A new Windows malware has emerged that makes disks unusable by overwriting the master boot record (MBR). It takes its cue from the COVID-19 pandemic, calling itself simply “Coronavirus.”
Overwriting the MBR is the same trick that the infamous NotPetya wiper malware used in 2017 in a campaign that caused widespread, global financial damage.
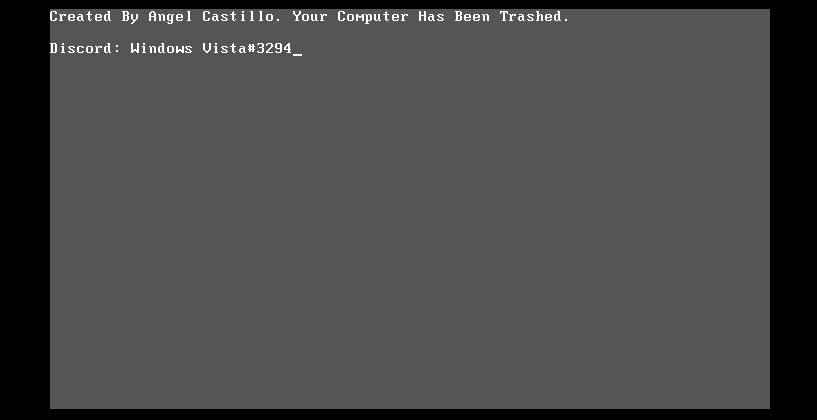
Worryingly, according to the SonicWall Capture Labs Threat Research team, the fresh malware strain is also a destructive trojan — though not as destructive as other wipers. And like its namesake, there’s no obvious cure. In a posting on Tuesday, researchers explained that victims of the Coronavirus trojan find themselves with a gray screen and a blinking cursor with a simple message, “Your computer has been trashed.”
The novel coronavirus, and the disease it causes, COVID-19, has provided a depth of fodder for cybercriminals looking to capitalize on the global concern around the pandemic. For instance, a recent spate of phishing attacks has used the promise of financial relief due to the disease as a lure. However, the operator behind this malware takes it one step further, going so far as to take the coronavirus as its name and infection theme.
As far as that infection routine, the malware can be delivered in any of the usual ways – as a malicious email attachment, file download, fake application and so on.
Upon execution, the malware starts its process by installing a number of helper files, which are placed in a temporary folder. The malware cleaves tight to its pandemic theme: An installer (a helper file named “coronavirus.bat”) sets up the attack by creating a hidden folder named “COVID-19” on the victim machine. The previously dropped helper files are then moved there, in an effort to go unnoticed until its goal is achieved.
After that, the installer disables Windows Task Manager and User Access Control (UAC) in a further stab at obfuscation, according to the analysis. It also changes the victim’s wallpaper, and disables options to add or modify that wallpaper after the change is made. It also adds entries in registry for persistence, and then sets about rebooting to finish the installation.
The process run.exe creates a batch file named run.bat to ensure the registry modifications done by “coronavirus.bat” are kept intact during the reboot process, according to SonicWall.
After reboot, the infection executes two binaries. One, “mainWindow.exe,” displays a window with a picture of the coronavirus itself, with two buttons. At the top of the window, the victim is notified that “coronavirus has infected your PC!”
The two buttons read “Remove virus” and “Help.” The former does nothing when clicked; the latter brings up a pop-up that tells victims to “not wast [sic] your time” because “you can’t terminate this process!”
The other binary carries out the meat of the attack: It’s responsible for overwriting the MBR.
“The original MBR is first backed up in the first sector before it is overwritten with new one, [and the] MBR is overwritten with the new code,” according to the researchers.
Once the overwrite is complete, the victim’s display is changed to a simple grey screen delivering the bad news:
SonicWall told Threatpost in an email interview that it was able to analyze the sample after it was uploaded to VirusTotal. Thus, so far, there haven’t been many instances of “Coronavirus” observed in the wild, and little in known in terms of targeting or what the spreading mechanisms are for the mysterious new malware.
The team also told Threatpost that the good news is that this is not as dangerous as other wiper strains.
“Even if the MBR is not restored…data can still be accessed/recovered by mounting the drive,” the firm noted. “The MBR [also] can be potentially restored, but it is not easy and requires deep technical knowledge.”
Do you suffer from Password Fatigue? On Wednesday April 8 at 2 p.m. ET join Duo Security and Threatpost as we explore a passwordless future. This FREE webinar maps out a future where modern authentication standards like WebAuthn significantly reduce a dependency on passwords. We’ll also explore how teaming with Microsoft can reduced reliance on passwords. Please register here and dare to ask, “Are passwords overrated?” in this sponsored webinar.