This week’s patch and security advisory for a vulnerability in Microsoft Office is the perfect example of why enterprise administrators need to take Microsoft’s criticality ratings as a suggestion and not gospel.
Microsoft pushed security update MS13-051 through on Tuesday with a rating of Important, despite the fact that exploits have been in the wild and the vulnerability is previously unreported – a zero day. Microsoft’s reasoning is that significant user interaction is required to trigger the exploit, and that for now, the targeted attacks seem limited to Southeast Asia.
The vulnerability primarily affects Office 2003—Microsoft has not provided mainstream support for the productivity application suite since 2009; extended support ends next year. Office 2011 for Mac is also vulnerable, while newer versions for Windows are not.
“Microsoft rates it only as ‘Important’ because user interaction is required, but attackers have shown over and over that getting a user to open a file is quite straightforward,” said Wolfgang Kandek, CTO of Qualys. “They use social engineering techniques and send the ‘right’ content to the user under attack—documents that have professional names and contain information that is of interest to the target.”
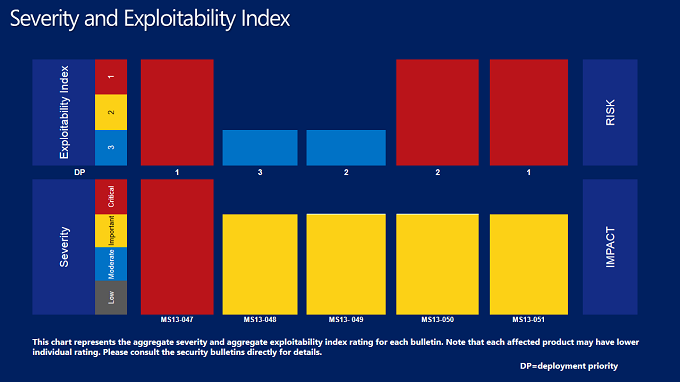
Microsoft released five bulletins as part of its June 2013 Patch Tuesday security updates. Aside from a cumulative update for Internet Explorer, the Office patch had the highest risk on Microsoft’s exploitability index and shared the highest deployment priority.
Microsoft has released additional information on the Office vulnerability, which is described in CVE-2013-1331. The problem lies in the way Office handles PNG files; the length field of a chunk is not correctly checked, Microsoft said. The parsing code does not catch the value of a field when it exceeds an allowed number of bytes as per the W3c specification, Microsoft said, leading to a buffer overflow and remote code execution.
“Shellcode analysis shows that the exploit for this vulnerability was a classic stack based buffer overflow, which wrote far past the end of a buffer on the stack, thereby overwriting control data on the program’s stack, eventually leading to hijacking the program’s execution,” wrote Neil Sikka, a Microsoft Security Response Center engineer.
Newer versions of Office, as well as Microsoft’s EMET 3.0 tool, will mitigate the issue, Microsoft said.
“The attacks we observed were extremely targeted in nature and were designed to avoid being investigated by security researchers,” Sikka said.
Researcher Eric Romang said the malicious PNG files and the zero day have been in the wild since February. He found one sample targeting victims in Vietnam with a Word document holding information about a territory conflict between China and the Philippines. Romang and Microsoft said the malicious PNG files used in the exploits are not embedded in the Office docs, but instead reference a file loaded from a remote server hosted on a number of different domains.
“Attackers also equipped their servers with scripts which avoid serving the PNG exploit multiple times, in an effort to keep this 0day more concealed,” Sikka said. “We believe that the limited attacks observed were geographically located mostly in Indonesia and Malaysia.”
Romang looked at three of the malicious domains. One, intent[.]nofrillsspace[.]com is a free Web host that was still operational as of May 28. Romang said the domain’s IP address was hosted in the Russian Federation and has been associated with a number of previous attacks; he also found a Google cache of an Excel document mentioning this domain. A second similar domain, mister[.]nofrillsspace[.]com has not been available since May 27.
The document targeting victims in Vietnam was found on the bridginglinks[.]com domain, another free Web host located in the Netherlands, he said. Malicious activity was detected on April 4 by urlQuery and March 3 by Joe Sandbox, Romang said, the latter being one of the Vietnamese Word documents which had a creation date of Feb. 25 and a document named “VN học gì từ vụ Philippines kiện TQ“
Image from Eric Romang’s blog.