Researchers say that 500 Google Chrome browser extensions were discovered secretly uploading private browsing data to attacker-controlled servers, and redirecting victims to malware-laced websites. The browser extensions, all of which have now been removed, were downloaded millions of times from Google’s Chrome Web Store.
Browser extensions are used for customizing web browsers, modifying user interfaces, blocking ads and managing cookies. But researchers said that the malicious extensions they discovered are instead part of a massive malvertising campaign that also harvested browser data. Malvertising often is used as a vehicle for fraudulent activity, including data exfiltration, phishing or ad fraud. In this particular instance, bad actors were redirecting victims from legitimate online ad streams to malware-laced pages.
“These extensions were commonly presented as offering advertising as a service,” according to Jamila Kaya, an independent security researcher, and Jacob Rickerd, with Duo Security, in a Thursday analysis. “[Security researcher Jamila Kaya] discovered they were part of a network of copycat plugins sharing nearly identical functionality. Through collaboration, we were able to take the few dozen extensions and… identify 70 matching their patterns across 1.7 million users and escalate concerns to Google.”
Researchers believe that the actor behind this campaign was active since January 2019, with activity escalating between March and June. After researchers first identified 71 malicious extensions and reported their findings to Google, the tech giant then identified 430 additional extensions that were also linked to the malvertising campaign, they said. The extensions had almost no ratings on Google’s Chrome Web Store, and the source code of the extensions are all nearly identical.
Once downloaded, the extensions would connect the browser clients to a command-and-control (C2) server and then exfiltrate private browsing data without the users’ knowledge, researchers said.
The extension would also redirect browsers to various domains with advertising streams. While a large portion of these ad streams were actually benign (leading to ads for Macy’s, Dell or Best Buy), these legitimate ad streams were coupled with malicious ad streams that redirected users to malware and phishing landing pages.
The campaign highlights various security issues that browser extensions can introduce, researchers said. In 2017, a malicious Google Chrome extension being spread in phishing emails stole any data posted online by victims. In 2018, four malicious extensions were discovered in the official Google Chrome Web Store with a combined user count of more than 500,000. And, in January, the Google Chrome and Mozilla Firefox teams cracked down on web browser extensions that stole user data and executed remote code, among other bad actions.
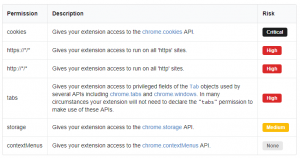
“Browser extensions are the Wild Wild West of the internet,” said Ameet Naik, security evangelist at PerimeterX, in an email. “There are approximately 200,000 extensions available on the Chrome store alone. What most users don’t realize is that extensions have full access to all of the data on a page including your email, banking information and credit card numbers. While many extensions provide value added services, there’s little to stop them from collecting and abusing user data.”
Google for its part has stepped up to the plate in its efforts to bar malicious extensions. The tech giant has implemented new user data privacy policy guidelines, requiring all extensions that handle user data to have a privacy policy, gain consent from the user, and only use the minimum required amount of permissions. Google has also implemented a program which will pay out bounties to researchers who find extensions that are violating this policy.
“We appreciate the work of the research community, and when we are alerted of extensions in the Web Store that violate our policies, we take action and use those incidents as training material to improve our automated and manual analyses,” said a Google spokesperson in a statement. “We do regular sweeps to find extensions using similar techniques, code, and behaviors, and take down those extensions if they violate our policies.”
Learn how Operational Technology and Information Technology systems are merging and changing security playbooks in this free Threatpost Webinar. Join us Wednesday, Feb. 19 at 2 p.m. ET when a panel of OT and IT security experts will discuss how this growing trend is shaping security approaches for IoT and 5G rollouts. This webinar is for security and DevOps engineers, IoT edge developers and security executives.