 The authors of the Zeus bot client, perhaps the most popular and pervasive piece of malware of its kind right now, have taken an extraordinary step to protect their creation: inserting a hardware-based licensing scheme into the Trojan. This represents a significant leap in the sophistication and professionalism of malware development, researchers say.
The authors of the Zeus bot client, perhaps the most popular and pervasive piece of malware of its kind right now, have taken an extraordinary step to protect their creation: inserting a hardware-based licensing scheme into the Trojan. This represents a significant leap in the sophistication and professionalism of malware development, researchers say.
Zeus has been making the rounds on the Web for some time now, and it has gone through a number of revisions and upgrades in recent months. Its creators, who remain unknown, have steadily added more and more features and functionality to the package, including a form grabber for Firefox, the ability to add extra data fields to online banking applications, a backconnect module and support for Windows Vista and Windows 7.
Much of this is fairly standard stuff, but the addition of the hardware licensing/activation scheme is an interesting, unique twist. Researchers at SecureWorks have been analyzing each new iteration of the Zeus kit and found that the latest release, version 1.3.4.x, added this functionality, likely in an effort to prevent rivals from selling pirated versions of the attack kit.
“The author has gone to great lengths to protect this version using a
Hardware-based Licensing System. The author of Zeus has created a
hardware-based licensing system for the Zeus Builder kit that you can
only run on one computer. Once you run it, you get a code from the
specific computer, and then the author gives you a key just for that
computer. This is the first time we have seen this level of control
for malware.,” Kevin Stevens and Don Jackson of SecureWorks wrote.
The newest release of Zeus is selling for $3,000 to $4,000 right now in private sales, the researchers said, and is being sold solely by the kit’s author. Other, older versions have been sold publicly in the past, which likely led to the author taking the step of using the hardware licensing system to protect his creation.
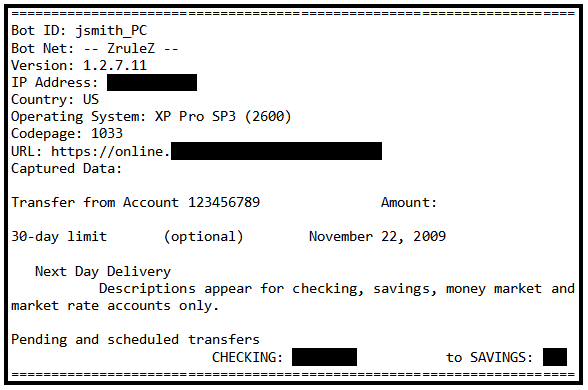
While Zeus includes a wide range of capabilities now, its basic reason for being is to steal financial data. Think of it as a banker Trojan on steroids, the 2007 David Ortiz of malware. As the SecureWorks researchers found, Zeus does much of its dirty work through secure HTTP POST requests to the remote command-and-control server. It targets a broad spectrum of financial data, including credit card numbers, bank account numbers and online banking login credentials.
Stevens and Jackson said that the Zeus author is working on version 1.4 of the kit, which will include a polymorphic encryption feature.
“The 1.4 version of ZeuS will enable the ZeuS Trojan to re-encrypt
itself each time it infects a victim, thus making each infection
unique. The 1.4 version also enables the ZeuS file names to be
randomly generated, thus each infection will contain different
file names. This will make it very difficult for anti-virus
engines to identify the ZeuS Banking Trojan on the victims’
system,” they said.









