TENERIFE, Spain–For more than 10 years, attackers have carried out a series of covert attacks on firms worldwide and capitalized on that connection by coercing the companies into a phony business relationship where they can further steal data.
Experts with Kaspersky Lab’s Global Research and Analysis Team, who today at the Kaspersky Lab Security Analyst Summit disclosed research on the group and the malware it spreads, say there’s enough evidence surrounding the attacks to suggest it’s the first ever Portuguese-speaking attack group.
According to GReAT Researchers Dmitry Bestuzhev, Juan Andres Guerrero-Saade, and Santiago Pontiroli, the commercial consortium behind the APT boutique predominately uses Brazilian-Portuguese language strings in its code and commands.
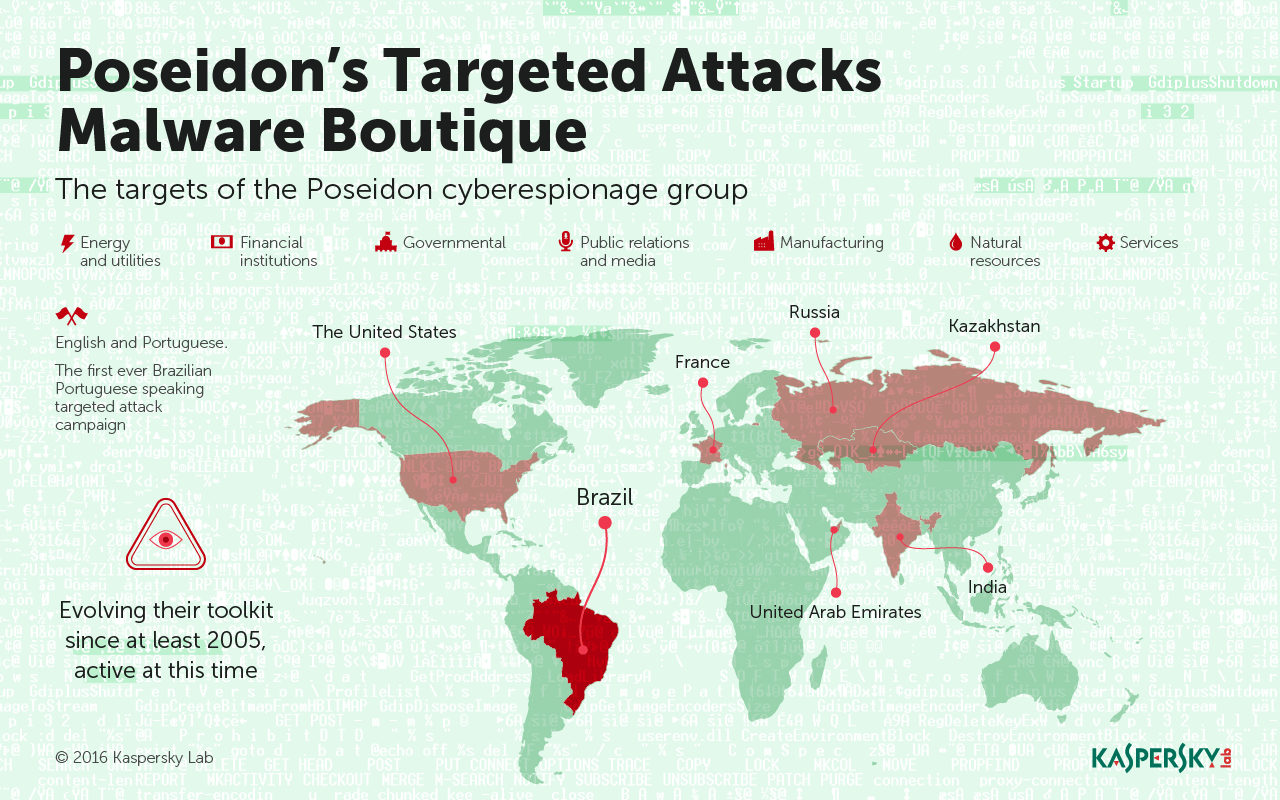
Despite being designed to function on English and Portuguese-language systems, the group still boasts a diverse number of targets, including firms and institutions from the United States, France, Kazakhstan, India, the United Arab Emirates, Russia, and Poseidon’s most favorite target, Brazil. According to Bestuzhev, the researchers discovered C&C servers in Brazil, USA, Greece, Colombia, and Venezuela.
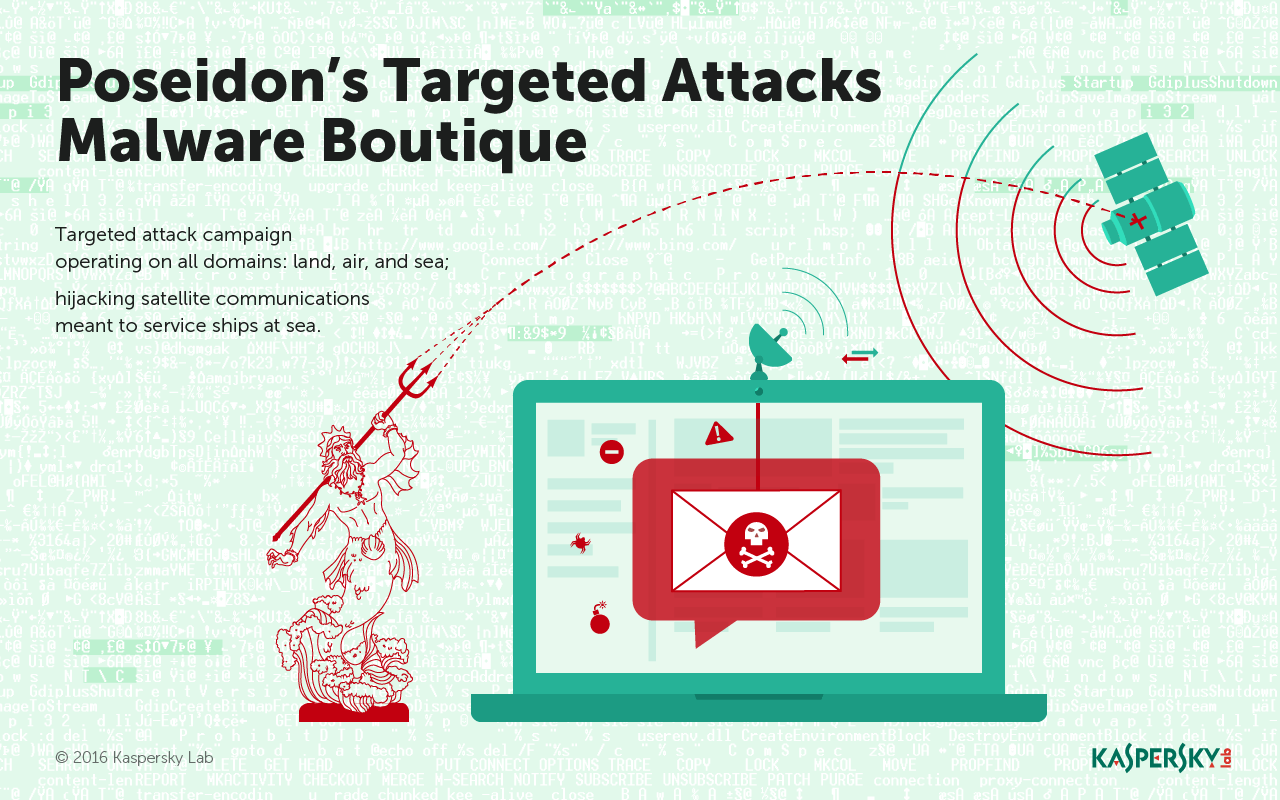
It starts off simply enough – the group collects information from firms conventionally by phishing them with malware-laden Microsoft Office documents. To hook victims, the documents usually have a human resources angle and come disguised as .RTF or .DOC files. Once inside, the Poseidon Group is able to enumerate all of the system’s processes and move laterally. By triggering a backdoor, it’s guaranteed a permanent remote connection.
That sensitive information is then lifted and used by an unnamed company to threaten the companies that were hacked to hire the Poseidon Group as a security firm – almost like a fake investment forecaster. Naturally, once the group is in, they’re in – and continues to monitor data .
The attackers are primarily focusing on stealing business-sensitive information, especially when it comes to technology, and pertains to investments, the researchers stress. That said, the attackers don’t discriminate – they’ve targeted a swathe of companies, 35 in total, including financial institutions, energy and utility firms, government entities, and even public relations and media outlets.
The malware uses digitally signed certificates, “often issued in the name of rogue and legitimate companies,” something that helps it avoid being detected, Bestuzhev, Guerrero-Saade, and Pontiroli said.
Its been a long haul for Poseidon. Some malware samples associated with the Poseidon Group actually date to 2005, but this is the first time that comprehensive information on the group has been pulled together.
Yet as any threat is wont to do when its operators oversee it for 10 years, the malware has matured over the years, first targeting Windows 95 systems and Windows NT, before moving onto Windows 2012 Server, and Windows 8.1.
The malware’s most cunning and recent addition has been an Information Gathering Tool (IGT) that carries out data theft, exfiltration, and then cleans up components, mostly when it comes to credentials that lie on the Domain or database server.
Researchers with the group insist on referring to Poseidon as an attack boutique, since the collective constantly shakes up its toolkit, customizing each build on a case-by-case basis for their clients.
The malware’s name stems from a handful of text fragments, the researchers discovered in the strings section of executable files. These text fragments suggest the group has an affinity for Poseidon, the God of the Seas, along with other Greek mythology terms.
It’s not the only connection Poseidon has to the sea. In one campaign, researchers claim Poseidon samples ultimately linked back to satellite uplink IP addresses, designed for communication with ships at sea.
“The networks abused were designed for internet communications with ships at sea which span a greater geographical area at nearly global scale, while providing nearly no security for their downlinks,” the trio wrote in a description of the APT published Tuesday.
More than 10 years later, the actors behind Poseidon remain active, researchers say. As the collective frequently tweaks their attacks, the group is in constant flux. It dumps C&C servers here and there but ultimately finds a new way to evolve, and persist, researchers claim.
“These people are very clearly paying attention to whats happening in the research industry,” Guerrero-Saade said in closing Tuesday.