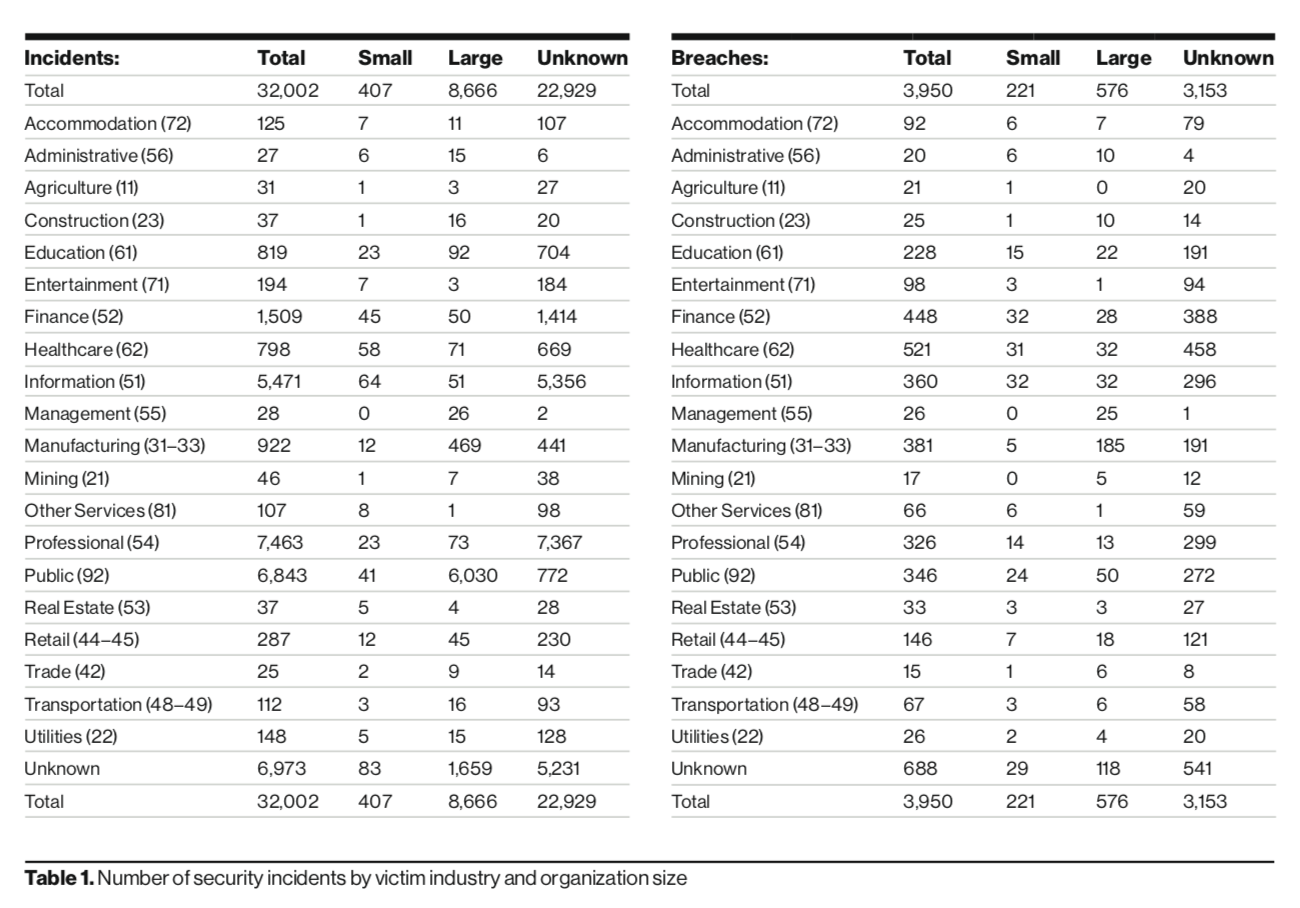
Denial-of-service (DoS) attacks have spiked over the past year, while cyber-espionage campaigns have spiraled downwards. That’s according to Verizon’s 2020 Data Breach Investigations Report (DBIR) released Tuesday, which analyzed 32,002 security incidents and 3,950 data breaches across 16 industry verticals.
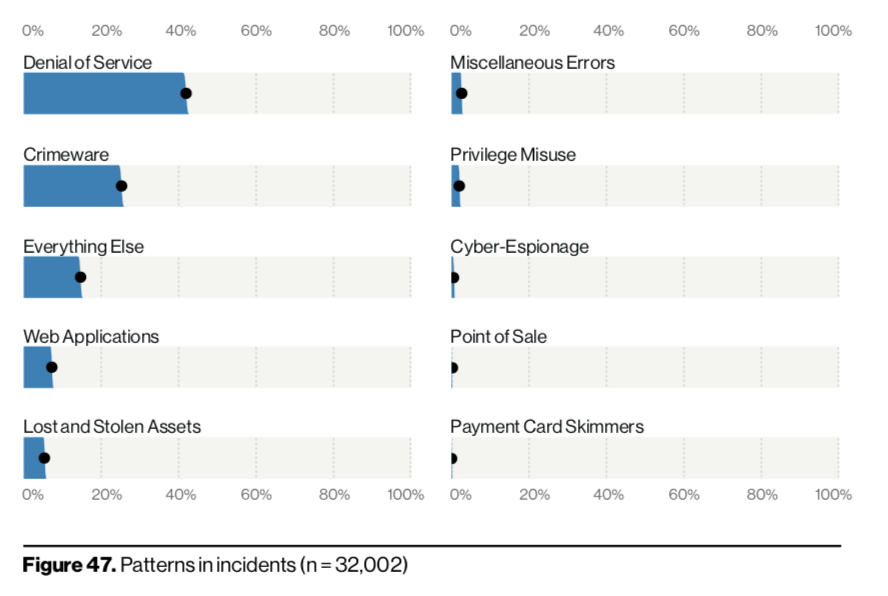
Notably, this year DoS attacks increased in number (13,000 incidents) and were also seen as a bigger part of cybercriminals’ toolboxes (DoS attacks made up 40 percent of security incidents reported), beating out crimeware and web applications. While DoS attacks use differing tactics, they most commonly involve sending junk network traffic to overwhelm and crash systems. It doesn’t help that cybercriminals have been creating new and dangerous botnets to launch DoS attacks, like Kaiji or Mirai variants, over the past few years.
“While the amount of this traffic is increasing as mentioned, in DDoS, we don’t just look at the number of attacks that are conducted,” said researchers. “We also look at the bits per second (BPS), which tells us the size of the attack, and the packets per second (PPS), which tells us the throughway of the attack. What we found is that, regardless of the service used to send the attacks, the packet-to-bit ratio stays within a relatively tight band and the PPS hasn’t changed that much over time, sitting at 570 Mbps for the most common mode.”
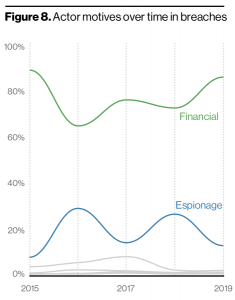
Cyber espionage attacks meanwhile have seen a downward spiral, dropping from making up 13.5 percent of breaches in 2018 to a mere 3.2 percent of data breaches in 2019. That may come as a surprise given that espionage campaigns were actually on the rise in the 2019 Verizon DBIR. In addition, a slew of cyber espionage campaigns (such as ones targeting the WHO, several governments in the Asia-Pacific region and more) were unearthed over the past year – but researchers say under reporting may be a factor in the dipping statistics.
“The drop in raw numbers could be due to either under-reporting or failure to detect these attacks, but the increase in volume of the other patterns is very much responsible for the reduction in percentage,” said researchers.
In fact, financially motivated breaches continue to not only be more common than espionage campaigns by a wide margin (making up 86 percent of all breaches), but also increasing over the past year, they said.
Breach Origins
When it comes to data breaches, almost half (45 percent) stemmed from actual hacks, while 22 percent used social attacks. Twenty-two percent breaches involved malware and 17 percent were created by errors. And 8 percent of breaches stemmed from misuse by authorized users.
In fact, internal actors were only behind 30 percent of breaches, with the majority (70 percent) actually coming from external actors. While researchers said that incidents stemming from “insider actors” have grown over the past few years, that’s likely due to increased reporting of internal errors rather than evidence of actual malice from these actors.
“External attackers are considerably more common in our data than are internal attackers, and always have been,” said researchers. “This is actually an intuitive finding, as regardless of how many people there may be in a given organization, there are always more people outside it. Nevertheless, it is a widely held opinion that insiders are the biggest threat to an organization’s security, but one that we believe to be erroneous.”
Malware Down
Malware has been on a consistent and steady decline as a percentage of breaches over the last five years, researchers said, due in part to the increasing level of access by cybercriminals to credentials.
“We think that other attack types such as hacking and social breaches benefit from the theft of credentials, which makes it no longer necessary to add malware in order to maintain persistence,” said researchers.
Accordingly, the top malware “varieties” in data breaches was topped by password dumpers (which are used to collect credentials), followed by capture app data and ransomware.
Ransomware attacks continue to grow over the past year and have created high-profile headlines and headaches for companies, such as Norsk Hydro. Ransomware is the third most common “malware breach” variety and the second most common “malware incident” variety. Part of this continued growth can be explained by the ease with which attackers can kick off a ransomware attack, researchers stressed.
“In 7 percent of the ransomware threads found in criminal forums and market places, ‘service’ was mentioned, suggesting that attackers don’t even need to be able to do the work themselves,” said researchers. “They can simply rent the service, kick back, watch cat videos and wait for the loot to roll in.”
Vertical-Specific Findings
The Verizon DBIR also broke down data breaches by vertical to show that cybercriminals are drastically changing how they are targeting industries. For instance, Point of Sale (PoS)-related attacks once dominated breaches in the accommodation and food services industry – however, they have been replaces by malware attacks and web application attacks.
“Instead, responsibility is spread relatively evenly among several different action types such as malware, error and hacking via stolen credentials,” said researchers. “Financially motivated attackers continue to target this industry for the payment card data it holds.”
The educational services industry saw phishing attacks trigger 28 percent of breaches, and 23 percent of breaches stem from hacking via stolen credentials. Ransomware is a top threat for the education space, with ransomware accounting for approximately 80 percent of malware infections in the incident data.
Ransomware attacks, triggered by financial motivations, also plagued the healthcare industry. Other top security issues leading to breaches include lost and stolen assets and basic human error. However, privilege misuse, which has topped data breach causes for healthcare in the past, for the first time this year wasn’t an issue in the “top three”. In the 2019 report, privilege misuse at 23 percent of attacks, while in 2020, it has dropped to just 8.7 percent.
Despite that, “This year, we saw a substantial increase in the number of breaches and incidents reported in our overall dataset, and that rise is reflected within the Healthcare vertical,” said researchers. “In fact, the number of confirmed data breaches in this sector came in at 521 versus the 304 in last year’s report.”
Finally, financial and insurance industries were plagued by phishing attacks and web applications attacks that leverage the use of stolen credentials. The attacks in this sector are perpetrated by external actors who are financially motivated to get easily monetized data (63 percent), internal financially motivated actors (18 percent) and internal actors committing errors (9 percent).
The Positives
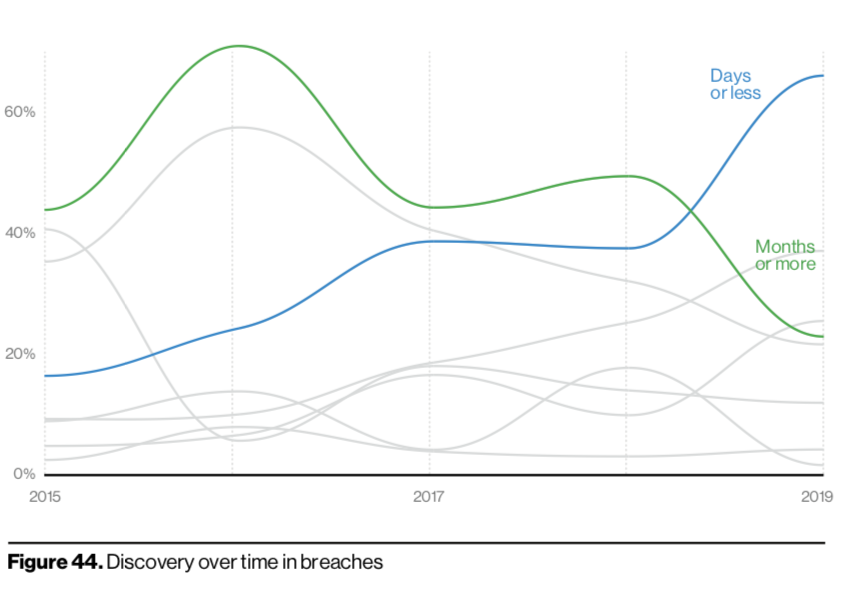
Breach timelines continue to show promising results. The number of companies discovering incidents in days or less is up, while containment in that same timeframe surpassed its historic 2017 peak.
Researchers also warned to keep in mind that the positive incident response numbers are likely due to the inclusion of more breaches detected by managed security service providers (MSSPs) in the report’s sampling. Also, it still took a quarter of companies dealing with data breaches months or more.
“All in all, we do like to think that there has been an improvement in detection and response over the past year,” said researchers.
Concerned about the IoT security challenges businesses face as more connected devices run our enterprises, drive our manufacturing lines, track and deliver healthcare to patients, and more? On June 3 at 2 p.m. ET, join renowned security technologist Bruce Schneier, Armis CISO Curtis Simpson and Threatpost for a FREE webinar, Taming the Unmanaged and IoT Device Tsunami. Get exclusive insights on how to manage this new and growing attack surface. Please register here for this sponsored webinar.