On Wednesday, Verizon’s Visible – an all-digital, uber-cheap wireless carrier – confirmed what customers have been complaining about on Reddit and Twitter all week: They lost control of their accounts; had their passwords and shipping addresses changed; and some got stuck with bills for pricey new iPhones.
The carrier denied suffering a data breach. Rather, on Wednesday, it described what sounds like a credential-stuffing attack:
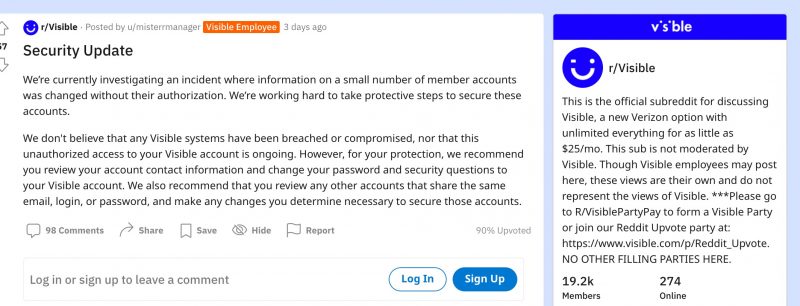
Visible is aware of an issue in which some member accounts were accessed and/or charged without their authorization. As soon as we were made aware of the issue, we immediately initiated a review and started deploying tools to mitigate the issue and enable additional controls to further protect our customers.
Our investigation indicates that threat actors were able to access username/passwords from outside sources, and exploit that information to login to Visible accounts. If you use your Visible username and password across multiple accounts, including your bank or other financial accounts, we recommend updating your username/password with those services.
Protecting customer information — including securing customer accounts — is critically important to our company and our customers. As a reminder, our company will never call and ask for your password, secret questions or account PINs. If you feel your account has been compromised, please reach out to us via chat at visible.com. —Visible’s Wednesday statement, posted to Reddit
Reach out via chat? Make that a nope, according to customers who reported that they’ve been unable to get through on chat, including this Twitter user:
I'm trying to get through on the chat and can't. Whoever changed my email address also ordered a phone
— Debbie Ondrasek (@dao0815) October 12, 2021
Another Reddit user likened Visible’s customer service to a dumpster fire.
Visible Wireless is owned by Verizon and runs on its parent company’s brawny 4G LTE network. It offers one thing: cheap, all-you-can-eat data plans. “All-digital” means it doesn’t have brick-and-mortar stores.
Visible’s subscribers and popularity have exploded over the past year, helped by ads featuring Kevin Bacon hawking it to everybody within X degrees of Kevin Bacon, from his dentist to a stunt double engulfed in flames.
Sayonara, and Thanks for the iPhones
In most of these cases of hijacked Visible accounts, the email address associated with the account has been reset by an unknown attacker who then uses the account’s payment method to order a phone.
“My account got hacked and they shipped out a [sic] iPhone 13 worth 1k that was taken from my PayPal,” one Reddit user wrote. Another said, “I literally signed up for Visible yesterday, and bought a [sic] $812 iPhone through their website. I woke up to an email this morning telling me that the email address associated with my account has been changed. […] 7 hours later I got an email saying the shipping address on my account has been changed, and no, I still wasn’t able to log in.”
Just a Weensy Hiccup, Visible Said at First
On Monday, when the complaints first started to flood in, Visible said that only a “small number” of accounts were edited without authorization, and that it was “working hard to take protective steps to secure these accounts.”
From Visible’s Monday statement on Reddit: “We don’t believe that any Visible systems have been breached or compromised, nor that this unauthorized access to your Visible account is ongoing.”
The story was first picked up by XDA Developers, which spotted the reports on Reddit’s Visible subreddit and on Twitter. One such, from Tuesday:
@Visible I was just hacked! They sent themselves a phone and changed my address! Urgent!’ How do i@stop this!!!! HURRY!!
— Kelley (@ksmrz77) October 12, 2021
Apparently, This Isn’t Over
Unfortunately, as of Thursday, customers were still complaining about being unable to get through to Visible on chat and said that the attack was still ongoing.
“My addresses were just changed in my account within the last hour, then I found this subreddit. What a mess,” one Reddit user said on Thursday morning. “Glad I found this thread. Yes the hacking is still happening. Trying to contact Visible chat agent now.”
Why no MFA?
Ripped-off customers have been complaining about Visible’s apparent failure to offer multi-factor authentication (MFA) to protect accounts. Not that MFA is a cure-all, mind you: Weak challenge questions by customer service reps have made it easy for fraudsters to hijack a phone line and bypass MFA to breach accounts, in so-called SIM-swap attacks.
Still, OWASP lists MFA as the strongest protection against credential-stuffing attacks – attacks that entail threat actors testing credentials that they’ve sucked up from breaches at other sites, in the hopes that users will do what users do: reuse email/password pairs.
Threatpost reached out to Visible’s parent company, Verizon, for specifics on the “protective steps” it said that it had implemented to shield affected accounts and to prevent future unauthorized account access. For example, going by OWASP’s list of protections, Visible could have chosen to implement any of these defenses:
- MFA
- Secondary passwords
- PINs
- Security questions
- CAPTCHA
- IP block-listing
- Device fingerprinting
Verizon didn’t immediately get back to Threatpost.
Change Your Visible Password
Visible is handing out standard-issue password hygiene instructions, asking users to change their passwords to something strong and unique. Unfortunately, during what seems to be an ongoing barrage of assaults on accounts, users have complained that the change-password function hasn’t been working – though the issue seems to have been rectified as of Thursday morning.
In addition, the company also announced updates to its purchasing process, which will now require specific user interaction.
Moving forward, any purchases will require you to re-validate your payment information as an added security measure. If there is a mistaken charge on your account, you will not be held accountable, and the charges will be reversed. —Visible
Researchers: A Plan’s Not Cheap if It Doesn’t Stop Bogus iPhone Purchases
Visible’s a hot-hot-hot carrier, thanks to its plans starting at a measly $25. But that’s not really a bargain if one can’t protect your account with MFA, security practitioners told Threatpost.
Bill Lawrence, CISO at SecurityGate, noted that the lack of MFA is, in this case, like an invitation for free iPhones: “Utility accounts, like cellphones or electricity, often require payment methods to be associated with a customer account. This scenario sounds like the attackers could change account access and treat themselves to new iPhones with the victim’s credit,” he said via email.
Lawrence advised customers to not only look for MFA when choosing a carrier but also to keep the business’ hands off of bank-account details: “When setting up these types of accounts, first and foremost, look for multi-factor authentication options and enable them. Also, be wary of linking bank accounts directly, and if you’re using a card, credit cards have better fraud protection than debit cards.”
As well, Lawrence said to never click on those little boxes websites present, prompting users to save their credit-card information to “make the next purchase easier.”
“That puts your information out there to be lost in each company’s future breach,” he said. “Use a password manager or your browser instead. And regularly keep an eye out for other fraudulent activity in your accounts.”
You Have to Make the Data Useless
Ruston Miles, founder and cybersecurity advisor at Bluefin, suggested that securing data isn’t all about protecting the perimeter these days, given how many ways attackers have devised to blow it up. A business’ security perimeter is still important, but the focus should also be on “making what’s inside that perimeter absolutely useless,” he said.
He’s talking about encryption: hashing and salting passwords, and also using tokenization to mask the data. “We call this devaluing the data; it is essentially taking all sensitive customer data, like login details, and encrypting or tokenizing it or both, depending on the business use case,” he commented.
“Encryption and tokenization masks the data so that it is not readable and therefore, not saleable on the Dark Web,” Miles said. “No business or organization will ever be able to 100 percent prevent a data breach, but they can prevent the breached data from being compromised…It’s like the old westerns where the robbers steal the safe from the bank, only to find out later that the safe is too strong for them to break into.”
Check out our free upcoming live and on-demand online town halls – unique, dynamic discussions with cybersecurity experts and the Threatpost community.