Cybercriminals are taking advantage of the massive uptick in unemployment across the U.S. in a recent spear-phishing campaign, which purports to be CVs sent from job-seekers – but actually spreads banking credential-stealing malware.
Researchers recently uncovered emails that distributed malicious files masquerading as resumes and CVs. The files, attached in Microsoft Excel format, were sent via email with subject lines such as: “applying for a job” or “regarding job.” As victims opened the attached files, they were asked to “enable content.”
After enabling, victims were given the infamous ZLoader malware, which has previously been distributed via spear-phishing campaigns taking advantage of the coronavirus pandemic. ZLoader is a banking malware designed to steal credentials and other private information from users of targeted financial institutions. The malware can also steal passwords and cookies stored in victim’s web browsers.
“With the stolen information in hand, the malware can allow threat actors to connect to the victim’s system and make illicit financial transactions from the banking user’s legitimate device,” said Check Point researchers, in a Thursday post.
This campaign is only the latest targeting those who have lost jobs, particularly as unemployment rates are soaring across the U.S., with more than 40 million Americans filing for first-time unemployment benefits at the end of May.
 Other campaigns were also discovered, including one that used medical-leave forms to deliver the IcedID malware. In this campaign, malicious documents were sent with names like “COVID -19 FLMA CENTER.doc” in emails with subjects such as “The following is a new Employee Request Form for leave within the Family and Medical Leave Act (FMLA).”
Other campaigns were also discovered, including one that used medical-leave forms to deliver the IcedID malware. In this campaign, malicious documents were sent with names like “COVID -19 FLMA CENTER.doc” in emails with subjects such as “The following is a new Employee Request Form for leave within the Family and Medical Leave Act (FMLA).”
The malware used redirection attacks that leveraged local proxies to redirect victims to malicious websites, as well as web-injection attacks that present fake content overlaid on the original pages. Either way, ultimately, the IcedID trojan was downloaded to steal victims’ financial data.
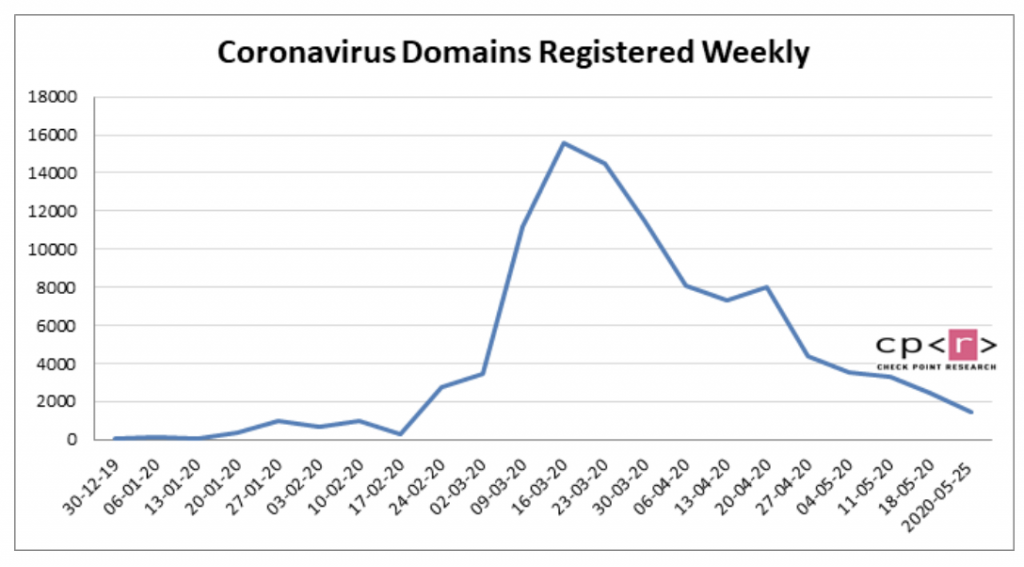
Overall, researchers noted that they have seen new malicious domains popping up in conjunction with these unemployment numbers: “We previously reported that because of high unemployment rates, people became vulnerable to scams and phishing attacks involving relief package payments,” said researchers. “We found that in May, 250 new domains containing the word ’employment’ were registered. 7 percent of these domains were malicious and another 9 percent suspicious.”
Campaigns are continually taking advantage of the unemployment surge in the U.S. A few weeks ago, infamous business email compromise (BEC) group called Scattered Canary (a highly-organized Nigerian cybergang) was discovered to have submitted hundreds of fraudulent claims with state-level U.S. unemployment websites and coronavirus relief funds. Researchers who tracked the fraudulent activity said cybercriminals may have made millions so far from the fraudulent activity. Since April 29, Scattered Canary has filed more than 200 fraudulent claims on the online unemployment websites of eight U.S. states; including at least 174 fraudulent claims with the state of Washington, for instance, and at least 17 fraudulent claims with the state of Massachusetts, they said.
Concerned about the IoT security challenges businesses face as more connected devices run our enterprises, drive our manufacturing lines, track and deliver healthcare to patients, and more? On June 3 at 2 p.m. ET, join renowned security technologist Bruce Schneier, Armis CISO Curtis Simpson and Threatpost for a FREE webinar, Taming the Unmanaged and IoT Device Tsunami. Get exclusive insights on how to manage this new and growing attack surface. Please register here for this sponsored webinar.