UPDATE: Engineers at social network Twitter.com plugged a vulnerability in the company’s main Web page after attacks that exploited the hole may have hit more than 500,000 users.
The security hole was patched at about 9:45 AM ET, according to a post by Del Harvey (@delbius), the head of Twitter’s Trust and Safety Team. In a blog post Bob Lord on the Twitter Security Team said that the company first learned of the exploit at 5:54 AM Eastern Daylight Time. The hole in question had been patched internally by the company last month, but was inadvertently reintroduced with a Web site update, Lord wrote.
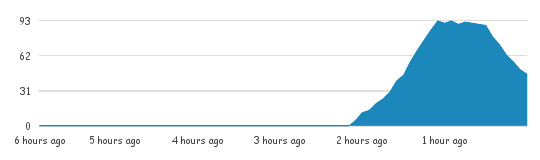
Security researchers at Kaspersky Lab started noticing a cross site scripting attack affecting the Twitter.com site about two hours earlier, just after 7:30 AM Eastern Time, USA. In the intervening two hours, the attacks spread like wildfire across the social network, with up to 100 users per second falling victim at its height, according to data from TwitScoop.com. Based on that figure, and given the length of the attack, it may have hit as many as half a million Twitter users, according to an estimate by George Wicherski, an analyst at Kaspersky Lab that was among the first to identify the attack.
Victims included high profile Twitter users including White House Press Secretary Robert Gibbs, who was perplexed by the balky javascript tweeted to more than 97,000 followers.
“My Twitter went haywire – absolutely no clue why it sent that message or even what it is…paging the tech guys…” Gibbs posted from the @PressSec Twitter account just after 8:30 AM Eastern Time.
The attacks leveraged a common javascript feature, onmouseover, which allows Web developers to program discrete actions when visitors move their mouse cursor over a designated area of a Web page. The attacks were mostly harmless, “proof of concept” attacks that simply reposted the javascript from the user’s session as a Tweet, said Costin Raiu at Chief Security Expert at Kaspersky Lab.
Exploits of the hole were, for the most point, harmless and appear to have been ad hoc rather than planned, as users learned of the cross site scripting hole, and developed novel ways of exploiting it.
“First, someone created an account that exploited the issue by turning tweets different colors and causing a pop-up box with text to appear when someone hovered over the link in the Tweet,” Lord wrote on the Twitter blog. “Other users took this one step further and added code that caused people to retweet the original Tweet without their knowledge.”
 Kaspersky researchers identified at least two worms that also launched on Tuesday morning, leveraging the same hole. Worm code was circulating on IRC within minutes of the discovery of the cross site scripting hole, Kaspersky Lab researcher Wicherski said in a blog post on the bug.
Kaspersky researchers identified at least two worms that also launched on Tuesday morning, leveraging the same hole. Worm code was circulating on IRC within minutes of the discovery of the cross site scripting hole, Kaspersky Lab researcher Wicherski said in a blog post on the bug.
The worms allowed attackers to infect a user’s account and those of his or her followers, as well. However, neither worm carried malicious payloads and neither appears to have spread as rapidly, Wicherski said.
Attack traffic began to taper off around by 10:00 AM Eastern time, with compromises at that time down to around 40 per minute as Twitter’s patch took hold. However, lingering compromises continued even after the patch from users accessing older, cached and unpatched versions of the page, Raiu said.
Cross site scripting attacks are among the most common types of Web vulnerabilities and the easiest to exploit. However, they’ve been more common on complex social networking Web sites like Facebook than on Twitter, which had instituted a Web of different checks and filters to prevent cross site scripting attacks, said Raiu.
Researchers were unclear how the latest hole slipped through that Web, but Raiu noted a recent overhaul of the Twitter.com site, unveiled on September 14, that may have inadvertently introduced the cross site scripting vulnerability.
The hole raises issues for Web based users of Twitter. Third party client applications to manage Twitter feeds, such as Twhirl and TweetDeck were not susceptible to the cross site scripting attack, Raiu noted. Twitter users concerned about future attacks might consider shifting to one of those applications, he said.









