Google said more than half of Android devices haven’t received a security update in the past year, and the percentage of potentially harmful apps running on devices installed from all sources rose in 2016.
The numbers come from the Android Security 2016 Year In Review (PDF) released Wednesday. While the reports touts security gains made over the last year, it also highlights areas where security is lacking.
By Q4 2016, Google said half of all Android devices in use at the end of 2016 had not received a platform security update in the previous year. This past year was the first full year of Google’s monthly patches.
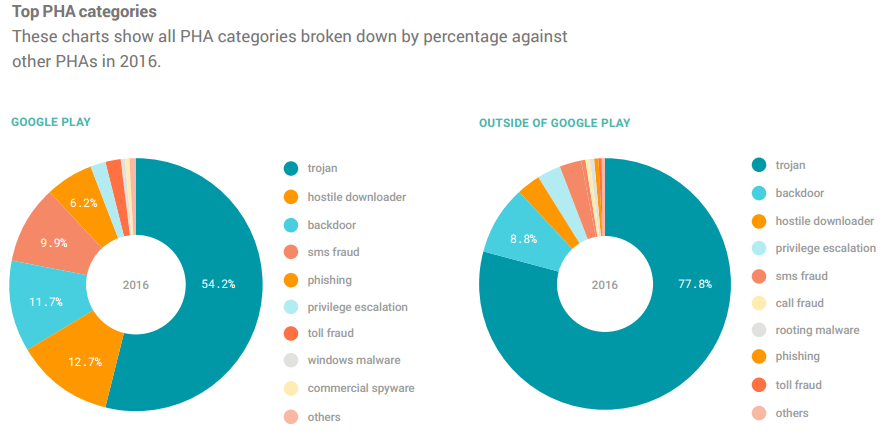
Google said overall the number of potentially harmful apps (PHA) downloaded from Google Play and including third-party apps stores running on Android devices rose to 0.71 percent in 2016, up from 0.5 percent in 2015 (PDF).
“Still, there’s more work to do for devices overall, especially those that install apps from multiple sources,” wrote co-authors of the report Adrian Ludwig, Google’s Director of Android Security, and Mel Miller, an Android security team member. “Using improved tools and the knowledge we gained in 2016, we think we can reduce the number of devices affected by PHAs in 2017, no matter where people get their apps.”
On a positive note, in 2016 Google reported, on average, devices that only installed applications from Google Play had less than 0.05 percent of PHAs installed. In 2015, that number was 0.15 percent.
Google said, during the past year it managed the security of 1.4 billion Android user devices. In that timeframe, Google touted its work with wireless carriers, system on chip manufacturers and device makers to release security patches at a faster pace.
“Several manufacturers, including Samsung, LG and OnePlus, regularly deliver security updates to flagship devices on the same day as Google’s updates to Nexus and Pixel devices, thereby providing their customers with the most up-to-date security available,” according to Google.
Still, over the past year, security experts pointed to device patching as a major issue for Google in 2016 and the year ahead. This past August, Google’s patching of the high-profile QuadRooter vulnerability took 96 days for it to go from vulnerability notification by Qualcomm to the release of the final patch for the critical flaws on Sept. 6.
Rich Smith, director of research and development for Duo Labs, blames carriers and manufacturers for hurting Google’s ability to speedily deploy patches. “(They) are doing a much worse job and acting as a drag factor on the overall Android ecosystem when it comes to timely patching,” he said.
By Q4 2016, more than half of the top 50 Android devices worldwide had a “recent” security patch, Google said. Smith points out that “recent” is a relative term. “Our analysis suggests that ‘recent’ looks to be about 90 days,” he said.
Duo Labs analysis of one million enterprise Android devices shows 65 percent of Google’s own Nexus and Pixel hardware receive security patches within a 60-day window of being released. And that 36 percent of what Google classifies as “top 50” Android devices receive a security patch within the first 60 days of availability. After three months, 90 percent of Google’s own devices had patches compared to 81 percent of other “top 50” Android devices, according to Duo Labs.
“That number is pretty impressive when you consider the fact that devices that aren’t part of the Nexus or Pixel family are at the mercy of their OEM or carrier as to when (or if) they would receive these updates,” Smith said.
Mediaserver, Google noted in its report, also received a big update in 2016. It was Android’s mediaserver, coupled with a security hole in Qualcomm’s Secure Execution Environment, which exposed 60 percent of Android devices to attack in 2016 as part of the QuadRooter vulnerability.
“We re-architected the mediaserver stack to address Stagefright-type vulnerabilities by adding integer overflow protections and compartmentalizing mediaserver’s components into individual sandboxes with minimal privileges. We also increased the degree of randomness in address space layout randomization (ASLR), making some attacks more difficult,” Google said.
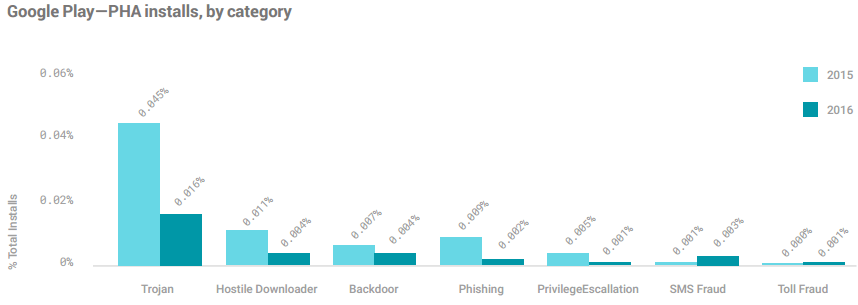
“The overall health of Google Play has increased year over year. The number of installed trojans dropped by 51.5 percent, hostile downloaders dropped by 54.6 percent, backdoors dropped by 30.5 percent, and phishing apps dropped by 73 percent,” wrote Ludwig and Miller.