Most of us—hopefully—awaken every day, shower and brush our teeth. If you own a home, you patch a leaky roof and paint the shutters so they don’t rot. You own a vehicle, you change the oil when you’re supposed to and make sure the brakes work the way they’re supposed to.
It’s simple hygiene.
Yet we don’t practice what we preach with computer systems—and we’re not breaking any news here. We manage computers whose job it is to keep our bank accounts safe whose patch levels are woefully out of date. We run computers whose job it is to keep the lights on and the water running, and those are exposed to the Internet, guarded only with a pitiful default password.
It’s 2014, more than a decade after Code Red, Slammer and NIMDA, and we’re still talking about hygiene.
The 2014 Verizon Data Breach Investigations Report (DBIR) emerged in the early hours of this morning, chock full of the usual: Deep numbers on data breaches, how they impact certain platforms or industries more than others, and why we’re falling down hard against things such as point-of-sale hacks, cyberespionage, DDoS, ATM skimmers and more.
And the answers and insight generally track back to hygiene.
“A lot of it is basic security hygiene: blocking and tackling that’s not occurring that should prevent organizations from being victims of opportunistic attacks,” said Marc Spitler, one of the authors of the DBIR. “Hackers are not targeting organizations because of who the organization is, but because they realized it had a vulnerable version of particular software that was worth exploiting to see what happens from there.”
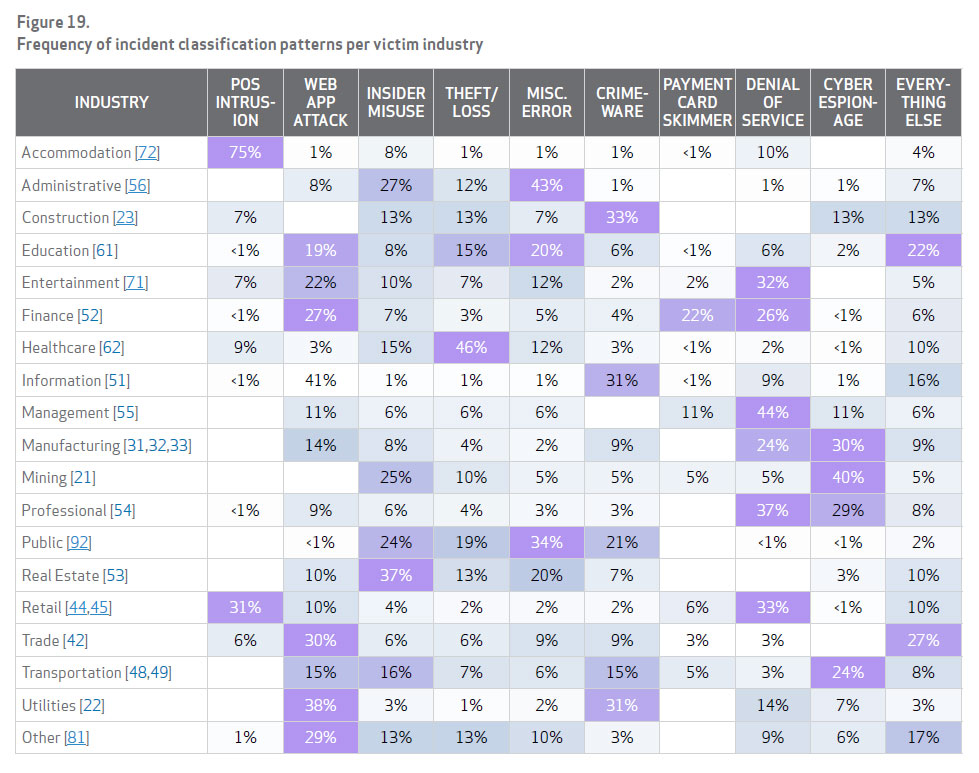
Verizon’s annual report (PDF) is a useful snapshot of data breach characteristics. The data comes from breaches and incidents investigated by Verizon and from law enforcement and private sector contributors to the report. This year, users are able to more easily consume the volumes of data compiled from more than 1,300 breaches and 65,000 incidents because Verizon has found nine attack patterns common to breaches across the board in order to better parse out the data.
Within each pattern, readers will find the top malware and hacking vectors attackers are exploiting, as well as other important statistics such as time to discovery and remediation, as well as recommended controls.
Almost without fail, each of the recommended controls concentrate on authentication issues such as stronger passwords, two-factor authentication, encryption of PIN data and understanding the privileges associated with identities and users. Not to mention more than one recommendation for updating antimalware protection regularly, as well maintaining proper patch levels.
“One recommendation we repeat is the implementation of two-factor authentication because credentials are such a sought-after data variety,” Verizon’s Spitler said. “Whether you’re a financially motivated hacker using it to get into a point-of-sale device, or a state-sponsored unit looking for intellectual property, you rely on legitimate credentials to move laterally and deeper into the network and do it under the radar in a non-noisy fashion where you’re not going to light up IDS and audit logs.”
The use of stolen credentials, for example, was the top threat action identified by this year’s DBIR; 422 incidents involved the use of a stolen password, ahead of data exfiltration, RAM scraper malware, backdoors and even phishing attacks. It was a plague in attacks where financial fraud was carried out using crimeware such as Zeus. Credentials were the top at-risk data type in breaches where crimeware was used, and in web application attacks where attackers were guessing credentials to access management panels.
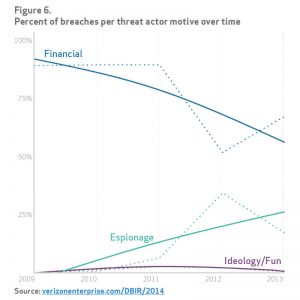
A lack of basic security hygiene can also affect national security or the security of critical services such as those provided by utilities. Cyberespionage campaigns, for example, are just as reliant on weak credentials, poor configurations and out-of-date patch levels as cybercriminals. Verizon, for example, laid out a plethora of controls to counter cyberespionage that could be the first few chapters of a resource guide on security hygiene: updated antimalware; network segmentation; log monitoring; user awareness; patching; and strong authentication. All of which prevent state-sponsored hackers from gaining an initial foothold inside a corporate network, but also prevent lateral movement once in, putting other resources at risk.