A smattering of bugs, mostly cross-site scripting (XSS) and cross-site request forgery (CSRF) vulnerabilities, have been plaguing at least eight different WordPress plugins as of late.
A security researcher going by the pseudonym Voxel@Night published on Monday information regarding the vulnerabilities, including proof of concepts for all of them on his personal blog Vextious Tendencies.
The software company Ready! is responsible for developing three of the affected plugins that collectively have been downloaded almost 1.5 million times.
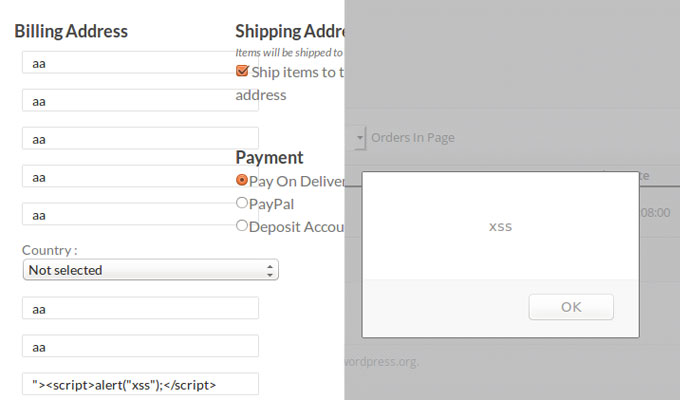
Most troublesome among them is a version (v0.5.0) of its eCommerce platform. The researcher points out that the plugin fails to sanitize any of its output/AJAX calls, something that can open it up to CSRF attacks, and subsequently, a total compromise.
Particularly of note is the fact that information end users supply when placing an order, such as their billing address, is later displayed unsanitized to administrators. Users meanwhile are met with an XSS notification.
Two other plugins put out by Ready! contain similar issues. A Google Maps plugin it oversees could let anyone update a site’s maps to point to random places, while a Coming Soon plugin, designed to let site visitors know when websites that are being worked on are completed, fails to contain malicious inputs.
Elsewhere, an issue with Easy Media Gallery, a plugin by GhozyLab that boasts that it’s the “#1 best selling gallery and portfolio plugin for WordPress” could lead to several CSRF vulnerabilities and let an attacker gain admin access to sites running it.
According to the researcher, another photo gallery plugin, WP Photo Album Plus, contains a stored XSS vulnerability.
Ironically what could be considered the least important vulnerability among the crop affects the most downloaded plugin, Contact Form, a relatively simple app that allows web developers to create a feedback page on their sites. Contact Form – – a plugin that boasts 2.3 million overall downloads – suffers from a bypass vulnerability that could let any user use AJAX functions. Voxel points out that the issue was initially brought up to the developer a year ago, in August 2013, but still, no changes have been made.
Almost all of the vulnerabilities stem from sloppy coding and a lack of nonces – arbitrary numbers used in cryptographic settings designed to thwart attacks.
When reached Tuesday, Alexey, the technical director and lead programmer for Ready! claimed the company had already submitted a fix for the eCommerce plugin, version 0.5.1, and was in the middle of addressing the vulnerabilities in the Coming Soon and Google Maps plugins.
WordPress plugin vulnerabilities have seemingly become more and more ubiquitous over the last several months.
Critical vulnerabilities in a popular WordPress mail plugin, MailPoet, could have opened sites using it up to a site takeover in July while in June, developers at TimThumb, a PHP-based image resizer, were forced to patch a zero day in its script that could have let attackers remove and modify files without authentication.
While not directly related to its plugins, WordPress announced earlier this summer that like many other online entities as of late, it plans to enable SSL, along with Perfect Forward Secrecy, to help bolster users’ security before 2014 is through.
Far and away the most popular blogging platform, upwards to 60 million websites, nearly a quarter of them belonging to the top 10 million, run WordPress.