A cybercrime gang has been running roughshod over the gaming industry for years using malware signed with valid digital certificates to steal source code and valuable in-game currency for a number of popular online games.
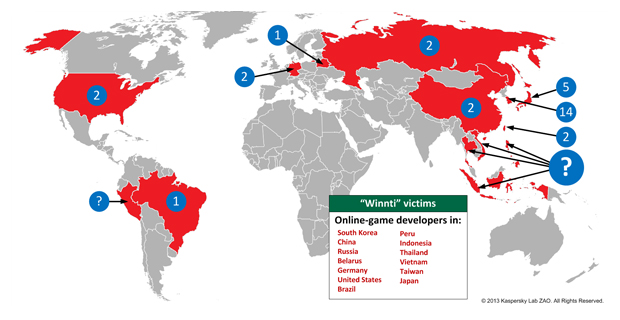
Researchers at Kaspersky Lab this morning published a report on the Winnti gang, which has been active since 2009 targeting more than 30 gaming companies located primarily in Southeast Asia and was successful in launching the first Trojan, in this case the Plug X remote administration tool (RAT), on a 64-bit version of Windows signed with a valid cert.
The Winnti group stole game “runes” or “gold” which are used by players to convert the virtual gains into actual money. The stolen source code was used to search for vulnerabilities in the game that were ultimately exploited to accumulate in-game money. It was also used by the attackers to deploy their own pirated versions of gaming servers.
Kaspersky experts said the group is still active and the company is working with certificate authorities and gaming companies to find more compromised servers and ultimately revoke any additional stolen certificates; to date, more than a dozen stolen certificates have been found related to the Winnti operation.
Some of the stolen certificates were not only used in attacks against gaming companies, but also in attacks against Tibetan and Uyghur activists.
“Either this group has close contacts with other Chinese hacker gangs, or it sells the certificates on the black market in China,” said Kaspersky Lab in a research report.
Companies such as ESTsoft, MGAME Corp and KOG among others in South Korea, Japan and China lost legitimate certificates to the Winnti group; these companies build popular Massively Multiplayer Role Playing Games. It was an investigation into one of these MMRPG games that led to the discovery of the Winnti operation. A game publisher hired Kaspersky to investigate a large number of players’ computers infected by a Trojan linked to a KOG-produced MMRPG. Kaspersky concluded that the infections were an unintended consequence, and that the attackers were targeting the gaming companies and not players.
Researchers found a malicious DLL library acting as a rootkit that was compiled for a 64-bit Windows environment and signed with a legitimate certificate. The payload was the Plug X RAT, which gave the attackers remote control over infected computers, the first such incident on a 64-bit computer. Plug X had also been used in attacks against Tibetan and Uyghur activists. The KOG certificate used in the attack was issued by VeriSign and has since been revoked, Kaspersky said.
In addition to gaming companies in Asia, a few other infections were found at companies in Europe, South America and the United States. Likely the malware was spread by game developers collaborating with colleagues or partners in the other regions.
Kaspersky researchers said they believe the attacks started with a spear phishing email sent to a few companies that contained a malicious PDF attachment exploiting vulnerabilities in Adobe Reader. These attacks were also used against Tibetan and Uyghur activists, as well as companies in the aerospace industry, Kaspersky said
While no zero-day exploits have been spotted in any of these attacks, the attackers have been able to use malware to pivot inside of organizations, elevate their privileges and land on servers hosting the information they targeted. Stolen data was sent to command and control servers that manage bots hosted in South Korea, Russia, Japan and the U.S., used to infect gaming servers. In fact, a variety of public Internet hosts were used to store encrypted control commands.
Several clues point to attackers in China behind the scheme, including the use of Chinese Simplified GBK coding used in the resource section of malicious modules and Chinese text used in the modules’ report messages. A number of Chinese users’ profiles were linked to control messages posted on blogs and forums linked to the attack.
The Winnti gang also used custom-built malware targeting particular services on the gaming companies’ servers. The malware injected itself into the process and was subsequently able to conceal itself as well as change the game in order to collect game currency illegally.
“We believe that the attackers that currently form Winnti group used to be members of Chinese underground hacking teams in the past,” the Kaspersky report said. “It is most likely that they were attacking various entities including businesses and individuals as members of those groups, but united in Winnti group, they have started doing that routinely, systematically and under well-organized management.”









