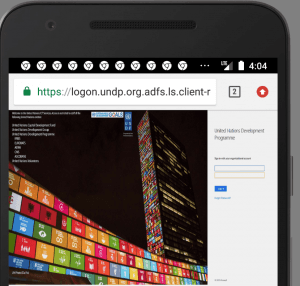
An ongoing, mobile-focused phishing campaign is targeting the United Nations and several humanitarian aid organizations, including UNICEF, the Red Cross and UN World Food. The campaign is using landing pages signed by SSL certificates, to create legitimate-looking Microsoft Office 365 login pages.
The unusual aspect of the campaign is that it identifies mobile devices; once detected, it then logs keystrokes in real-time as the user enters them into the phishing page.
“Specifically, Javascript code logic on the phishing pages detects if the page is being loaded on a mobile device and delivers mobile-specific content in that case,” explained researchers from Lookout, in a posting on Friday. They noted that mobile web browsers also unintentionally help obfuscate phishing URLs by truncating them, making it harder for the victims to vet the legitimacy of the pages.
“The mobile-aware component found in this campaign is further proof that phishing attacks have evolved to target mobile devices,” Lookout researchers said in the post. “Mobile phishing has emerged as a source of increasing risk for enterprises, as the post-perimeter world and widespread adoption of bring your own device (BYOD) policies blurs the lines between personal devices and corporate networks, not to mention the expanded multi-channel threat surface presented by such devices and mobility as a whole.”
Meanwhile, the key-logging functionality is actually embedded directly into the password field of the phishing login pages; as such, the command-and-control (C2) infrastructure collects anything entered into the fields, even if the use abandons the process halfway through.
“The intensity and sophistication of phishing techniques are constantly increasing. New phishing styles emerge frequently, but the core of these scams remains the same – an attempt to prompt email users to click a link or download an attachment that will trigger malicious activity and might result in a data breach,” Shlomi Gian, CEO at CybeReady, told Threatpost. “What is needed is a methodology that trains people repetitively to carefully watch incoming emails. Alarming signals include unknown senders, uncommon URLs, awkward language and even context and timing of email. The best advice is to ask yourself if you were expecting an email from this source or an email with such content.”
There are two domains that are hosting the phishing content, according to Lookout Security, and they’ve both been live since March 2019. The associated IP network block and Autonomous System Number (ASN) has been known to have hosted malware in the past, researchers said.
“The latest phishing campaign targeting officials from the United Nations, UNICEF, Red Cross and other humanitarian aid organizations demonstrates how sophisticated and highly convincing phishing attacks have become,” said Alexander García-Tobar, CEO and co-founder of Valimail, via email. “By using deviously coded phishing sites, hackers are attempting to steal login credentials and ultimately seek monetary gain or insider information.”
It should be noted that some of the SSL certificates used by the phishing infrastructure are expired – they were valid from May 5 to August 3, and from June to September 3. Since all major browsers alert users about expired SSL certificates and mark the pages as “unsafe,” which likely cuts phishing efforts from those specific pages off at the knees. However, six certificates are still valid, and the campaign goes on.
“These latest attacks targeting United Nations and global charity websites use TLS certificates to make malicious domains appear legitimate, they take advantage of the implicit trust users have in the green padlock created by TLS certificates,” said Kevin Bocek, vice president of security strategy and threat intelligence at Venafi, via email. “Internet users have been trained to look for a green padlock when they visit websites, and bad actors are using SSL/TLS certificates to impersonate all kinds of organizations.
This tactic is increasingly common, he added. “For example, in 2017, security researchers uncovered over 15,000 certificates containing the word ‘PayPal’ that were being used in attacks. And in June, the FBI issued a warning stating that the green padlock on websites doesn’t mean the domain is trustworthy and safe from cybercriminals,” he said. “In order to protect businesses and users, security teams must identify all the legitimate TLS certificates on their own networks. They also need to identify fraudulent certificates issued by attackers that are being used to impersonate their organization. Technologies like certificate transparency and certificate reputation can definitely help, but as the number of certificates issued every day continues to skyrocket, more help is definitely needed.”