A software vulnerability is a weakness in an operating system or application that can be exploited by an attacker to invade an IT network. When publicly disclosed, these software vulnerabilities are usually assigned a CVE identifier. CVE is a popular term when referring to a vulnerability, and 50 to 60 CVEs are discovered every day on average.
Clearly, vulnerabilities are increasing rapidly, challenging IT security teams. Furthermore, over 40% of discovered vulnerabilities have no CVE identifier assigned and can be easily exploited by cybercriminals. These vulnerability loopholes allow unauthorized access to the network, resulting in ransomware and malware attacks.

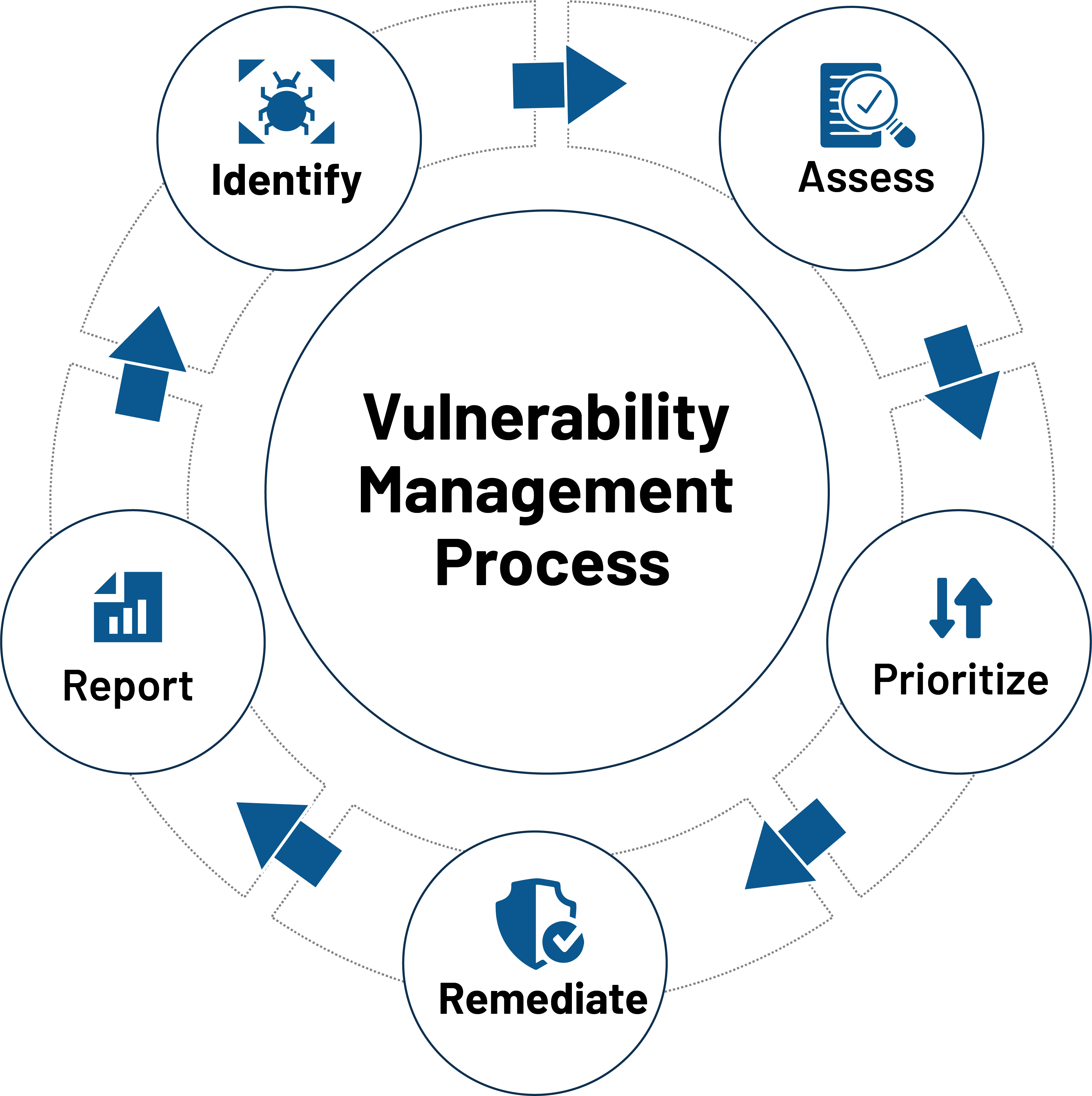
IT Security teams must implement a seamless vulnerability management process to prevent cyber attacks. They should continuously identify the vulnerabilities in their network, assess them thoroughly, prioritize them based on their severity, remediate them with relevant patches, and report all the data for strategic analysis.
It’s evident that CVEs or software vulnerabilities are a critical security loophole, but are these the only form of vulnerabilities attackers’ look out for? To answer this, we need to rethink vulnerabilities from the standpoint of an entire attack surface.
Are Software Vulnerabilities the Only Vulnerability in the Attack Surface?
CVEs or software vulnerabilities contribute only to a part of security risks in the IT vulnerability landscape. The attack surface comprises numerous vulnerabilities from a misconfigured firewall policy, unavailability of antivirus, unauthorized applications, lack of visibility over scheduled tasks, unwanted services and ports, hidden assets, and publicly discoverable files to numerous security control deviations and anomalies.
All these vulnerabilities and security risks are as threatening as a software vulnerability and can easily open gateways for an array of cyberattacks. IT security teams should look beyond CVEs and software vulnerabilities and start managing these security risks to attain a strong security posture and combat attacks.
Top Security Risks in the IT Security Landscape
Here are the top security risks that are as threatening as a software vulnerability and need to be considered as a vulnerability in the IT security landscape.
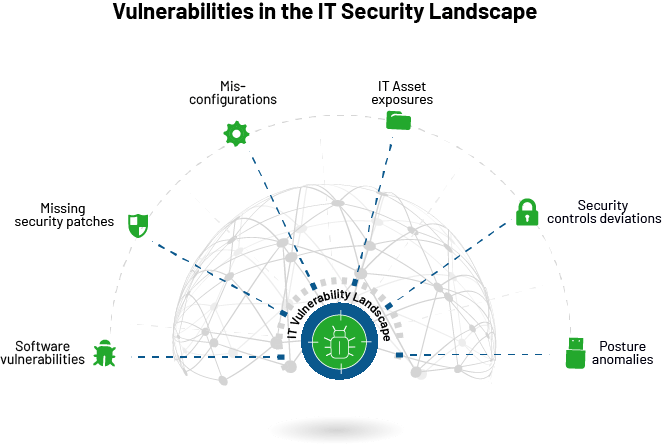
- Software Vulnerabilities: Software vulnerabilities are an IT network’s most critical security risks. Although they receive a lot of attention from security teams, they are still prevalent in huge numbers inside a typical IT infrastructure. While managing the other security risks, IT security teams must bring in a continuous and automated process to quickly detect and remediate software vulnerabilities.
- Misconfigurations: Security misconfigurations are inaccurately configured settings that leave an organization’s IT infrastructure at risk. Although security misconfigurations are not a part of an application or an operating system, they control the settings that make applications and operating systems run. For instance, a weak system password or weak encryption is a security misconfiguration that can open doors for numerous attacks, including brute force attacks.
- IT Asset Exposures: IT security teams should have complete and continuous visibility over the IT infrastructure. Any malicious entry of IT assets will disrupt security to a large extent. For instance, using unauthorized applications or devices will cause a huge threat to an organization’s security, inviting attacks like data thefts. Likewise, shadow IT, end-of-life and end-of-support software, and unwanted ports and services must be identified in the network and worked upon.
- Missing security patches: Missing patches are one of the crucial security risks in an IT network. Many attacks, including the infamous WannaCry ransomware, were due to a missing patch that was not applied on time. Apart from fixing vulnerabilities, patches play an important role in keeping systems stable, up-to-date, and safe from cyberattacks. It is essential to patch all operating systems and third-party applications continuously to safeguard your network from potential attacks.
- Deviation in security controls: Numerous security controls must be implemented in a device for adequate security. If these security controls are not configured properly, they might lead to security mishaps. For example, crucial security controls like antivirus and firewall should always be enabled. Any error in these settings or even if they are accidentally disabled, it serves as an alarming security loophole in an IT network.
Like the above security risks, security deviations and posture anomalies are present in an IT infrastructure that are as alarming as a software vulnerability. Attack surface reduction cannot be achieved only by managing CVEs. All the vulnerabilities and security risks discussed above must be managed rigorously to minimize attack surfaces and combat cyberattacks.
Again, opting for different solutions to manage all these vulnerabilities and security risks will only create chaos and complexities. IT security teams should start looking for a solution that automatically detects and remediates vulnerabilities, IT asset exposures, misconfigurations, security control deviations, and posture anomalies from a single place. Only a tool that treats all these vulnerabilities equally can meet today’s IT security demands and pave the way for a threat-free IT landscape.










