A zero-day vulnerability is being exploited in the wild in targeted attacks against Windows users in the Middle East, researchers warned Thursday.
The Flash Player vulnerability (CVE-2018-5002), a stack-based buffer overflow bug that could enable arbitrary code execution, was patched earlier today by Adobe.
The vulnerability “allows for a maliciously crafted Flash object to execute code on victim computers, which enables an attacker to execute a range of payloads and actions,” researchers from ICEBRG’s Security Research Team, who was the first to report the discovered vuln, said in a Thursday post. It’s particularly dangerous because all that needs to happen for the bug to be triggered is for the victim to open a malicious file.
According to Adobe, CVE-2018-5002 was discovered by researchers from an array of organizations, including individuals from ICEBRG; 360 Threat Intelligence Center of 360 Enterprise Security Group; and Qihoo 360 Core Security. ICEBRG and Qihoo 360 both came out with posts analyzing the new bug.
The exploit uses a carefully constructed Microsoft Office document to download and execute an Adobe Flash exploit to the victims’ computers, according to ICEBRG researchers. The documents were sent primarily via email, according to Adobe.
First, the user would open a weaponized Shockwave Flash file. From there, the file downloads and executes the exploit to achieve code execution on the system.
The file then executes shellcode, which calls out to the attackers command and control servers and enables the threat actor to further control the victim machine.
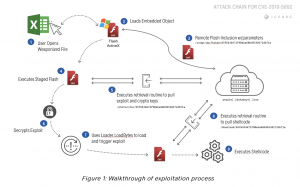 “Typically, the final payload consists of shell code that provides backdoor functionality to the system or stages additional tools,” ICEBRG researchers said.
“Typically, the final payload consists of shell code that provides backdoor functionality to the system or stages additional tools,” ICEBRG researchers said.
Both ICEBRG and Qihoo 360 found evidence that suggested the exploit was targeting Qatari victims, based on geopolitical interests.
“The weaponized document … is an Arabic language themed document that purports to inform the target of employee salary adjustments,” ICEBRG researchers said. “Most of the job titles included in the document are diplomatic in nature, specifically referring to salaries with positions referencing secretaries, ambassadors, diplomats, etc.”
Meanwhile, Qihoo researchers also said that “all clues show this is a typical APT attack.”
“The attacker developed sophisticated plans in the cloud and spent at least three months preparing for the attack,” Qihoo researchers said. “The detailed phishing attack content was also tailored to the attack target.”
Adobe dealt with another zero-day Flash vulnerability back in February, which was exploited by North Korean hackers.
The company on Thursday also patched another critical vulnerability (CVE-2018-4945) that enables arbitrary code execution; and two “important” vulnerabilities that could both lead to information disclosure, including one (CVE-2018-5000) Integer Overflow bug and an Out-of-bounds read glitch (CVE-2018-5001).
Microsoft did not respond to a request for multiple request for comment from Threatpost. The company posted a security update regarding the vulnerability on Thursday.
“In order to protect themselves users should immediately upgrade their Adobe Flash and disable macros in Microsoft Office,” Allan Liska, threat intelligence analyst at Recorded Future, told Threatpost.










