Zero Day Initiative (ZDI) awarded more than $1.5 million in cash and prizes to bug-hunters throughout 2019, it said, resulting in 1,035 security vulnerability advisories for the year.
Most of those advisories (88 percent) were published in conjunction with a patch from the vendor, Zero Day Initiative (ZDI) noted – just 127 were not.
The pace of bug discovery looks to stay steady. ZDI, a division of Trend Micro, announced that already, as of the end of January, it bounty program has published 154 advisories for 2020, affecting products from Apple, Cisco, Oracle, Microsoft and others.
Notable milestones for the year included the introduction of an automotive category to Pwn2Own Vancouver, the group’s annual hacking contest. In terms of bugs themselves, “[we also] saw [Windows user account control] abused for privilege escalation, had the Samsung handset exploited via baseband for the third Pwn2Own Tokyo in a row and disclosed a significantly impactful SharePoint bug later seen in active attacks,” ZDI’s Brian Gorenc wrote, in a blog post on Thursday.
2019 Bug Bounty Trends
From a trend perspective, Gorenc said that 2019 saw a shift towards more reports for high-severity flaws – rather than medium-severity bugs making the bulk of advisories as they have in years past. In all, there were 98 critical, 583 high-severity and 167 medium-severity bugs disclosed. That compares with 262 critical, 211 high-severity and 867 medium-severity bugs disclosed the year before.
At the same time, the number of low-severity advisories increased year-over-year, totaling 191 vs. 103 in 2018.
“The increase in low-severity CVSS cases reflects our commitment to information-disclosure cases,” Gorenc explained. “On their own, they aren’t as impactful. However, when combined with other vulnerabilities, they become an essential piece of an exploit chain. As exploits often rely on info leaks for sandbox escapes and other compromises, these humble info-disclosure bugs will continue to be worth [giving bounties for].”
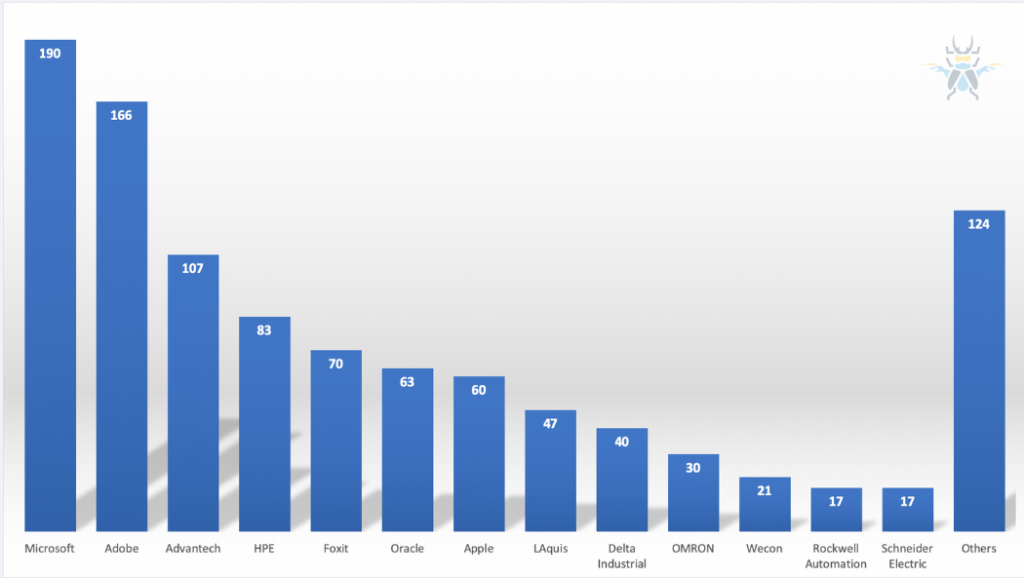
Unsurprisingly, Microsoft topped the list of advisories-by vendor, accounting for 190 disclosures.
“In years past, many of the Microsoft bugs we purchased were browser related,” Gorenc said. “We’re still buying plenty of those, but this year saw an increase in bugs affecting the OS as well. In particular, we had an increase in bugs impacting font parsing – both in the kernel and in the GDI+ library. The JET database engine also proved to be a popular target for researchers.”
Adobe was a close second, with 166 advisories published.
“Bugs in Adobe software used to be synonymous with Flash, but that’s no longer the case,” the researcher noted. “In 2019, two out of three Adobe bugs we purchased impact Acrobat and Reader. We did purchase a few Flash bugs, but we actually had more submissions for Photoshop than we did for Flash – five times more.”
Also notable is the fact that a little more than 30 percent of the published advisories impacted industrial control systems (ICS) products from vendors including Delta Industrial, Rockwell Automation and Schneider Electric. That’s a marked increase from the year before, he said, and 2020 could see an even bigger spike, given that ZDI kicked off Pwn2Own Miami in January dedicated to ICS bug-hunting.
When it comes to the types of vulnerabilities found in 2019, out-of-bounds (OOB) read flaws were the most common. Use-after-free (UAF) bugs were a close second; followed by OOB writes, stack-based buffer overflows and heap-based overflows.
A type of bug known as “improper neutralization of special elements used in an expression language statement” accounted for about 6 percent of the bounties issued. A.k.a. “expression language injection,” this type of server-side code injection vulnerability can allow attackers to completely compromise an application’s data and functionality, and often of the server that is hosting the application, according to a description at Portswigger.
The past year also saw an across-the-board increase in deserialization bugs, “whether they were submitted to the program, used at Pwn2Own or found in the wild,” Gorenc wrote. “This trend will likely continue in 2020, although it is unlikely these will reach the level of OOB reads.”
Gorenc noted that ZDI doesn’t typically take on reports for many commonly exploited vulnerabilities, like cross-site scripting (XSS), DLL planting, vulnerabilities in live websites or online tools, or ActiveX bugs. Thus, this snapshot of the group’s bounty activity gives an incomplete picture of the threat landscape as a whole.
Meanwhile, it’s likely that the number of advisories stemming from 2019 bug discoveries will grow: “We usually see notifications from vendors early in the new year of vulnerabilities patched late in the previous year (but where advisories were not coordinated),” said Gorenc. “Because of this, the actual number of 2019 advisories will eventually increase.”
The ZDI bug-bounty report card comes on the heels of an update from Google, which said this week that it paid out $6.5 million in rewards in 2019.