The APT known as the Sednit threat group (also known as Sofacy, APT28 and Fancy Bear) has kicked off a fresh spearphishing campaign, that was spotted targeting government entities with the Zebrocy backdoor. The malware features a rewritten and newly-improved backdoor and downloader, indicating an ongoing evolution for the custom code.
Sednit has been around since 2004 and aims to steal information from victims — mostly in the political realm. It has been linked to Russia by the U.S. government, which attributed election-season hacking during the 2016 presidential election to the group.
The APT was most recently spotted sending spearphishing emails on Aug. 20, targeting both embassies and Ministries of Foreign Affairs in Eastern European and Central Asian countries.
Researchers with ESET on Tuesday warned that this latest campaign shows key changes in the APT’s approach – including an improved downloader that has new obfuscation techniques, and a backdoor rewritten in a new language and with a new screenshot-taking capability.
“New downloaders, new backdoor – the Sednit group has been active and is not letting their components get too old,” researchers with ESET said in a Tuesday analysis. “By looking at it, it seems that the Sednit group are porting the original code to, or reimplementing it in, other languages in the hope of evading detection. It’s probably easier that way and it means they do not need to change their entire TTPs.”
The Campaign
The latest Zebrocy campaign, which was first documented by Telsy researchers in August, targeted victims with a malicious email armed with an attached lure document.
The email itself, directed to at least one diplomatic institution of Eastern European and Central Asian countries (not specified by researchers), was blank and lacked any message components. However, it references a remote template (wordData.dotm) hosted on the Dropbox file sharing service – the use of which is “unusual for the group,” ESET researchers said.
After a victim opens the document in Word, it downloads the remote template (wordData.dotm) which contains malicious macros that are then executed. That macros then launch a long chain of downloaders, ending with a backdoor designed to infect and steal data from systems.
The main functions of this malware include taking screenshots of the victim’s desktop every 35 seconds and executing commands received from the Command and Control (C&C) server, amongst other information-stealing capabilities.
What’s New
When they first analyzed the campaign in August, researchers with Telsy had noted that the campaign uses a downloader written in the Nim programming language (a tactic first noted in a June campaign by Kaspersky researchers). In their more recent, Tuesday analysis, researchers with ESET detailed more changes that they noted both in the downloaders launched during the campaign as well as the end-result backdoor.
Two new details have been added to the downloaders in the August campaign. First, once downloaded onto the victims’ system the downloader now checks that the first letter of executed filenames have not changed, a move that researchers believe is likely used as an anti-sandbox trick. 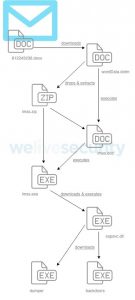 Second, the downloader reconstructs the download URL string so that correct letters in the string are replaced with placeholder letters. This is an obfuscation method as basic static analysis tools are unable to locate the URL string without the correct letters in place, researchers said.
Second, the downloader reconstructs the download URL string so that correct letters in the string are replaced with placeholder letters. This is an obfuscation method as basic static analysis tools are unable to locate the URL string without the correct letters in place, researchers said.
The downloader’s dynamic-link library payload (named ospsvc.dll) has also been changed to be rewritten in Golang, an open source programming language. This is different than other Sednit downloaders seen in the past, researchers said, which were developed in AutoIt, Delphi, VB.NET, C# and Visual C++.
“Sednit’s previous Golang downloaders have been described in detail by other researchers and it seems that Sednit’s developers have rewritten their previous Delphi downloader in Golang,” ESET researchers said. “Those earlier downloaders gather a lot of information about the victim computer and send it to their C2 server. However, this new one is quite light in terms of its data-gathering capabilities.”
Downloaders are used to download three pieces of malware: including two components that have not changed from previous campaigns (a dumper and a backdoor written in Delphi) — but also a third brand-new backdoor that is then executed on the victim’s machine.
The new backdoor has similar behavior to previous backdoors used by Sednit, which were written in Delphi. However, this new backdoor has instead been rewritten in the Golang programming language, and has new capabilities including an AES algorithm used to encrypt data on the system, the use of hex encoding for strings, and screenshot capabilities.
Other than these new capabilities the backdoor has an array of tasks that were seen in previous, Delphi-based samples: including file manipulation, screenshot capabilities, command execution and more.
The Zebrocy trojan was previously spotted in a June campaign by Kaspersky researchers targeting locations included Germany and the United Kingdom in Western Europe, who at the time noted that the campaign was using a new Nim downloader.
Moving forward, researchers recommend that email users are attentive when opening attachments from suspicious emails.
Interested in the role of artificial intelligence in cybersecurity, for both offense and defense? Don’t miss our free Threatpost webinar, AI and Cybersecurity: Tools, Strategy and Advice, with senior editor Tara Seals and a panel of experts. Click here to register.