 It can be hard to parse the results of the Verizon Data Breach Investigation Report (DBIR), what with the shifts from year to year in the sources of breach data collected. Last year’s report, if you recall, found a stunning drop in incidents of data theft in 2010, even as tracking sites like Datalossdb.org reported no noticeable change that year.
It can be hard to parse the results of the Verizon Data Breach Investigation Report (DBIR), what with the shifts from year to year in the sources of breach data collected. Last year’s report, if you recall, found a stunning drop in incidents of data theft in 2010, even as tracking sites like Datalossdb.org reported no noticeable change that year.
Frankly, it’s hard to read the DBIR and not have the term “sample bias” float into your head time and again. But the DBIR report has always been a good way to understand the security Zeitgeist, and this year’s report is no different, with more normal-seeming results and a focus on the actions of ideologically motivated hacking groups which, Verizon claims, were linked to 58% of all the data stolen from customers in 2011.
The 2011 Data Breach Investigation Report culls information from information gathered during forensic investigations conducted by Verizon from the past year. Around 90 incidents involving data compromise were documented by Verizon’s RISK Team, as well as the Dutch National High Tech Crime Unit, the Australian Federal Police, the U.S. Secret Service, Irish Reporting & Information Security Service (IRIS) and the UK’s Police Central e-Crime Unit, part of the Metropolitan Police, Verizon said. All told, the report comprises data on 855 incidents that compromised 174 million records.
Ideologically motivated “hacktivist” attacks were few and far between, said Chris Novak, the Managing Principal of Investigative Response on Verizon’s RISK Team. But when they happened, they were big. “Looked at from numbers perspective, they were just 2% of breaches, but 58% of compromised records,” he said.
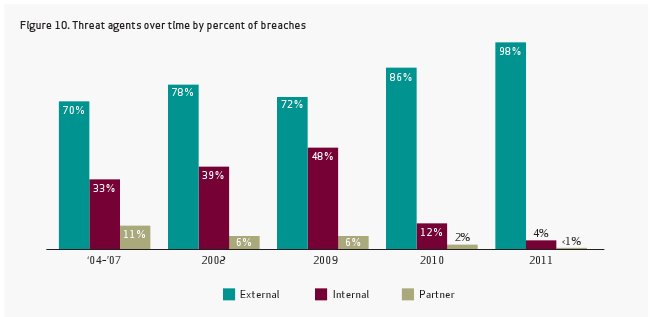
One explanation is that targeted “hacktivist” attacks on companies like Sony, HBGary and Stratfor were designed, specifically, to net huge volumes of data that could then be used to expose and embarrass the victim online.
“There’s a big divide between smash and grab attacks and those going after large organizations in order to get significant amounts of data,” Novak said.
Despite the high profile given to targeted attacks by groups like Lulz Security and Anonymous, most data breaches that Verizon and its partner organizations investigated in 2011 were at small firms. Companies employing between 11 and 100 employees accounted for 570 of the 855 incidents – or 67%.
Most of the incidents involved low-skill hacks that focused on targets of opportunity, rather than pre selected victims, the report concludes. Fully 79% of victims in the DBIR were considered to be targets of opportunity, Verizon reports. Often, that was because they harbored and easily exploitable weakness in their IT infrastructure. A huge percentage of attacks – 96% – were deemed “not difficult” to carry out, the report concludes.
The picture that emerges is one of semi-automated, industrial scale attacks against large numbers of organizations in a short time frame, with “little to no resistance” offered by the victim. Hacking and malware-based attacks were the most common elements of the attack. In fact, some form of malware was used by an attacker in around 95% of the data breach cases that made up the 2011 report, Novak said.
Beyond that, compromised organizations often go weeks – or longer – to even realize a compromise has taken place, Verizon concluded. Fully 85% of the breaches took “weeks or more” to discover. More than 90% were discovered by a third party, not by the victim organization.
The picture that emerges is of a “digital divide” when it comes to both attacks and protections, said Novak. Larger companies with healthy IT budgets can afford both the tools and professionals to prevent the most common types of attacks, to enforce best practices like strong passwords that can lead to data compromise. And, when incidents do occur, larger companies are more likely to spot them in a timely manner.
On the other side of the divide is the sea of smaller organizations that lack both the budget and staff to deploy even basic security tools like firewall, log monitoring and intrusion detection tools. Those organizations then become easy targets to criminal groups. And they’re less likely to notice the attack when it occurs, increasing the damage done by the attackers, Novak said.
“Large organizations are more likely to have mechanisms in place to thwart attacks, whereas small organizations don’t,” he said.
Verizon recommends that companies of all size do basic blocking and tackling on security: making sure that they have essential security controls in place and checking to make sure that they remain so. Organizations could do a better job of mining event logs for potential incidents, and in culling data that they no longer use from their network.
Finally, organizations of all sizes need to do a better job preparing for the inevitable: a hack or data breach that affects their firm, he said. “You have to prepare for what you’re going to do. What are the mandatory elements of your response plan? Once you know that, draw up your plan,” Novak said. “A lot of organizations assume they’ll have time to figure everything out before an event happens, and that’s a dangerous assumption.”









