Targeted cyberespionage attacks have dominated discussions within the security community and outside of it from the mainstream media to the halls of the executive and legislative branches of government. But until now, discussions about attacks stemming from China that target intellectual property from engineering, manufacturing and military interests in the United States, have been anecdotal and one-off analyses of specific breaches.
The 2013 Verizon Data Breach Investigations Report (DBIR) has changed that. For the first time, the report has branched out and extensively quantified nation-state attacks motivated by espionage. This is a significant departure from previous editions of the report, which many consider to be the industry standard research on data breaches.
Released today, the report takes great pains to correlate threat actor motives and the data that is compromised. It also has a host of new contributors, now 19 in all, bringing fresh perspectives to the data set used to make up the bulk of the 60-plus page report. As has been the case with the past eight DBIRs, the data comes from paid forensic investigations carried out by Verizon’s RISK Team, in addition to contributions from law enforcement and computer emergency response teams worldwide, as well as industry groups, large consulting and services organizations, and the U.S. Secret Service.
The data in this year’s report comes from 621 breaches where data loss or disclosure was confirmed and 47,000 reported security incidents. Despite the new focus on espionage-related attacks, the report still does its customary deep dive into financially motivated attacks and comparing the tactics used by cybercriminals to those used by nation-state actors.
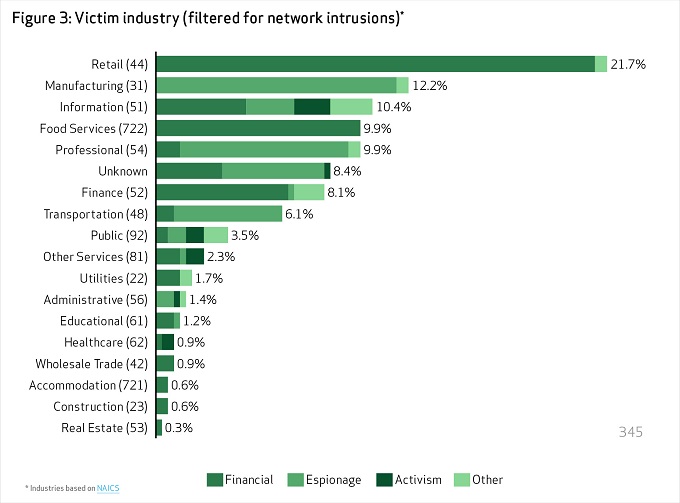
The report’s bevy of new contributors brought with them the most insightful data into attacks tied to China targeting intellectual property, which accounted for 19 percent of breaches.
“They all focus on something different,” said Jay Jacobs, one of the DBIR authors and a principal at Verizon. “You have to understand the research and information you want to pull out; that makes a difference in what you want to share. If you want to count the number of SQL injection attacks, that’s one thing. If you want to correlate that to industry and organization size, you have to expand your vision.”
The majority of data breaches still rely on the exploitation of weak or default credentials or stolen passwords. Hackers continue to blend hacking and malware to steal payment card information or to gain legitimate access to network resources to steal intellectual property. Most financially motivated attacks are opportunistic and rated as low difficulty, while those motivated by espionage use a combination of phishing emails and advanced malware to ramp up the difficulty of initial compromise and subsequent actions.
And there isn’t a typical victim for espionage attacks.
“The ‘I’m too small to be a target’ argument doesn’t hold water. We see victims of espionage campaigns ranging from large multinationals all the way down to those that have no IT staff at all,” the report says. “Lesson two is that some industries appear to be more targeted than others.”
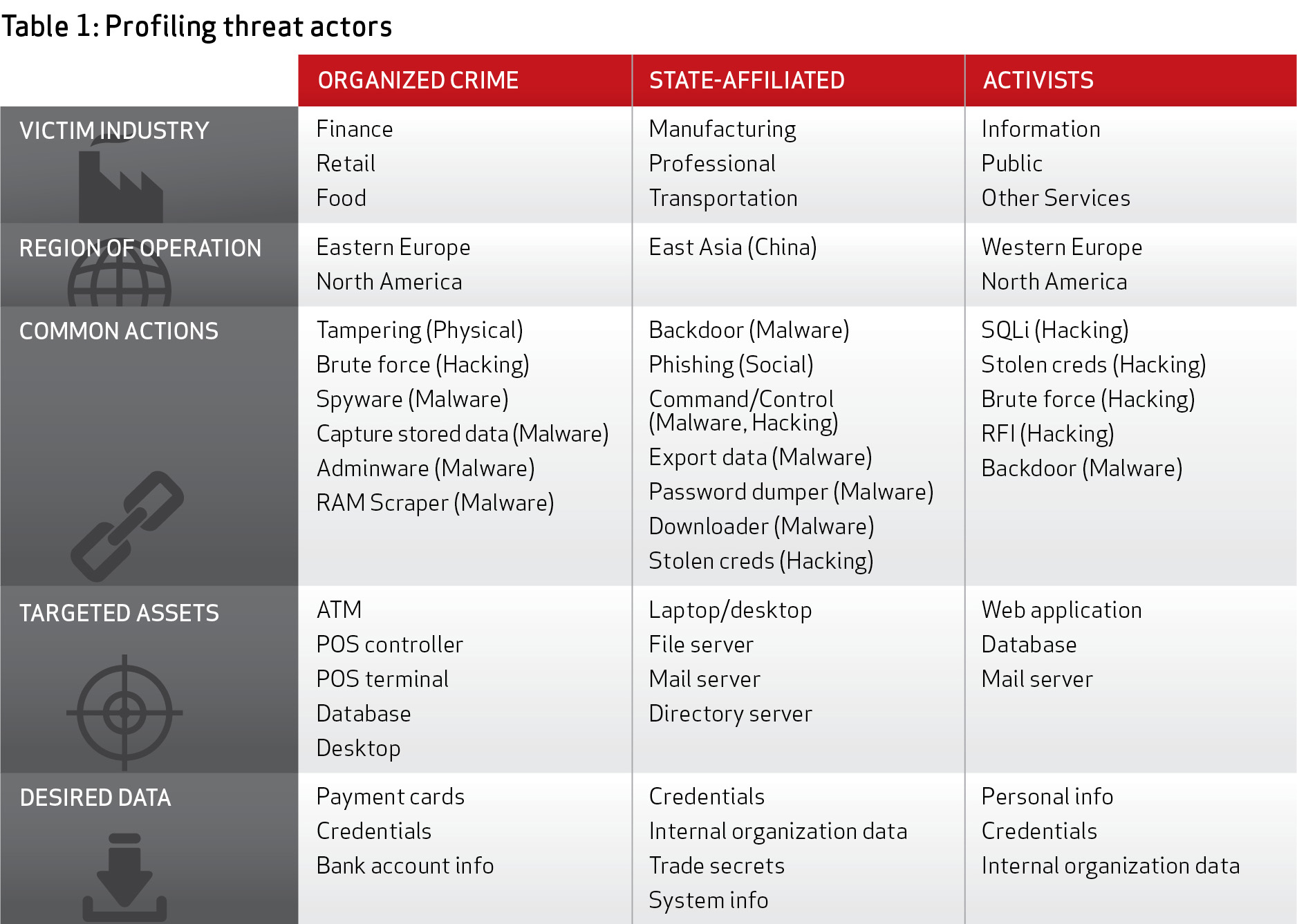
Most attacks motivated by espionage target the manufacturing and transportation industries, while retail and food services lead the way for financially motivated actors. State-sponsored hackers covet not only secrets and internal organizational data, but system information.
“Most organizations have some form or proprietary or internal information they want kept private. Without this secret sauce, it’s hard to stay competitive,” the report says. “And because it’s a secret and competitively advantageous, others may want to steal that sauce. Thus, ‘who wants my sauce?’ is probably a better question than ‘am I a target of espionage?’”
The number of state-affiliated actors accounts for 21 percent of attacks, compared to 55 percent attributed to organized crime groups. While China accounts for the majority of state-affiliated espionage attacks (96 percent), Eastern European countries such as Romania, Bulgaria and Russian Federation countries account for the bulk of financial crimes targeting payment systems with commodity malware not found in espionage attacks. Attribution, Verizon says, isn’t based just on geolocation of IP addresses for example, but data from arrests and the use of particular tactics associated with known groups of attackers. Insiders, meanwhile, aren’t on the radar with 92 percent of attacks attributed to external sources, again, most of those coming from criminal groups. Insiders have a role in 14 percent of data breaches, most of that number resulting from non-malicious actions, including human error.
The use of malware hasn’t tapered off. Espionage-related attacks, for example, account for a spike in the use of malicious email attachments as part of phishing campaigns. Phishing has become the initial entry point in many financial attacks too, in addition to direct compromise of a point-of-sale system or ATM machine. Malware used in espionage attacks, however, has very different goals than financially motivated attacks. Malware used to spy on organizations enables prolonged access to systems, control of those systems, and the ability to capture and exfiltrate data.
Spyware, keyloggers and RAM scrapers dominate the types of malware used in financially motivated attacks, while in espionage attacks, the threat actors are interested in a number of different things including grabbing screenshots of sensitive data. State-affiliated attackers are interested in maintaining persistence on machines and want to install backdoors in order to move data and install more malware such as downloaders, password dumpers and rootkits.
“Throughout this process, attackers promulgate across the systems within the network, hiding their activities within system processes, searching for and capturing the desired data, and then exporting it out of the victim’s environment,” the report says.
Hacking remains the most popular way attackers are infiltrating organizations, primarily through the use of stolen credentials. In financially motivated attacks, hackers will brute force attacks to steal weak credentials, or socially engineer them. Organized crime groups behind financially motivated attacks again made payment card data the most sought-after data type; that in addition to identity information can most quickly be turned into cash. In espionage attacks, stolen credentials are used to set up backdoor connections and then shell services such as SSH or RPC are used to pivot internally to different network resources. Similarly, Web-based desktop sharing services such as RDP and VNC are favorites for financially motivated attackers.
Given the number of new data sources, this year’s DBIR branches out in a number of new directions. With the number of high-profile espionage attacks gaining more attention, i.e., attacks on the New York Times, Apple, Facebook, Twitter and a number of government an activist organizations, organizations now have more insight into attacks that rely on more than social engineering and commodity malware.
“We’re seeing a diverse set of data that we can analyze,” Verizon’s Jacobs said. “We’re getting more views into breach data and seeing a diversity in threat actors and motives.”










