A glut of WordPress sites have fallen victim to both malware infections and a series of brute force attacks that have been making the rounds over the past several days, researchers claim.
According to Peter Gramantik, a malware researcher at Sucuri, highly obfuscated malware payloads have been targeting sites with out of date plugins and sloppy, weak passwords.
While the fact that malware is targeting outdated plugins and weak passwords isn’t particularly surprising, Gramantik claims what makes the attack interesting is the fact that the payload is being blindly injected. Bug-riddled PHP is apparently corrupting legitimate WordPress files, along with theme and plugin files that belong to the popular content management system.
The errors are prompting a series of PHP warnings, like the one below, which pop up in normal site content according to the firm.
Parse error: syntax error, unexpected ‘)’ in /home/user/public_html/site/wp-config.php on line 91
Sucuri claims the only way it knows how to fix the infected files is to restore the files from backup after the malware has been removed.
This week has also seen a series of brute force attacks wreaking havoc on WordPress sites, according to researchers at the SANS Institute.
The attacks appear to target XMLRPC.php, the same PHP library that was leveraged to cause a large-scale distributed denial of service attack on tens of thousands of WordPress sites earlier this year.
SANS incident handler Daniel Wesemann warned Tuesday that some Internet Storm Center readers have been experiencing a scourge of attacks on their sites.
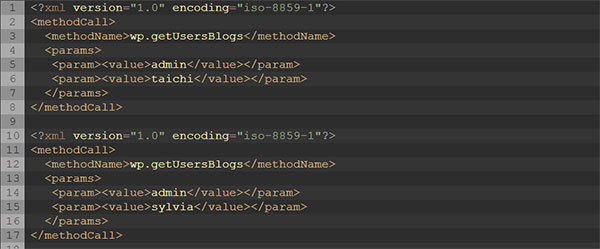
The attacks specifically use the wp.getUsersBlogs function of XMLRPC to send out brute force password guessing attacks. Code posted by Wesemann on the InfoSec Handlers Diary Blog clearly shows requests trying to guess passwords (admin, admin123) on a targeted WordPress installation.
(Image via Robert Paprocki, cryptobells.com)
Weseman goes on to point out that looking at the simple HTTP web server logs isn’t the best indicator of these attacks as the requests are approved by the web server and the XML message that the server returns as a payload includes an anticipated ‘403 – Not Authorized’ message.
The post warns that using “traditional” modes of security protection, like the plugin BruteProtect, are actually less effective.
“Most of these add-ons tend to watch only wp_login.php and the associated wp_login_failed result, which does not trigger in the case of an XMLRPC login error.”
WordPress experts are encouraging users looking to avoid getting hit with brute force attacks like these to use a strong password, not to use a common username and follow the Hardening WordPress FAQ on WordPress.org.
Jan Reilink, a Netherlands-based system administrator, claimed he noticed a rash of HTTP POST requests using XMLRPC.PHP on WordPress earlier this month but it’s unclear if the requests he noticed, which came in the form of a much larger payload, are related to the XMLRPC.PHP DDoS attack Sucuri noticed in March.
The brute force attack campaign sounds similar to attacks initiated by the massive 90,000-strong WordPress botnet that reared its head last spring. Those attacks used a combination of “admin” as a user name, and a list of common passwords to break its way into systems.