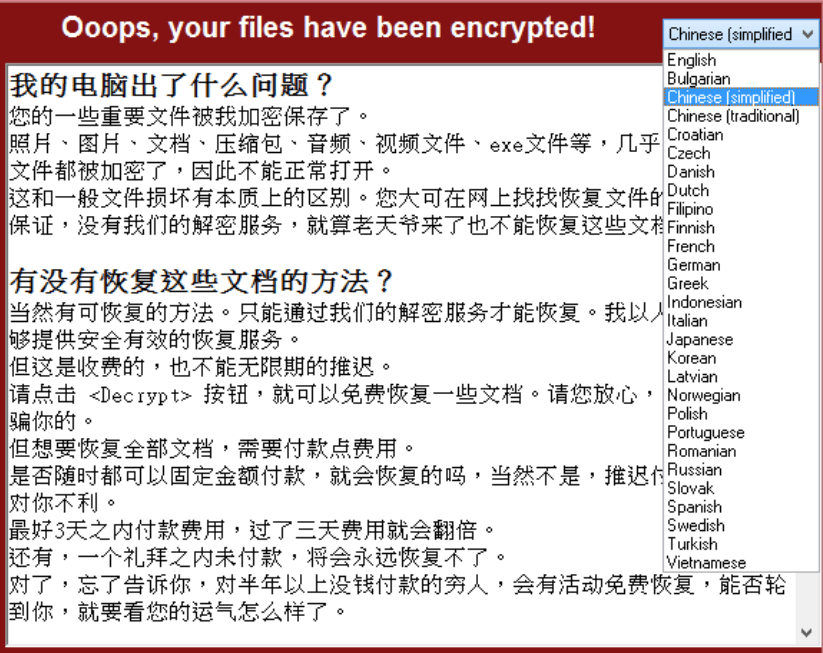
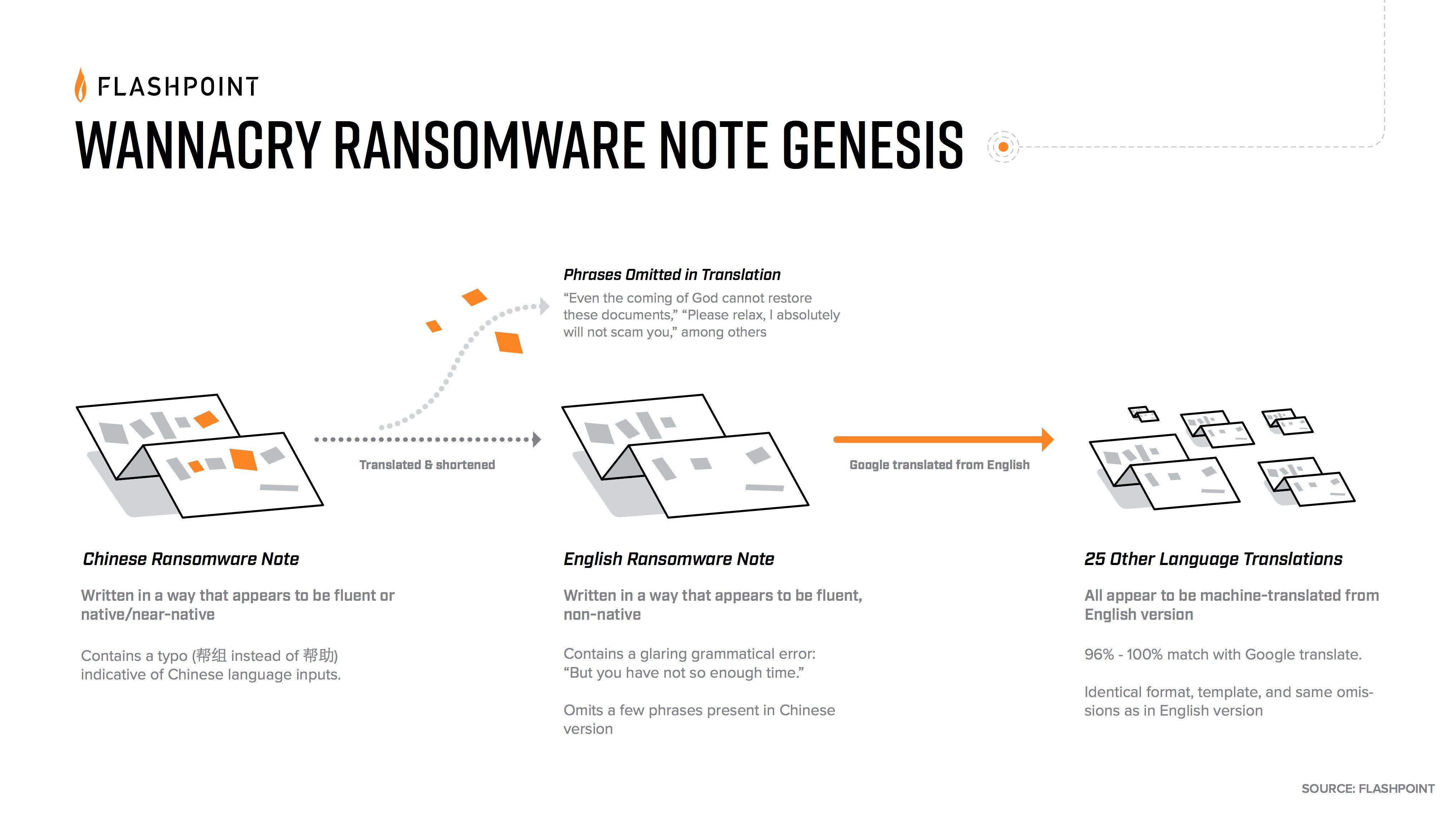
The WannaCry ransom note was likely written by Chinese- and English-speaking authors, adding more intrigue to the investigation into whether it was indeed a North Korean APT using stolen NSA exploits to spread ransomware worldwide.
Analysts at Flashpoint, including some fluent in Chinese, said the Simplified and Traditional Chinese notes differ significantly from the others and that it was likely the original note. The English note was then the source note for the remaining translations and was flushed through Google Translate to create them. The notes demanded $300 USD in Bitcoin for the safe return of victims’ encrypted files.
Many of the notes, Flashpoint director of Asia-Pacific research Jon Condra said, contained glaring grammatical errors that a native would not make. Ironically, the version of the note written in Korean was among the most poorly translated.
“It was interesting to us and we were kind of shocked after hearing the links to the Lazarus group that the Korean note was so badly translated,” Condra said. “That could be intentional, or maybe the person who wrote it didn’t speak Korean.”
Condra said the analyst who looked at it said it was about 65 percent correct and there were some basic mistakes made in the translation.
“Our conclusions don’t necessarily point to a particular geography where the actors may be located,” Condra said. “It does potentially point to the native tongue of the individual. Or this could have been written by someone highly fluent in Chinese but is not a native speaker and does not reside in China. There is a large Chinese diaspora around the world that would be capable of writing this, in theory. It’s not enough to point back to mainland China.”
Attribution is the most difficult challenge in the investigation of cybercrime and nation-state activity. The links to Lazarus began May 15 when Google researcher Neel Mehta tweeted out a chunk of code found in an early version of WannaCry that was also found in code used by Lazarus.
Lazarus is a state actor believed to be responsible for the Sony Pictures Entertainment hack in 2014, the Dark Seoul wiper attacks in South Korea a year prior, and last year’s SWIFT banking attacks in Bangladesh. Researchers at Kaspersky Lab and Symantec have also confirmed the similarities in the code Mehta found, adding further credence to the thinking the North Koreans may have been behind the ransomware outbreak.
“Having only had WannaCry for five days, I think it’s important to understand that this is only a lead, and not a simple lead,” Kaspersky Lab researcher Juan Andres Guerrero-Saade said last week. “It’s not necessarily easy to just replicate a very specific function of code from a very obscure piece of malware from two years ago that you only put into version 1.0 and then removed.”
Flashpoint too was hesitant to cement links between WannaCry and any actor, adding that it’s possible some members of the Lazarus group speak Chinese, are Chinese, or are North Korean who either studied in China or work in China given the better connectivity in that country.
“This is just one data point to go into the attribution puzzle,” Condra said. “I do think this might force us to rethink our assumptions about North Korean cyberactors. You might think that whatever they put out or they write is going to be in Korean, but that’s not necessarily the case. The relationship between North Korea and China, especially in intelligence domains, is probably much more complicated than widely appreciated. In this case, I don’t think this necessarily points away from North Korea. The technical analysis that’s been done by other researchers seems strong. This doesn’t contradict those findings, but adds to them.”
Flashpoint said the ransom notes written in Simplified and Traditional Chinese characters are identical and contain more information and colloquialisms than other notes. There’s also a typo in the Chinese version of the word help where the author wrote bang zu in characters, rather than the correct bang zhu, indicating this was manually input rather than translated, Flashpoint said. The text also includes a grammatical error that was likely caused by an autocomplete, as well as certain phrases—for the word “week” and “antivirus”—used more commonly in South China, Hong Kong, Taiwan and Singapore, rather than Korea.
“We started throwing some of the foreign language [notes] into Google Translate and we realized some of them are straight-up copy-paste [of the English version],” Condra said. Most of the notes, aside from the Chinese, contain similar word counts and are around 96 percent identical in content, Condra said.
“The Chinese one is written in a very fluent fashion,” Condra said, adding that the typo in the note is highly indicative of it being physically typed. “An automated service would not have made that mistake because that character doesn’t fit there. That was the linchpin where we sat back and said this looks like the Chinese was the source document and the English looked like the boiled-down version of the Chinese note.”