Long thought dead, the peer-to-peer (P2P) ZeroAccess botnet has resurfaced, and as of just a few weeks ago, has returned to propagating click-fraud scams.
Researchers with Dell’s SecureWorks revealed Wednesday that they witnessed the botnet restart itself from March 21 to July 2, 2014 and that halfway through this month – six months after it was last seen – the botnet has apparently gone back to its old ways and is again doling out click-fraud templates.
Click-fraud, one of the easier techniques cybercriminals use to monetize malware, is essentially the embezzling of ad revenue from clicks that don’t come from legitimate customers.
Despite the botnet’s resurfacing, researchers insist it hasn’t grown or even tried to incorporate new compromises. Instead the botnet, which has split into two smaller botnets that use different UDP ports, is built around hosts from past infections.
As seen below, researchers found ZeroAccess in two smaller botnets in both 32-bit (blue) and 64-bit (gray) compromised Windows systems.
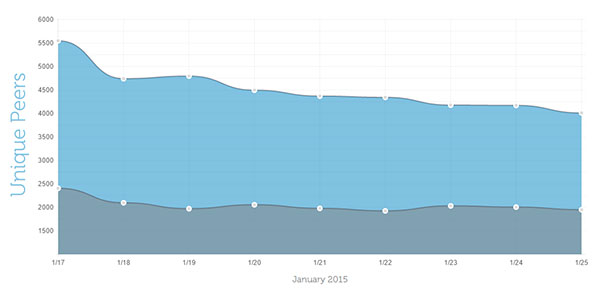
“Compromised systems act as nodes in the P2P network, and they periodically receive new templates that include URLs for attack-controlled template servers,” the firm’s Counter Threat Unit (CTU) wrote.
Once the URLs are visited, like a chain reaction, the bots are redirected to their final destination.
The unit claims it counted 55,000-plus different IP addresses – mostly in Japan, India and Russia – engaging with the botnet from Jan. 17 to Jan. 25. Some may consider 55K small potatoes compared to the botnet’s heyday, when Microsoft cleaned half a million machines of the virus from Feb. to March 2013, but Dell is stressing that for all intents and purposes ZeroAccess should still be considered substantial.
Adding that it may not be able to do what other flashy botnets can, like carry out banking fraud or hold users’ files ransom, ZeroAccess can still wreak havoc on advertisers and machines it infects alike.
It was thought the botnet was dead in December 2013 after Microsoft, along with Europol’s European Cybercrime Centre (EC3), the F.B.I., and the firm A10 disrupted ZeroAccess’s two million odd machines. Click-fraud is just one of the botnet’s favorite pastimes. ZeroAccess, a/k/a Sirefef, has also been seen hijacking search results and redirecting victims to malicious, information stealing websites and for a short stint the platform was even spotted facilitating Bitcoin mining.
Microsoft greatly curbed the botnet’s click-fraud tendencies in May 2013 after it added its signature to its Malicious Software Removal Tool (MSRT) and cleaned all the infected machines it could find of ZeroAccess.










