An updated version of the AZORult spyware has been sighted as the payload in a large spam campaign – just one day after debuting on the Dark Web.
AZORult steals information and can download additional malware; it’s been around since at least 2016, when Proofpoint researchers identified it as part of a secondary infection via the Chthonic banking trojan. It’s become fairly common in a range of malspam attacks since then, the firm noted – but the authors have now released what researchers termed in a Monday posting “a substantially updated version.”
The upgraded code has a raft of sophisticated improvements, including the ability to steal histories from non-Microsoft browsers, a conditional loader that checks certain parameters before running the full malware; support for Exodus, Jaxx, Mist, Ethereum, Electrum, Electrum-LTC cryptocurrency wallets; the ability to use system proxies; and a few administrative tweaks, like location awareness and the ability to more easily delete spy reports that don’t have useful information.
The conditional loader is particularly interesting: In the admin panel, the user can specify rules for attacking victims to ensure that running the malware is fruitful: For instance, it can check if certain desired cookies or saved passwords from specific sites are present on the target machine, or it can verify if there’s data from cryptocurrency wallets on board.
Once connected to the C2 server, the infected machine sends four reports with information: An “info” file contains basic computer information such as Windows version and computer name; “pwds” contains stolen passwords; “cooks” includes cookies or visited sites; and “file” contains the contents of the cookie files and a file containing more system profiling information, including machine ID, Windows version, computer name, screen resolution, local time, time zone, CPU model, CPU count, RAM, video card information, process listing of the infected machine and software installed on the infected machine.
“After the initial beaconing, receiving a configuration, and exfiltrating stolen information from the infected machine, AZORult may download the next payload,” Proofpoint researchers explained today.
The researchers saw the new version in action in a large email campaign on July 18, just one day after it debuted in underground forums. They attributed the campaign to the TA516 threat actor, which has a particular expertise in cryptocurrencies.
“[It was] leveraging its new capabilities to distribute Hermes ransomware,” they said. “It is always interesting to see malware campaigns where both a stealer and ransomware are present, as this is less common, and especially disruptive for recipients who initially may have credentials, cryptocurrency wallets and more stolen before losing access to their files in a subsequent ransomware attack.”
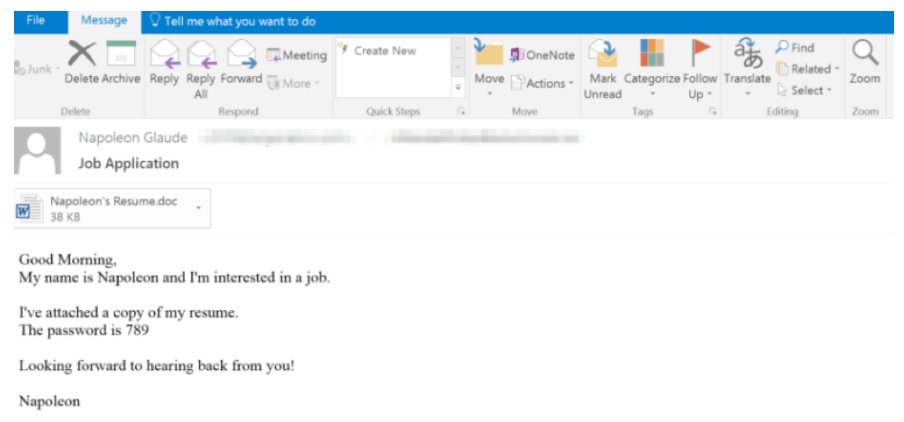
The campaign consisted of thousands of messages targeting North America with a timeworn social-engineering lure: Employment-related subject lines such as “Job Application,” purporting to have resumes attached.
Interestingly, a successful infection required more than the usual amount of user interaction. In a move calculated to avoid antivirus, the user would need to download the document, which did not become weaponized until the victim typed in a password in a pop-up box (provided in the body of the email). After that, he or she would then need to enable macros for the document to download AZORult, which in turn downloaded the Hermes 2.1 ransomware.
Researchers added that the implications of the improvements could be considerable.
“AZORult malware, with its capabilities for credential and cryptocurrency theft, brings potential direct financial losses for individuals as well as the opportunity for actors to establish a beachhead in affected organizations,” they said.