The U.S. has slapped sanctions on three well-known North Korean state-sponsored hacker groups – including the group that was tied to the 2017 WannaCry ransomware attacks and the 2014 cyberattack on Sony Pictures Entertainment.
The three that were sanctioned are the infamous Lazarus Group, as well as two Lazarus sub-groups called Bluenoroff and Andariel. All three are owned by the Reconnaissance General Bureau (RGB), North Korea’s primary intelligence bureau. The U.S. Department of Treasury on Friday said that the sanctions freeze any U.S. related financials assets with the groups and bar any U.S. dealings with them.
“Treasury is taking action against North Korean hacking groups that have been perpetrating cyberattacks to support illicit weapon and missile programs,” said Sigal Mandelker, Treasury Under-Secretary for Terrorism and Financial Intelligence, in a media statement. “We will continue to enforce existing U.S. and UN sanctions against North Korea, and work with the international community to improve cybersecurity of financial networks.”
Together, the three groups have hit U.S. entities and organizations with dozens of malicious cyberattacks – including widescale, operation-crippling ransomware attacks, information-stealing hacks and at one point stealing $571 million in cryptocurrency in just five attacks.
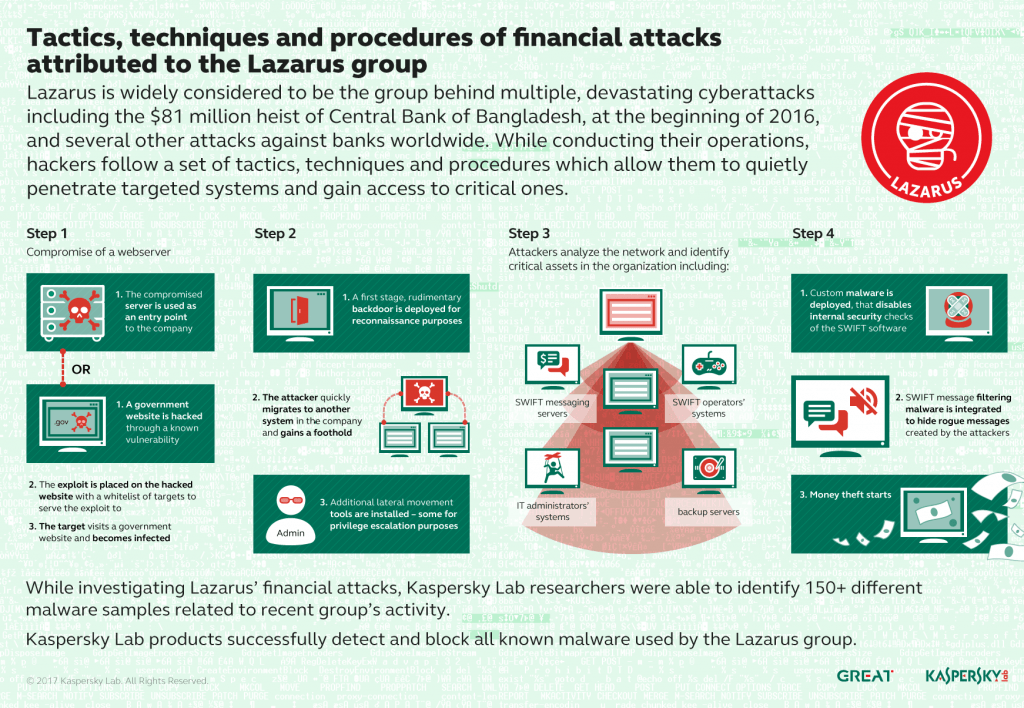
Lazarus Group first appeared in 2010, and is best known for being behind the 2014 attack against Sony Pictures Entertainment and for links to the global WannaCry attack in 2017 that caused millions of dollars of economic damage and impacted at least 150 countries.
Beyond these, the APT has continued to stay active over the years, most recently seen targeting the cryptocurrency business by sending out documents containing weaponized macros to spread various malware payloads, and targeting Apple users with PowerShell scripts that control macOS malware.
The U.S. dinged two sub-groups of Lazarus Group with sanctions as well. One, Bluenoroff, appeared as early as 2014 and was formed by North Korea’s government to earn revenue illicitly in response to increased global sanctions, according to the Treasury release.
Bluenoroff was behind the theft of $80 million dollars from the Central Bank of Bangladesh’s New York Federal Reserve account, by making more than 36 large fund transfer requests using stolen SWIFT credentials. It has launched scores of phishing attempts and backdoor intrusions targeting the financial space, and according to reports, by 2018 had attempted to steal over $1.1 billion dollars from financial institutions.
“Bluenoroff conducts malicious cyber-activity in the form of cyber-enabled heists against foreign financial institutions on behalf of the North Korean regime to generate revenue, in part, for its growing nuclear weapons and ballistic missile programs,” according to the Treasury release.
The second sub-group is Andariel, which was first spotted in 2015 and has targeted South Korea’s government to collect information and create disorder. The group has aimed to steal bank card information by hacking into ATMs and withdrawing cash or stealing customer information to sell on the black market. The group also developed malware to hack into online poker and gambling sites to steal cash.
The sanctions mark a wider effort on the U.S. government’s part for cracking down on “an increasing North Korean cyber-threat,” the Treasury department said. For instance, they said that the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) recently disclosed malware samples which were attributed to North Korean cyber-actors.
“This, along with today’s OFAC [Office of Foreign Assets Control] action, is an example of a government-wide approach to defending and protecting against an increasing North Korean cyber-threat and is one more step in the persistent engagement vision set forth by USCYBERCOM [U.S. Cyber Command],” the Treasury said in its media statement.
Interested in the role of artificial intelligence in cybersecurity, for both offense and defense? Don’t miss our free Threatpost webinar, AI and Cybersecurity: Tools, Strategy and Advice, with senior editor Tara Seals and a panel of experts. Click here to register.