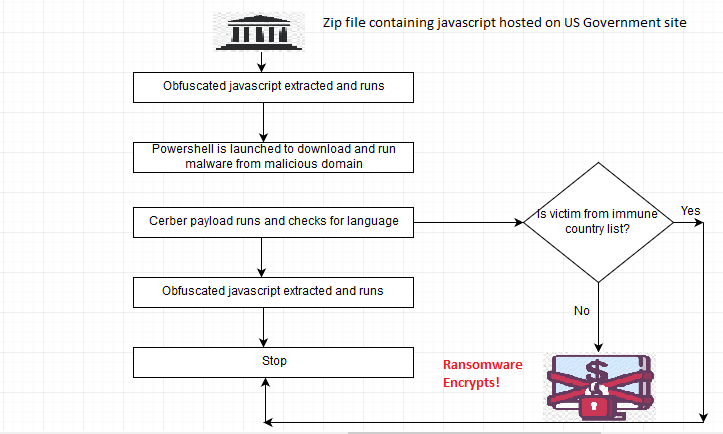
As recently as Wednesday afternoon, a U.S. government website was hosting a malicious JavaScript downloader that led victims to installations of Cerber ransomware.
Researcher Ankit Anubhav of NewSky Security tweeted the discovery Wednesday, and within hours, the malware link was taken down. It’s unknown whether anyone was infected through the site.
#Javascript #malware using #powershell hosted on US Government site. Link is still live! cc @USCERT_gov
IOC :: https://t.co/Thoyom3PTF pic.twitter.com/OjX9M7OzDU— Ankit Anubhav (@ankit_anubhav) August 30, 2017
It’s also unknown how the downloader was dropped onto the .gov site. Anubhav speculated that either the site was hacked, or it possibly stores attachments from government officials’ emails and the downloader was archived.
The researchers did point out similarities to the Blank Slate spam campaign which earlier this year was spreading Cerber. Emails in that campaign contained only a double-zip archive with the second containing either a malicious JavaScript file or a malicious Microsoft Word document. The emails contain no text, and experts believed then that all of this combined to evade detection.
Repeated requests for comment from the Department of Homeland Security were not returned in time for publication.
Anubhav said the site was hosting a .zip archive that contained JavaScript that included obfuscated PowerShell. The PowerShell downloads a gif file which is in reality a Cerber executable.
Cerber has been in circulation for more than a year, and like most crypto-ransomware families, it has been spread by exploit kits, spam campaigns, and the same botnet used by the Dridex financial malware. Earlier this year, attackers were exploiting a critical Apache Struts vulnerability on Windows servers and dropping Cerber on the machines.
Anubhav and Mariano Palomo Villafranca, a malware analyst with Spanish telco Telefonica, today published an analysis of the attack. They point out that most U.S. .gov sites are whitelisted by reputation services, making them ideal malware hosts for attackers wishing to elude detection.
Anubhav said a victim could be sent a link to the page hosting the .zip file and once they click on it and it’s executed, the obfuscated JavaScript is extracted and launches PowerShell which downloads the malware from a known misbehaving domain.
“This powershell downloads malware from a known malicious site and runs it,” Anubhav said. “All these steps of course happen automatically and end user wont see it.”
Cerber is the payload and before it encrypts files on the host machine, it checks for certain language packs for Commonwealth of Independent States (CIS) countries running on the compromised computer before proceeding.
Anubhav and Villafranca wrote that the gif executable was a NSIS installer which extracts the Cerber JSON file configuration. In March, researchers found that Cerber infections were finding success in bypassing detection by hiding inside NSIS installers before executing. Researchers at Deep Instinct told Threatpost that Cerber versions 4 and 5.1 and many versions of Locky were using this technique, along with different versions of Cryptolocker and Cryptowall.
NSIS, which is short for Nullsoft Scriptable Install System, is an open source system that’s used to build Windows installers.
Cerber, like other ransomware, demands Bitcoin in exchange for the decryption key that allows users to recover encrypted data. Early versions of the malware were sold as a service, and yet others were coded to force the victim’s machine to speak to the user and repeat over and over that documents and files had been encrypted.