Researchers are warning that an old Twitter API still used by popular iOS mobile apps that could be abused as part of a man-in-the-middle attack. It could be used to hijack Twitter accounts and compromise other third-party apps that are linked to the same “login with Twitter” feature.
According to researchers with Germany-based Fraunhofer SIT, the culprit is a flawed TwitterKit library that was replaced by Twitter about a year ago. However, a review of the 2,000 most popular German iOS mobile apps revealed that the bad code is sill being in use by 45 applications and impacting millions of German users.
Worldwide the number of apps running the buggy Twitter Kit framework could be closer to tens of thousands, researchers said.

The flaw, tracked as CVE-2019-16263, is described as a bug in “the Twitter Kit framework through 3.4.2 for iOS does not properly validate the api.twitter.com SSL certificate. Although the certificate chain must contain one of a set of pinned certificates, there are certain implementation errors such as a lack of hostname verification.”
Twitter deprecated the Twitter Kit library code in October 2018. At the time, it asked developers to switch to alternative libraries. However, it left old code on its GitHub repository with no indication to users the code could be used in attacks, said Jens Heider, head of mobile security with Fraunhofer SIT.
 “The Twitter GitHub library still contains the malicious code,” Heider told Threatpost. “We are concerned that because the apps using the code appear to be working fine, developers will neglect updating their apps to a secure Twitter library.”
“The Twitter GitHub library still contains the malicious code,” Heider told Threatpost. “We are concerned that because the apps using the code appear to be working fine, developers will neglect updating their apps to a secure Twitter library.”
While not singling out specific applications by name, Heider said affected apps include newsreaders and many other services or applications that allow a user to login via their Twitter Access Token: “If an attacker is able to gain access to the (Twitter) OAuth token, they are able to use it to post to the targets Twitter account, read past private messages and like and retweet the tweets of other users.”
The issue stems from the way TwitterKit for iOS checks received certificates to ensure they have a corresponding public key. A TwitterKit is an open source software developers kit (SDK) used by mobile apps for displaying tweets, authorizing Twitter users and linking to the Twitter API, according to Twitter.
“They wanted to increase the security by implementing a public key pinning of trusted root certificate authorities (CA), such as VeriSign, DigiCert and GeoTrust. So they created [an] array with entries of 21 public key hashes for the CAs,” researchers wrote in a breakdown of their research.
They explained that the domain name of the leaf certificate is not verified by iOS. Because it’s not verified, any valid certificate (of the 21) with a public key hash, is accepted by the vulnerable app.
“An attacker with a valid certificate for his own domain, issued by one of these CAs, can use this certificate for man-in-the-middle-attacks against apps communicating via the Twitter Kit for iOS with api.twitter.com,” wrote the researchers.
Heider said the attacker could leverage this bug to use the Twitter OAuth tokens to login to third-party services that support the Twitter OAuth token framework. OAuth is an open standard used as a way to grant websites or applications access to data on other websites without giving them the passwords.
Researchers said they contacted Twitter in May 2019, notifying them of the vulnerable API. “Twitter acknowledged the finding, but as the library already was deprecated they did not provide a fix,” Heider said. Instead, Twitter has replaced the Twitter API code with an updated version.
“We would have liked to have seen some communication about the flaws that are in this library used by so many applications,” he said.
Twitter has not responded to a request for comment to this story.
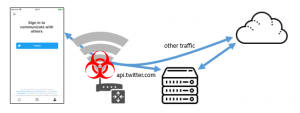
In order to exploit the vulnerability, researchers said, an adversary would first need to take control of a Wi-Fi access point. Next, a victim would log into the rogue wireless network, and then the attacker could capture the Twitter OAuth token for a user session.
The attack scenario includes a replay attack using the Twitter OAuth token to gain access to the primary Twitter account and also other third-party accounts and services that support the “login with Twitter” feature.
“Such issues are … common, which illustrates the need to check for vulnerable or outdated third party code,” wrote Fraunhofer SIT.
Researchers will formally present their work at the security conference it-sa 2019 in Nuremberg, Germany on Tuesday.
What are the top cyber security issues associated with privileged account access and credential governance? Experts from Thycotic will discuss during our upcoming free Threatpost webinar, “Hackers and Security Pros: Where They Agree & Disagree When It Comes to Your Privileged Access Security.” Click here to register.










