The New York attorney general, Letitia James, is demanding more information about how Zoom secures user data. The inquiry comes amidst mounting public scrutiny of the web conferencing platform’s data privacy and security policies.
In a Monday letter, James questioned whether Zoom’s security protections can keep up with the spike in users, with more employees working from home over the past few weeks due to the coronavirus pandemic. Almost 600,000 people downloaded the Zoom app on March 15, after social distancing orders were put in place, for instance.
“While Zoom has remediated specific reported security vulnerabilities, we would like to understand whether Zoom has undertaken a broader review of its security practices,” according to the letter obtained by the New York Times.
The potential security issues that Zoom’s facing are myriad. Already, numerous reports have emerged of threat actors hijacking Zoom meetings and upending them with hate speech, threats of sexual harassment, and pornographic images. Some of the attacks have even go so far as to threaten those attending the meeting with physical harm.
Our video call was just attacked by someone who kept sharing pornography + switching between different user accounts so we could not block them. Stay tuned for next steps. And I am sorry to everyone who experienced. We shut down as soon as we could.
— Jessica Lessin (@Jessicalessin) March 20, 2020
Zoom meetings have an option to be password protected, but there’s still ways attackers could bypass that. Check Point Research on Monday pointed to cybercriminals setting up fake Zoom domains and then persuading victims to enter their account credentials into that domain. The credentials could then be used to snoop in on conference meetings.
Since the start of 2020, more than 1,700 new fake Zoom domains were registered – and 25 percent of them were registered in the past week, the researchers said: “During the past few weeks, we have witnessed a major increase in new domain registrations with names including ‘Zoom,’ which is one of the most common video communication platforms used around the world.”
Privacy Concerns
Behind these real-world attacks, Zoom’s policies for collecting, sharing and securing data are coming under criticism. A report from The Intercept, released Tuesday, questioned Zoom’s claims that the platform uses end-to-end encryption. The report said that Zoom’s platform actually uses transport layer security (TLS) encryption, which provides encryption between individual users and service providers instead of encrypting communication directly between the users of a system.
Zoom this week also removed a feature in its iOS web conferencing app that was sharing analytics data with Facebook, after a report revealing the practice sparked outrage. According to the Motherboard report last week that originally disclosed the privacy issue, the transferred information included data on when a user opened the app, a user’s time zone, device OS, device model and carrier, screen size, processor cores and disk space.
Zoom’s privacy policy did not clearly outline that it was transferring the data to Facebook. The web conferencing platform’s policy (which has been updated as of Sunday, March 29) initially stated: “Our third-party service providers, and advertising partners (e.g., Google Ads and Google Analytics) automatically collect some information about you when you use our Products,” without giving further information about data being shared with Facebook.
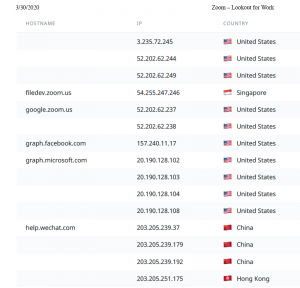
Chris Hazelton, director of security solutions at Lookout, told Threatpost that Lookout researchers analyzed Zoom’s most recent iOS version (4.6.9) as of Monday morning, and confirmed they are still communicating with Facebook APIs in the current iOS version of the Zoom app (see image to the left). However, that doesn’t indicate that the data-sharing feature hasn’t been killed, Hazelton said, “only that the app is still communicating with Facebook.”
“Zoom did update their app with version 4.6.9, which was updated to three days ago for ‘Improvements to Facebook Login,'” Hazelton told Threatpost. “The app communicates with IPs in the US, China, India, and Germany. This is to leverage APIs from Alibaba, Box, Dropbox, Facebook, Google, Microsoft, Ringcentral, WeChat and QQ.”
In response to these concerns James’ letter requested an outline of the different categories of data that Zoom collects, the purpose of collecting this data, and entities to whom Zoom provides this user data, according to the New York Times article.
The letter also inquired about Zoom’s strategy for obtaining consent in collecting data related to children, with more school systems turning to the web conferencing platform for online coursework. A spokesperson for the AG’s office confirmed to Threatpost that the office sent a letter to Zoom with a number of questions regarding how the company is taking appropriate steps to ensure users’ privacy and security.
Zoom for its part told Threatpost that it “takes its users’ privacy, security, and trust extremely seriously.”
“During the COVID-19 pandemic, we are working around-the-clock to ensure that hospitals, universities, schools, and other businesses across the world can stay connected and operational,” a spokesperson told Threatpost. “We appreciate the New York Attorney General’s engagement on these issues and are happy to provide her with the requested information.”
Security Measures
In the meantime, Zoom users can make sure they’re taking extra security precautions by always setting a password for their meetings. This “adds a randomly generated password that invitees will need to input,” according to Tony Anscombe with ESET on Tuesday. “A numerical password can be used to authenticate users who connect by phone. Do not embed the password in the meeting link.”
He added, “most videoconferencing platforms allow for the creation of groups of users or the ability to restrict access by internet domain so only users with an email address from your company would be able to join the call. Alternatively, only allow attendees that are invited by adding their email addresses to the invite when scheduling the call.”
Check Point researchers also say, users should be on the lookout for lookalike Zoom domains, spelling errors in emails and websites, and unfamiliar email senders.
Zoom had security issues long before the platform’s spike in popularity. In January, researchers said Zoom used weak authentication that made it possible for adversaries to join active meetings, for instance.
Do you suffer from Password Fatigue? On Wednesday April 8 at 2 p.m. ET join Duo Security and Threatpost as we explore a passwordless future. This FREE webinar maps out a future where modern authentication standards like WebAuthn significantly reduce a dependency on passwords. We’ll also explore how teaming with Microsoft can reduced reliance on passwords. Please register here and dare to ask, “Are passwords overrated?” in this sponsored webinar.











