Researchers have developed a method for bypassing Windows Defender that will allow any malware to execute on a Windows machine. Microsoft, meanwhile, has told the experts that it does not see this as a security issue and will not address the problem in its native antimalware protection.
A request to Microsoft for further comment was not answered in time for publication. Microsoft said in a response provided to Threatpost:
“The technique described has limited practical applicability. To be successful, an attacker would first need to convince a user to give manual consent to execute an unknown binary from an untrusted remote location. The user would also need to click through additional warnings in order to grant the attacker Administrator privileges. Should the attacker successfully convince a user to carry out the manual steps mentioned, Windows Defender Antivirus and Windows Defender Advanced Threat Protection will detect further actions by the attacker.”
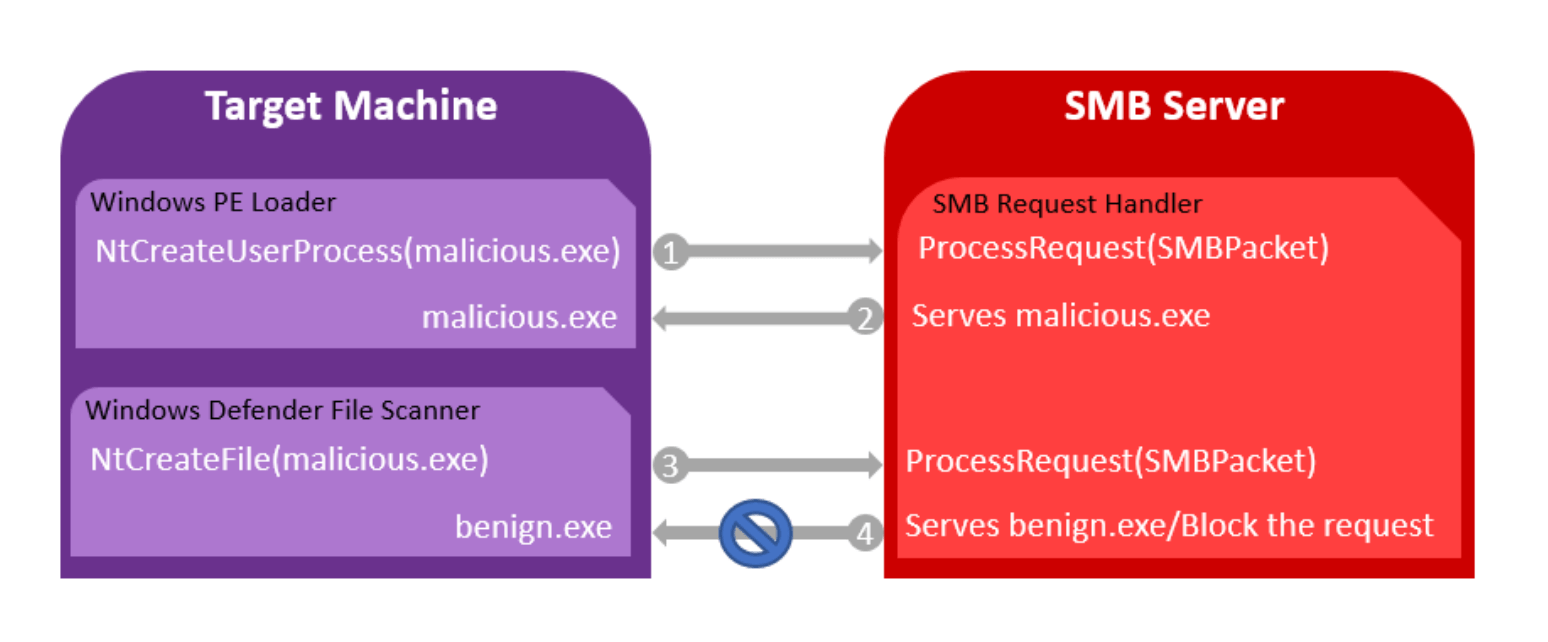
The bypass involves the use of a custom-built SMB server, tricking Windows Defender into scanning a benign file, and executing a malicious one instead that is passed to the operating system.
CyberArk cyber research team leader Doron Naim and Kobi Ben Naim, senior director of cyber research, told Threatpost that their attack, which they call Illusion Gap, may also affect other commercial antivirus products.
Ben Naim said such an attack would likely be of interest to an advanced attacker who could use this type of attack as a first stage in order to gain the ability for lateral movement or to exploit other vulnerabilities.
An attacker would first need to trick the victim into executing an exploit hosted on the malicious SMB share. The attacker would serve different files from their custom SMB share to the Windows PE Loader—which encapsulates information in order for the OS to run an executable—and to Windows Defender. Once PE Loader creates the process to execute the file and requests it from the SMB server, the attacker would serve the malicious file. When Windows Defender wants to scan the file, it is served a different and benign file which Windows Defender will scan as clean. PE Loader will then execute the malicious file it requested, CyberArk said.
“Once an attacker puts the malicious file into the share, the attacker can control which file to notify the Windows Defender that it will run,” Naim said, adding that this situation stems from a design issue related to the Windows Defender call. “Since you are sitting in the SMB server side, you are able to understand if you’re getting addressed by the operating system or by Windows Defender. Once the attacker on the SMB side actually identifies that Windows Defender wants to read his file, they can hand it another benign file instead of the malicious file. The actual file that runs in the OS at the end of the procedure is the malicious file.”
Naim also said that the script they built can also drop the request to Windows Defender and it would fail to open.
Microsoft, meanwhile, said in a statement provided to CyberArk that since the attack requires a user to trust and run malicious code from an untrusted SMB share that it “doesn’t seem to be a security issue but a feature request.” That request, Microsoft told CyberArk, was forwarded to its engineering group.
“That response is quite ridiculous. If you develop a security product, the first and last thing that product should do is give you more security,” Ben Naim said. “If you decide that every process executable has to go through an antivirus scan before it’s executed, if you cannot scan the file, the default should be that the process is not executed. This is a consideration every security vendor should have.”
Naim said this behavior is just the opposite and that even if Windows Defender is not able to scan a file, it would still allow the process to execute. CyberArk, meanwhile, said it has already privately disclosed similar issues to other security vendors.
“If you are able to identify which requests are coming from native antivirus and which are coming from native operations from Windows, you can do same trick for other antivirus,” he said.