The attention given to the Target data breach elevated concerns about point-of-sale hacks and got us reacquainted with RAM scrapers and other threats to retailers big and small. And while it’s been a noteworthy highlight to the annual Verizon Data Breach Investigations Report for the past few years, the data in this year’s report indicates the trend is reversing course.
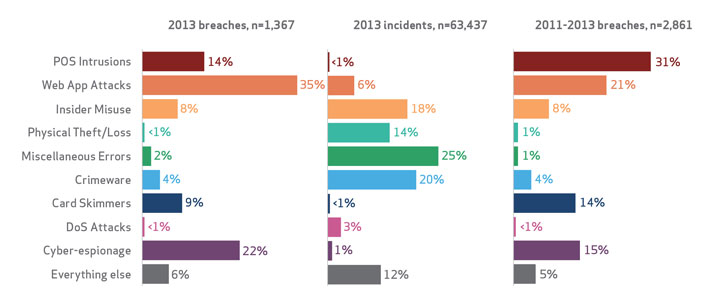
The DBIR, which was released today, points out that point-of-sale intrusions were a declining threat among the 1,367 breach investigations conducted by Verizon and data submitted by 50 global law enforcement and private organizations. While retailers and small enterprises were still a prime target for cybercrime, point-of-sale attacks accounted for 14 percent of the breaches in the report, down from a high of more than 30 percent in 2011 and 2012. Web application attacks and cyberespionage, meanwhile, spiked where point-of-sale attacks dipped.
The Target breach was massive with hackers breaching point-of-sale systems with malware that stole credit card data from memory on the devices before it was encrypted. More than 40 million cards were stolen, along with personal records of 70 million individuals, elevating it to one of the biggest breaches in U.S. history. Yet the total number of breaches and incidents related to POS devices is down to 198 incidents in 2013.
“When we had big spikes like those in 2011 when they were at their highest, we would see sprees where one criminal group was attributed to 50 to 100 victims,” said Marc Spitler, Verizon senior analyst and DBIR co-author. “Criminals would cast a net and script something that finds POS servers with weak credentials, and install malware and away they would go. We called it the industrialization of cybercrime and financially motivated cybercrime.”
The data in the Verizon DBIR, now in its eighth year, is one of the most-cited annual snapshots of data breach information and gives the industry a benchmark of breach characteristics and trends. This year’s report has a markedly different look to it. Rather than be organized solely by threat actions, actors, compromised assets and more, this year’s report is broken up by nine characteristic attack patterns common to breaches across the board. The nine patterns include: point-of-sale intrusions; web application attacks; insider misuse; physical theft or loss; crimeware; card skimmers; denial-of-service attacks; cyberespionage; miscellaneous errors; and everything else.
Within each pattern, Verizon identifies trends, percentages against industry and new tactics employed by hackers. It also suggests recommended controls for each attack pattern.
“We structured the report in this manner to give people information about these attack classification patterns, take a look at them and tell how often the patterns are present in your industry,” Spitler said. “We were able to take that information and present it in a way that’s easier to analyze and make more actionable. Readers asked how we could make this more actionable. They like the report and there’s good information, but want it to be more concrete, and be able to take the information in and do things with it.”
For the first time there is data on distributed denial of service attacks for example which plagued the banking industry and other high-profile targets throughout 2013. There’s also significant data on cyberespionage attacks most of which are perpetrated by nation states for the purposes of industrial espionage and intellectual property theft.
Big picture, Verizon concludes that attackers are widening the gap in time between the time it takes to compromise an asset and the time to discover and remediate a breach. Attackers, the report says, are getting faster at breaching vulnerable assets at a higher rate than which defenders are remediating. External sources, meanwhile, are still the primary means of breach discovery, the report said, but the trend is improving with internal detections for the first time outnumbering external fraud detection. Still, many breaches are first reported by law enforcement or another third party such as a researcher.
“There was a slight gain in time to discovery, but at the same time, the gap is increasing [compared to time to compromise],” Spitler said. “We’d like to see it flipped and notice incidents before compromises. This is the way it’s looking and the way it’s looked the last 10 years. We need to do a better job.”
The spate of watering-hole attacks early in 2013 against government and high-value government targets drove the number of Web application attacks skyward, Verizon said. The DBIR noted close to 4,000 incidents, many of which capitalizing on shoddy credentials guarding content management systems such as WordPress. Many of these attacks overlapped with hacktivism and cyberespionage incidents, 511 of which were investigated by Verizon last year most of those in the public and manufacturing sectors.
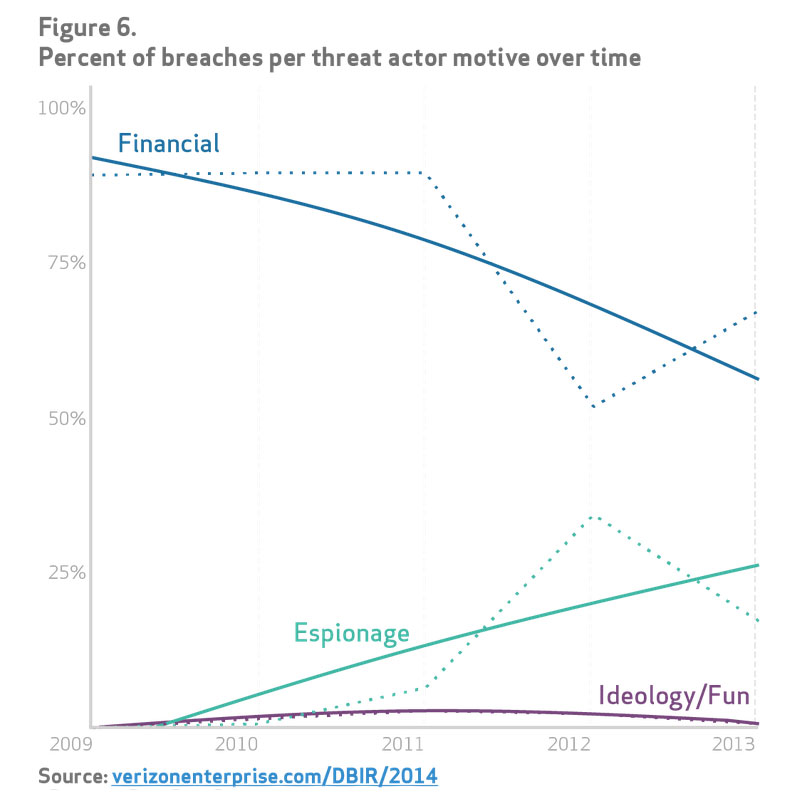
“For the first time, a significant number of breaches had espionage as a motive,” Spitler said. “We had a groundswell of contributors bolster that data set.”
And while targeted attacks and espionage get splash headlines, the most serious financial damage is still happening with breaches at small retailers, hotels and restaurant chains. Attackers are remotely hitting these organizations by compromising an Internet-facing remote desktop management or desktop sharing interface guarded by a weak or default password. RAM scraping malware generally does the job of stealing payment card data from memory before it is encrypted and sent to a payment processor. RAM scrapers were seen in 85 percent of POS intrusions, Verizon said. Data was stolen in 79 percent of breaches, usually card data sent to a third party.
RAM scrapers were the big culprit in the Target breach and have caught and passed keyloggers as the most common malware associated with POS intrusions, Verizon said. Compromises take seconds or minutes (87 percent combined) to happen in POS attacks, with exfiltration happening within minutes of a compromise in 88 percent of breaches. Attackers, meanwhile, have free reign for weeks, in 85 percent of breaches before they are discovered.
While the overall number of POS intrusions may be down, they’re still costing organizations tens of millions of dollars in recovery costs that include not only patching and new infrastructure, but breach notification costs and credit protection for victims.
“We don’t know if during the last two years if they’ve over-fished the waters,” Spitler said. “We are starting to see a decline in vulnerable POS systems out there. I’m hoping that what we’re doing in these reports is filtering down to smaller businesses. We’re still trying to get the word out there that these organizations should not have remote access points open to the Internet combined with a truly horrible password. I hope they can raise the bar high enough to where they’re not victims to an automated attack.”