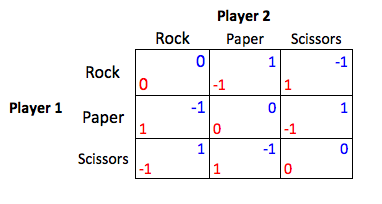
Think about rock, paper, scissors. There are two players with the same strategies. Both have 50/50 chances of winning.
Of course, unlike rock, paper, scissors in cybersecurity both players can strategize and make intelligent decisions based on their resources, to attain the rewards, while at the same time anticipating the actions from opposing players.
2. Cybersecurity is an Imbalanced Game.
“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.” – Stephane Nappo
Unfortunately in every cybersecurity encounter, network defenders are always at a constant disadvantage. Despite all the cyber-security technology, they don’t know when, where, and how the attackers will strike.
Cybersecurity is an imbalanced and unfair game setup— it favors attackers.
During cybersecurity incidents, there are three affected players, attackers, defenders, and legitimate network users. All of them have different reasons and motivations for succeeding. First, there are the attackers that lead the way. They want to exploit vulnerabilities, steal data, monetize it, or disrupt operations. The defenders, on the other side, want to protect their assets, data, and network. Finally, legitimate users who want to perform their function as usual and efficiently as possible and experience security measures for the most part, as a burden.
A Brief Analysis On Network Defenders vs Attackers:
- Defenders: Like a goalkeeper — a single failure can be catastrophic.
- Attackers: They have unlimited opportunities to try, without consuming resources, and only one score can make them win.
- Defenders: Defense mechanisms are costly and require 100% effectiveness.
- Attackers: They are continually shifting and setting the rules.
- Defenders: Must trade-off impact to legitimate users’ access to system against security needs. Security measures that are too cumbersome are rejected by the business.
- Attackers: Can conceal themselves as users and avoid detection.
Clearly, attackers have the dominant strategy. Regardless of what any other players do, attackers can get a more substantial payoff than defenders and legitimate users. Attackers don’t have to spend many resources, and still can score big if they are capable of breaching the network.
3. Beating Attackers at Their Game.
For quite some time, network security administrators had to take on the role of the “deceived.” They are always looking at ways to avoid skillful deceptive hackers, who are masters at social-engineering users, misinforming systems, and disguising their activities to avoid detection.
But how would you find equilibrium in such an unbalanced cybersecurity equation? How can you make both players equally competent?
By leveling the field and using their tricks against them. By using cyber deception.
Introducing Deception into The Game.
In a cybersecurity framework, deception is a strategy used to fool automated hacking tools and humans adversaries. Deceptive elements are used to entice, engage, and detect attackers.
The concept of “deception” alters the players’ decision-making strategies, and on a larger picture, the entire game. When we add deception into the mix, we could even re-name the game players, as the “Deceiver” and the “Deceived.” The deceived will unknowingly behave in a way that is unfavorable to them, but that is beneficial to the deceiver.
Now, the network defender can take the role of the deceiver.
Game theory can be used in network security to create tangible solutions. If game theory helps to anticipate “strategies” from attackers, it can help develop models that are useful for improving cybersecurity and also to develop new intelligent cyber deception systems.
4. Cyber Deception Systems.
In its cybersecurity report, the analyst firm Gartner revealed that ” Organizations that have chosen deception over other approaches report detecting threats with a low false-positive rate, radically simpler deployment, lower costs, and less operational burden…” And they were right. Deception is giving network defenders a chance at the dominant strategy. Defenders can use a deception system to distract and lure attackers into a trap.
Caught by surprise!
Attackers don’t know that they are interacting with a decoy, which delays, disrupts, and leads them into a corner. Now defenders will have the upper hand to react any way they want.
A deception system such as the TrapX DeceptionGrid opens the field for the attacker but lays it with mines, decoys, and traps. Attackers are diverted into fictitious resources, and away from real high-value assets.
But the deception doesn’t end there.
After being exposed, the attacker is misinformed with fake business data. Even the exfiltration stage can be set up as a deception.
To learn more about cyberattack case studies, analysis, and actionable recommendations on where and when to use deception, download the latest TrapX iOT Manufacturing Report.