Criminals in Eastern Europe have evolved their attacks against automated teller machines, moving beyond solely targeting consumers with card skimmers that steal debit card numbers, to attacks against banks using malware that allows someone to remove money directly from an ATM without the need for a counterfeit or stolen card.
Researchers at Kaspersky Lab, in conjunction with Interpol, today said they have detected the Tyupkin malware on more than 50 machines; only ATMs from a particular manufacturer running a 32-bit version of Windows are impacted.
“The Tyupkin malware is an example of the attackers taking advantage of weaknesses in the ATM infrastructure,” said Vicente Diaz, Principal Security Researcher at Kaspersky Lab’s Global Research and Analysis Team. “We strongly advise banks to review the physical security of their ATMs and network infrastructure and consider investing in quality security solutions.
“The fact that many ATMs run on operating systems with known security weaknesses and the absence of security solutions is another problem that needs to be addressed urgently,” Diaz said
Most of the Tyupkin submissions to Virus Total are from Russia (20) with a limited number of samples (4) reported from the United States.
Kaspersky researchers have seen several variants of this malware with subtle advancements in each. The latest, version .d, includes anti-debug and anti-emulation features and also disables application security software from a particular vendor.
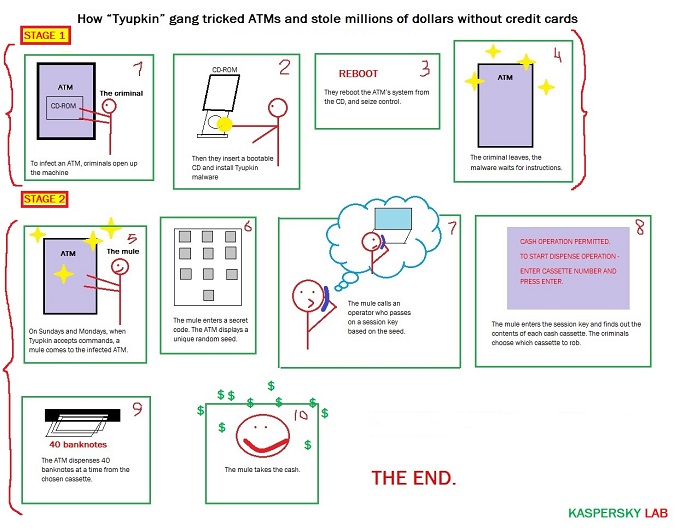
While all of these techniques aim to frustrate detection and examination of the malware, the criminals behind this operation also went to great pains to ensure their exclusive access to the money. The malware, for example, is configured to run only at specific times and a key is required in order to access the infected ATM. The key, researchers said, is based on a random seed number used for each session and are used to prevent random users from stumbling upon the interface used to steal money.
“When the key is entered correctly, the malware displays information on how much money is available in every cassette and allows an attacker with physical access to the ATM to withdraw 40 notes from the selected cassette,” the researchers wrote.
The attackers targeted the ATMs individually, installing the malware by uploading it from a bootable CD. Two files are copied: an executable and a debugging file which is removed after a registry key is created for the executable. The malware waits for user input, which it accepts only on Sunday and Monday nights, the researchers said.
Once the criminal enters the session key and it’s accepted, they are prompted to enter the correct cassette number in order to receive 40 bank notes from the machine, researchers said. The malware also disables the local area network, likely in order to disrupt any remote troubleshooting, the researchers wrote.
U.S. regulators, meanwhile, earlier this year warned banks that hackers were leveraging phishing attacks to access and alter Web-based ATM management interfaces that criminals were taking advantage of to cash in on millions-worth of fraudulent withdrawals. Unlimited Operation scored the criminals more than $40 million.
“These control panels, often web-based, manage the amount of money customers may withdraw within a set time frame, the geographic limitations of withdrawals, the types and frequency of fraud reports that its service provider sends to the financial institutions, the designated employee that receives these reports, and other management functions related to card security and internal controls,” said an advisory from the Federal Financial Institutions Examination Council (FFIEC).
“Offenders are constantly identifying new ways to evolve their methodologies to commit crimes, and it is essential that we keep law enforcement in our member countries involved and informed about current trends and modus operandi,” said Sanjay Virmani, Director of the INTERPOL Digital Crime Centre.