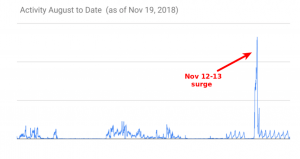
A massive malvertising campaign targeting iOS devices hijacked a whopping 300 million browser sessions in just 48 hours.
Researchers at Confiant recorded the campaign Nov. 12, and said that the threat actor behind the campaign is still active to this day.
According to researchers, those behind the malvertising campaigns typically inject malicious code into legitimate online ads and webpages, so when victims click those pages, they are forcefully redirected to a malicious page. In this case, the ad unit forcefully redirects mobile users to adult content and gift card scams.
Those included “forceful redirection to fake ‘You’ve Won a Gift Card’ or adult content landing pages,” Confiant CTO Jerome Dangu said in an analysis of the campaign, published Monday.
In this specific case, when users visited a web page, the malicious ad would execute embedded obfuscated JavaScript. Victims were then redirected to an array of malicious landing pages, including happy.hipstarclub[dot]com or happy.luckstarclub[dot]com. These landing pages typically impersonated Google Play apps, making them appear more legitimate, researchers said.
The pages would typically then try to phish visitor data in order to commit affiliate marketing related fraud and or steal personal identification data, such as email, address, revenue information, purchase intent, and more, Dangu told Threatpost.
“The session is hijacked without user interaction,” Dangu said . “When a user is given the opportunity to win $1,000, there will be some people falling for it. And at the scale of the scheme, this is very profitable for the attacker.”
The Scale
Malvertising campaigns are no rare occurrence. In July, for instance, the AdsTerra online advertising company was leveraged as part of a malvertising campaign that involved at least 10,000 compromised websites.
This recent campaign, which targeted primarily iOS users in the United States, stands out due to its scale, Dangu told Threatpost.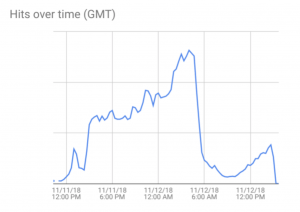
While Confiant blocked over 5 million hits, the company estimated the total amount of impressions served to publishers to be over 300 million impressions during the 48-hour period.
To put that into perspective, 2017’s largest malvertising campaign, launched by threat actor Zirconium, wracked up one billion impacted browser impressions – throughout an entire year.
Dangu said that almost 60 percent of Confiant’s customers were impacted by the campaign, and “if you were browsing your favorite websites with your iPhone on [the impacted dates], there’s a good chance you were exposed to it.”
Applying a conservative 0.1 percent conversion rate to the 300 million impacted browser sessions, that could amount to at least 300,000 victims, said Dangu.
“Each of these victims is worth multiple dollars to the attacker,” Dangu told Threatpost. “Since our telemetry indicates that the attacker spent about $200,000 to run the campaign, we believe the attacker raked in to the tone of $1 million in 2 days.”
The Bad Actor
While there are dozens of these malvertising groups, “this one stands out by the scale of the attack they were able to deploy,” Dangu told Threatpost. “Although we attribute continuous activity to this attacker since at least August, we don’t have any more visibility on who is behind this.”
What Dangu does know, he said, is that the bad actor has been active since August – but with much lower visibility to tier-1 publishers and using smaller exchanges.
Researchers observed the attacker targeting the US – but also running malvertising campaigns in other locations, like Australia and New Zealand.
The bad actor is still active, researchers said, and have simply been pivoting to different ad networks on an on-going basis.
“We expect they will continue to leverage programmatic advertising platforms to maintain their operations for the foreseeable future,” Dangu said.