LAS VEGAS – Researchers at Black Hat USA 2019 demoed how known vulnerabilities in WhatsApp could still be exploited in several attacks that manipulate chats.
Facebook-owned WhatsApp is a popular end-to-end encrypted messaging platform with at least 1.5 billion users. Researchers with Check Point last year disclosed three different attack methods that can let attackers change chat users’ messages, make private messages public and change sender identities.
And so far, two of the three attack methods are still open to attack, researchers said.
“WhatsApp end-to-end encryption ensures that only you and the person you’re communicating with can read what’s sent, and nobody in between, not even WhatsApp. However, we managed to reverse-engineer WhatsApp web source code and successfully decrypted WhatsApp traffic,” Check Point researchers Roman Zaikin and Oded Vanunu said in their Black Hat USA session on Wednesday, “Reverse Engineering WhatsApp Encryption for Chat Manipulation and More.”
After decrypting the WhatsApp communications, researchers found that the messaging platform uses the “protobuf2” protocol for encryption. By converting this protobuf2 data to Json, researchers were able to see the actual parameters for the messages that were sent and manipulate them in order to spoof messages.
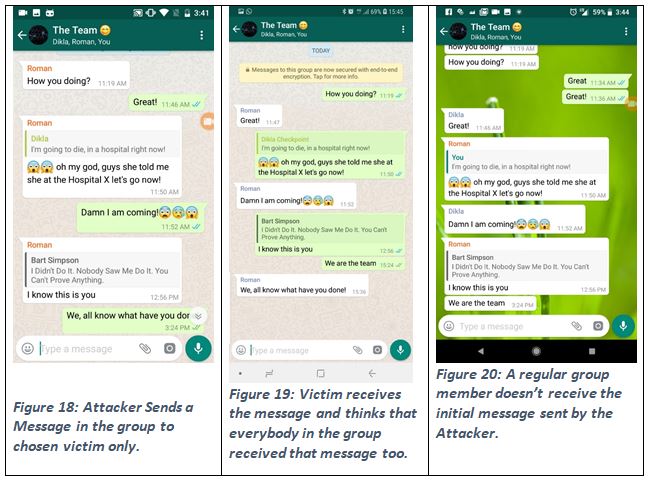
Using this method of reverse engineering coupled with social engineering, researchers were able to launch three attacks via WhatsApp:
- Altering the text of a chat user’s reply, essentially putting words in their mouth;
- Using the “quote” feature of a group chat to change the identity of the sender (even if they are not part of the group chat);
- And ending a private message to another group chat user that is disguised as a public message for all, so that when the recipient responses their response is visible to everyone in the conversation.
The latter issue has been fixed by WhatsApp, while the first two glitches remain exploitable, researchers said.
“During the process we unveiled new vulnerabilities that could allow threat actors to intercept and manipulate messages sent in both private and group conversations, giving attackers immense power to create and spread misinformation from what appear to be trusted sources,” the duo said.
These attacks have various malicious purposes for threat actors: For instance, in the third attack vector (above) a bad actor could manipulate a certain member of a group chat and trick them into revealing information to the group that they may otherwise not want them to know. Or, by altering the text of a recipient’s reply, a bad actor could incriminate a person unfairly, or close a fraudulent deal.
Meanwhile, WhatsApp has had its fair share of privacy vulnerabilities this year. In May, a zero-day vulnerability was exploited by attackers who were able to inject spyware onto victims’ phones in targeted campaigns; while in July, researchers found faulty developer coding that allows cyberattackers to intercept media files sent on the Android versions of the service.
Facebook did not have a statement when reached for comment.
Black Hat USA 2019 has kicked off this week in Las Vegas. For more Threatpost breaking news, stories and videos from Black Hat and DEF CON, click here.